Just came across this thread.
I thought it would test my nas to see if it was vulnerable.
It's Truenas core 13.0-U5.3.
It's got a Xeon E5 1650 v2 (6C 12T) and 128 GB ECC memory on a supermicro MB.
Storage is a total of 24 sata 'nas' drives. Some are WD Red's, some are seagate exos. The 24 drives are in 4 vdevs of 6 drives in Raid-Z2.
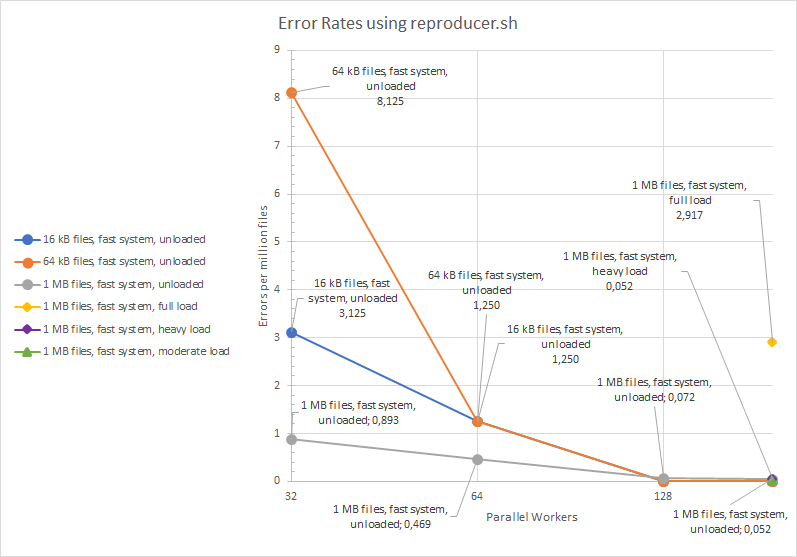
Reproducer script ran with (the built in) freebsd cp, not gnu cp. Set to 1 meg files, and 1000 copies.
The first run on this nas failed:
Code:
root@nas testdirectory # for i in {1..8} ; do ~/reproducer.sh & done; wait
[1] 37367
[2] 37368
[3] 37369
[4] 37370
[5] 37371
[6] 37372
[7] 37373
[8] 37376
writing files
writing files
writing files
writing files
writing files
writing files
writing files
writing files
checking files
checking files
checking files
checking files
checking files
checking files
checking files
checking files
Binary files reproducer_37370_0 and reproducer_37370_142 differ
Binary files reproducer_37370_0 and reproducer_37370_285 differ
Binary files reproducer_37370_0 and reproducer_37370_286 differ
Binary files reproducer_37367_0 and reproducer_37367_292 differ
Binary files reproducer_37370_0 and reproducer_37370_571 differ
Binary files reproducer_37370_0 and reproducer_37370_572 differ
Binary files reproducer_37370_0 and reproducer_37370_573 differ
Binary files reproducer_37370_0 and reproducer_37370_574 differ
Binary files reproducer_37367_0 and reproducer_37367_585 differ
Binary files reproducer_37367_0 and reproducer_37367_586 differ
[1] Done ~/reproducer.sh
[2] Done ~/reproducer.sh
[3] Done ~/reproducer.sh
[5] Done ~/reproducer.sh
[7]- Done ~/reproducer.sh
[8]+ Done ~/reproducer.sh
[4]- Done ~/reproducer.sh
[6]+ Done ~/reproducer.sh
As expected, all the non identical files are full of nulls:
Code:
root@nas testdirectory # hexdump reproducer_37370_142
0000000 0000 0000 0000 0000 0000 0000 0000 0000
*
0100000
root@nas testdirectory # hexdump reproducer_37370_285
0000000 0000 0000 0000 0000 0000 0000 0000 0000
*
0100000
root@nas testdirectory # hexdump reproducer_37370_286
0000000 0000 0000 0000 0000 0000 0000 0000 0000
*
0100000
root@nas testdirectory # hexdump reproducer_37370_572
0000000 0000 0000 0000 0000 0000 0000 0000 0000
*
0100000
root@nas testdirectory # hexdump reproducer_37367_585
0000000 0000 0000 0000 0000 0000 0000 0000 0000
*
0100000
I then tried running it at work on our Truenas X10, and it also failed on the first run:
Code:
Binary files reproducer_98467_0 and reproducer_98467_386 differ
Binary files reproducer_98467_0 and reproducer_98467_773 differ
Binary files reproducer_98467_0 and reproducer_98467_774 differ
I know this is unlikely to be an issue with network access, but it's still very worrying.