This blog explores the security features in TrueNAS SCALE, including the new features in Electric Eel (24.10), as well as the TrueSecure™ package, designed to meet stringent commercial and government security standards.
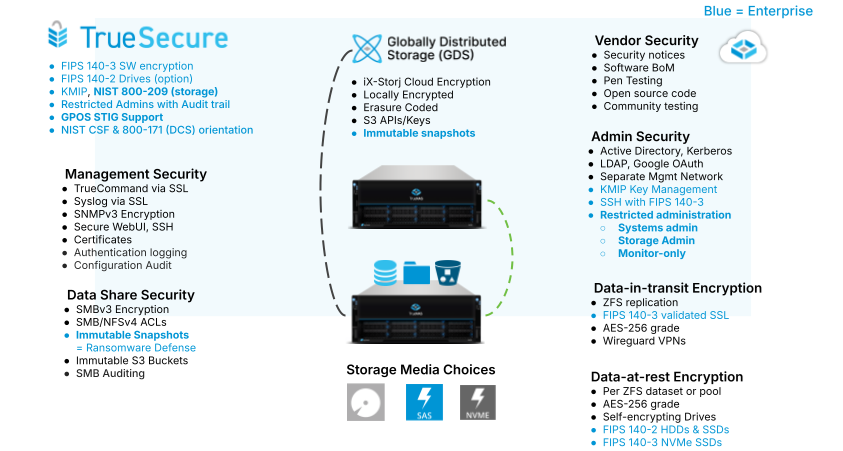
TrueSecureTM is an optional feature package for TrueNAS Enterprise that offers a robust set of enterprise-level software and hardware capabilities to meet high security and compliance standards.
The key features of TrueSecureTM include:
-
- FIPS 140-validated cryptographic modules for SSL-based encryption of data in transit
- FIPS 140-validated HDD and SSD media for encryption of data at rest
- KMIP for centralized management of encryption keys
- Optional restricted administration roles for limited access
- Immutable ZFS Snapshots to further enhance ransomware protection
- General Purpose OS STIG support and NIST 800-209 compliance to meet US federal requirements
With the optional TrueSecureTM feature package, TrueNAS complies with the requirements of the NIST Cybersecurity Framework to make Federal-level storage security as cost-effective as possible. With this foundation, TrueNAS can be used for federal government use cases from military bases to law enforcement and secure research organizations.
By default, TrueNAS includes a wide range of capabilities intended to simplify the delivery of secure storage infrastructure, including network encryption, access control, auditing, and logging functions.
Security notices (CVEs) and the Software Bill of Materials (SBoM) are available via the updated TrueNAS security site. For developers or those with an intimate knowledge of programming, the TrueNAS source code is available for review via GitHub. We believe that sunlight is one of the best disinfectants.
Secure for Enterprises
While some consumer storage vendors prioritize ease of use over security, exposing themselves to exploits that lead to virus or ransomware attacks, TrueNAS places security at the forefront. With built-in features that reduce attack vectors and restrict admin access, TrueNAS is designed to seamlessly integrate into secure network environments, providing enterprise-grade protection against evolving threats.
New threats come online with such frequency that new features and tools are always needed to stay ahead of the curve. In the last year, TrueNAS Enterprise has added a FIPS 140-2 validated crypto module and the option to enable Restricted Admins on Enterprise appliances. Let’s dive into Restricted Admins and then review the other key security features available in Electric Eel.
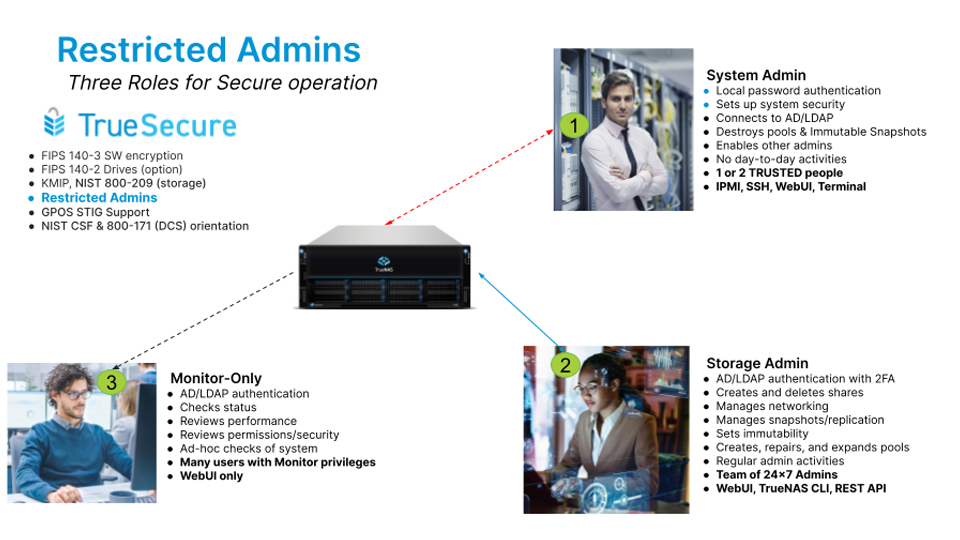
Restricted Admins
TrueNAS Enterprise 24.04 and later versions introduce three admin roles—System Admins, Storage Admins, and Monitor-Only Admins—to enhance security and limit access. This multi-level admin structure ensures that sensitive actions are restricted to authorized personnel, significantly reducing the risk of unauthorized data access or manipulation.
System Admins have the authority to set up the system, much like the original root user. They set up the system and its security posture, including connections to AD, LDAP, and KMIP and configuring any passwords required. However, once the system is set up, they then create storage admins to operate the system. They are needed to retire systems and delete pools or immutable snapshots. For security reasons, only a select few users should be made System Admins.
Storage Admins have the authority to create, configure, and delete shares and snapshots, and can also set immutability; however, they do not have the authority to destroy pools or immutable snapshots. There can be as many Storage Admins as needed.
Monitor-Only Admins have the authority to review configurations, performance, and check alerts, but can’t make changes to the system. They are often the storage users in the organization who can check that systems are supporting their applications. Where needed, they can request that a Storage Admin sign in to make approved changes.
Administrator roles are restricted regardless of the method of access, whether that be the WebUI, CLI, or API, with optional Two-Factor Authentication (2FA) used to secure interactive access.
TrueNAS Security Features
TrueNAS offers a comprehensive suite of security features, including encryption, access control, and logging, all designed to protect data integrity and compliance. These features ensure that TrueNAS remains a secure and reliable choice for organizations of any size.
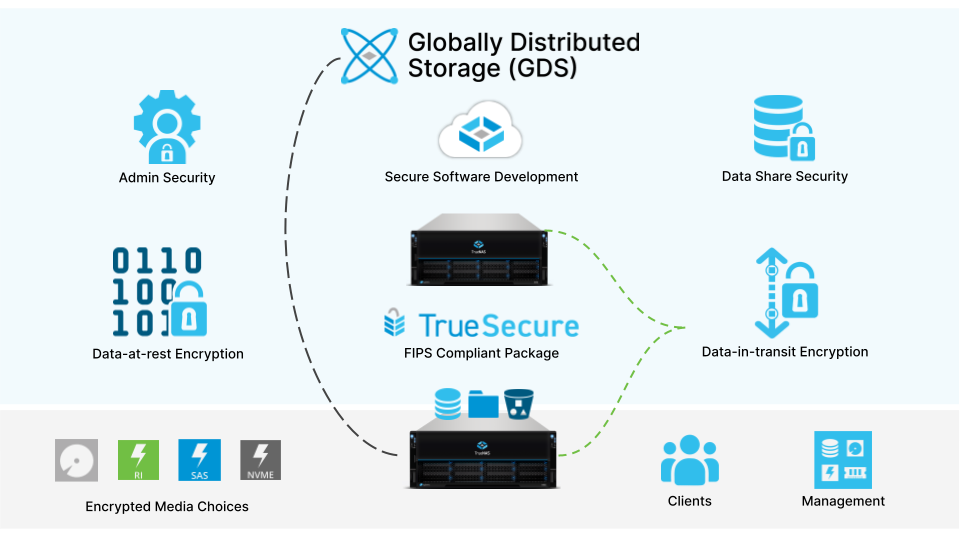
While TrueNAS provides robust security, it’s essential to also follow general network security best practices, such as using firewalls, Intrusion Detection/Prevention Systems, and integrating with a directory service such as Active Directory or LDAP, to maximize your defense-in-depth..
With recent releases of TrueNAS SCALE, there have been many security advancements:
Rootless administration allows changing away from using the commonly known “root” username, and instead setting up your own unique administrator usernames and passwords. This is the precursor to Restricted Admins.
Snapshot retention tags can prevent snapshots from being deleted, remaining on the system permanently as a restore point. This provides additional protection against ransomware by allowing the administrator to make a decision on when it is safe and appropriate to remove the ZFS snapshot outside of normal retention policies. Immutability is managed via this mechanism and ensured through Restricted Admins.
2-Factor Authentication (2FA) verifies the identities of administrators using Google Authenticator or any Time-based One-Time Password (TOTP) compliant authentication application.
iX-Storj Globally Distributed Storage inherently protects data by encrypting it on the TrueNAS system before distributing the data via erasure coding over a global network. Thanks to the combination of zero-trust and zero-knowledge encryption in use, no storage provider or government entity has access to your private data stored on iX-Storj. Electric Eel adds a cloud backup capability that provides robust backup and restore capabilities with immutable cloud snapshots for both shares and LUNs.
Auditing and logging capabilities have been added to increase security of system administration and SMB file sharing. Electric Eel adds logging of all configuration changes, any sudo commands, and attempts to login via ssh or Web UI.
Authentication and Authorization capabilities are required in any organization. Active Directory and LDAP are used to provide identity authentication and user authorization services for a whole organization. TrueNAS integrates well into these services. With Electric Eel, FreeIPA is also supported for those looking for an Open Source identity management.
TrueSecure Features
Some security capabilities are specific to the TrueSecure feature package available with TrueNAS Enterprise. As a reminder, TrueSecure provides the following additional security capabilities:
Restricted Admins provide separate roles for system/security admins, storage admins and monitors. As described earlier, these role separations are critical for larger organizations.
FIPS 140-2 validated storage media provide highly secure Data-at-Rest capabilities. Both HDD and SSD (SAS or NVMe) drives can be provided on standard TrueNAS Enterprise systems. These drives are similar to self-encrypting drives (SED) but include tamper-proof mechanisms for additional security.
FIPS 140-2 validated software encryption module provides highly secure Data-in-Transit capabilities. The validated encryption algorithms are more secure than the current open source algorithms and validated for use in critical Federal use-cases. For example, these algorithms will protect administration and data replication tasks.
Key Management Interoperability Protocol (KMIP) provides the capability to centralize the management of SED and ZFS encryption passwords for larger organizations. This capability is also in TrueNAS Enterprise 13.0.
Security Technical Information Guides (STIGs) for use with TrueSecure to help lockdown TrueNAS Enterprise systems and ensure secure operation. A General Purpose OS STIG is available for guidance.
TrueNAS Enterprise is secure storage that can be configured for government-grade security. Together, all of these features can be used with Active Directory to comply with the requirements identified in NIST 800-209, the USA cyber security standard for storage systems. Similarly, these features address the security requirements identified for storage systems in ISO/IEC 27040.
With the upcoming Electric Eel release in fall 2024, new features and tools will continue to enhance security. If you’d like to learn about any TrueNAS Enterprise system or security needs, please feel free to contact us.