JoshDW19
Community Hall of Fame
- Joined
- May 16, 2016
- Messages
- 1,077
Today we are announcing a partnership with Nextcloud to provide an officially supported integration with TrueNAS. Nextcloud and TrueNAS are the #1 Open Source platforms for team collaboration and software-defined storage, respectively. The Nextcloud software suite will plug into TrueNAS and both companies will offer support for the powerful combination.
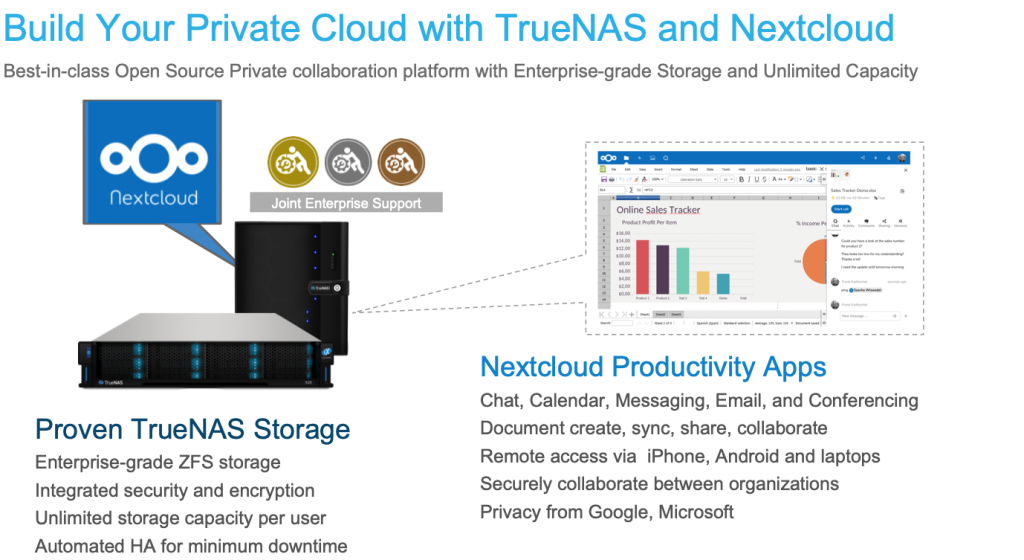
Together, Nextcloud and TrueNAS combine to provide a very complete private cloud infrastructure with both data storage and a suite of team collaboration services like document creation, chat, email, conferencing, calendaring, and several others. The combination is Open Source and self-hosted for maximum privacy and security. Unlike public cloud services (e.g. G-Suite, Office 365), an organization’s data can be securely managed onsite without any third-party backdoors. The HA and integrated replication capabilities of TrueNAS allow very reliable infrastructure to be built that is less dependent on Internet access bandwidth or reliability.
Nextcloud Hub is a collaboration platform designed to be self-hosted for complete privacy and cost control. The applications included are:
TrueNAS is a software-defined storage platform which provides file, block, object, and app storage built on top of OpenZFS. The powerful enterprise-grade capabilities of TrueNAS include:
An official Nextcloud plugin for TrueNAS simplifies the installation and operation of Nextcloud. The plugin can be installed with a few clicks on a webUI to create a dataset and initiate the Nextcloud instance. The engineering teams of both companies will collaborate to ensure reliable operation and resolve any integration issues found. Users will have access to both the large Nextcloud and TrueNAS communities for feedback and questions.
The Nextcloud plugin is free and directly available for download within TrueNAS. Small businesses and extended families can set up their own private clouds in just a few clicks. For larger schools and organizations, an Enterprise support option is available starting at $8/month per user with no limits on the storage capacity or compute power per user. With the use of TrueNAS HA systems, these organizations will be able to build high-reliability solutions. TrueCommand can be used to manage distributed infrastructure deployments.
The initial Nextcloud plugin will be based on Nextcloud 22 and TrueNAS CORE 12.0-U6. Collabora will run as a Linux server, VM, or Kubernetes pod. Future versions of the plugin will feature integration with Collabora Online and integration with TrueNAS SCALE for scale-out operation. We look forward to working with both Nextcloud and TrueNAS communities to deliver a first-class Open Source experience.
Later this week, on Wednesday the 13th of October (8am Pacific = 5pm Central European Time), we will host a live Q&A session with Morgan Littlewood, Senior VP at iXsystems, and Jos Poortvliet, Marketing Director and Co-Founder of Nextcloud. It will stream live from the TrueNAS YouTube channel and everyone will be able to ask them anything, so stay tuned!
If you have any additional questions or need advice on a new TrueNAS or Nextcloud project, please contact us. We are standing by to help.
The post Nextcloud and TrueNAS Collaborate to Help You Build Your Private Cloud appeared first on iXsystems, Inc. - Enterprise Storage & Servers.
Continue reading...

Together, Nextcloud and TrueNAS combine to provide a very complete private cloud infrastructure with both data storage and a suite of team collaboration services like document creation, chat, email, conferencing, calendaring, and several others. The combination is Open Source and self-hosted for maximum privacy and security. Unlike public cloud services (e.g. G-Suite, Office 365), an organization’s data can be securely managed onsite without any third-party backdoors. The HA and integrated replication capabilities of TrueNAS allow very reliable infrastructure to be built that is less dependent on Internet access bandwidth or reliability.
Nextcloud Hub is a collaboration platform designed to be self-hosted for complete privacy and cost control. The applications included are:
Nextcloud Files: Share and sync documents, spreadsheets, presentations, photos, and any other type of documents. With Collabora Online (included), multiple users can edit documents in real-time. Data can be accessed via the web or Windows, Mac, Linux, iOS, and Android clients.
Nextcloud Talk: Video and audio conferencing, combined with chat and whiteboarding, increase remote productivity in the new telecommuting era.
Nextcloud Groupware: Calendars, webmail, and task management are integrated with Files and Talk so teams can collaborate both within and across organizations.
TrueNAS is a software-defined storage platform which provides file, block, object, and app storage built on top of OpenZFS. The powerful enterprise-grade capabilities of TrueNAS include:
Data Management: Built into TrueNAS CORE, OpenZFS provides continuous integrity checks and self-healing, along with RAID functions, snapshots, clones, and replication of data.
Integrated Security: Encryption of data-at-rest is managed with admin-provided keys or integration with enterprise KMIP servers. Integrated VPNs and encrypted replication provide protection from hackers.
High Availability (HA): Downtime impacts productivity and is unacceptable to larger organizations. TrueNAS Enterprise provides dual-controller options (X-Series and M-Series) to deliver “five nines” availability (equivalent to downtime of less than 5 minutes per year).
Scalability: Scale up to 20 PB in a single one-rack system or scale out to even larger systems with TrueNAS SCALE. Most importantly, there is no need to pay excessively for users with high capacity needs due to photos or videos.
Unified Storage: While Nextcloud will manage a lot of data for the organization, the same TrueNAS may also manage NFS, SMB, iSCSI, or S3 data for other applications and backup systems.
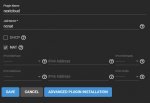
An official Nextcloud plugin for TrueNAS simplifies the installation and operation of Nextcloud. The plugin can be installed with a few clicks on a webUI to create a dataset and initiate the Nextcloud instance. The engineering teams of both companies will collaborate to ensure reliable operation and resolve any integration issues found. Users will have access to both the large Nextcloud and TrueNAS communities for feedback and questions.

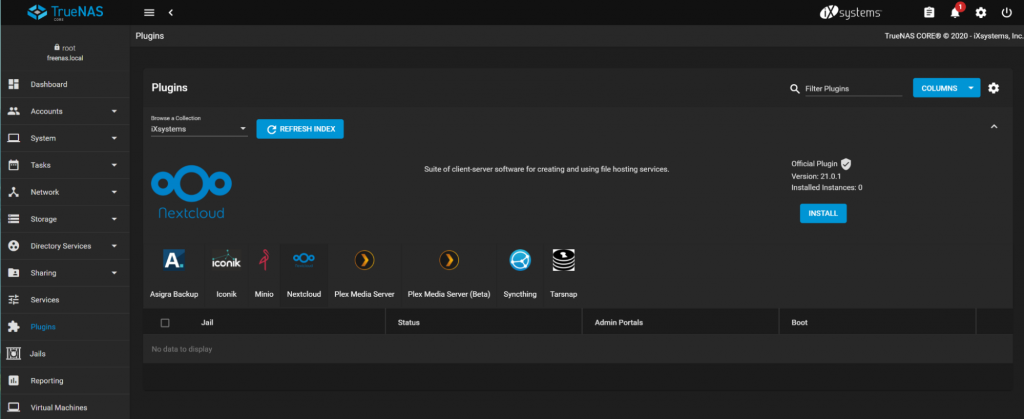
The Nextcloud Plugin with TrueNAS Web UI
The Nextcloud plugin is free and directly available for download within TrueNAS. Small businesses and extended families can set up their own private clouds in just a few clicks. For larger schools and organizations, an Enterprise support option is available starting at $8/month per user with no limits on the storage capacity or compute power per user. With the use of TrueNAS HA systems, these organizations will be able to build high-reliability solutions. TrueCommand can be used to manage distributed infrastructure deployments.
The initial Nextcloud plugin will be based on Nextcloud 22 and TrueNAS CORE 12.0-U6. Collabora will run as a Linux server, VM, or Kubernetes pod. Future versions of the plugin will feature integration with Collabora Online and integration with TrueNAS SCALE for scale-out operation. We look forward to working with both Nextcloud and TrueNAS communities to deliver a first-class Open Source experience.
Later this week, on Wednesday the 13th of October (8am Pacific = 5pm Central European Time), we will host a live Q&A session with Morgan Littlewood, Senior VP at iXsystems, and Jos Poortvliet, Marketing Director and Co-Founder of Nextcloud. It will stream live from the TrueNAS YouTube channel and everyone will be able to ask them anything, so stay tuned!
If you have any additional questions or need advice on a new TrueNAS or Nextcloud project, please contact us. We are standing by to help.
The post Nextcloud and TrueNAS Collaborate to Help You Build Your Private Cloud appeared first on iXsystems, Inc. - Enterprise Storage & Servers.
Continue reading...