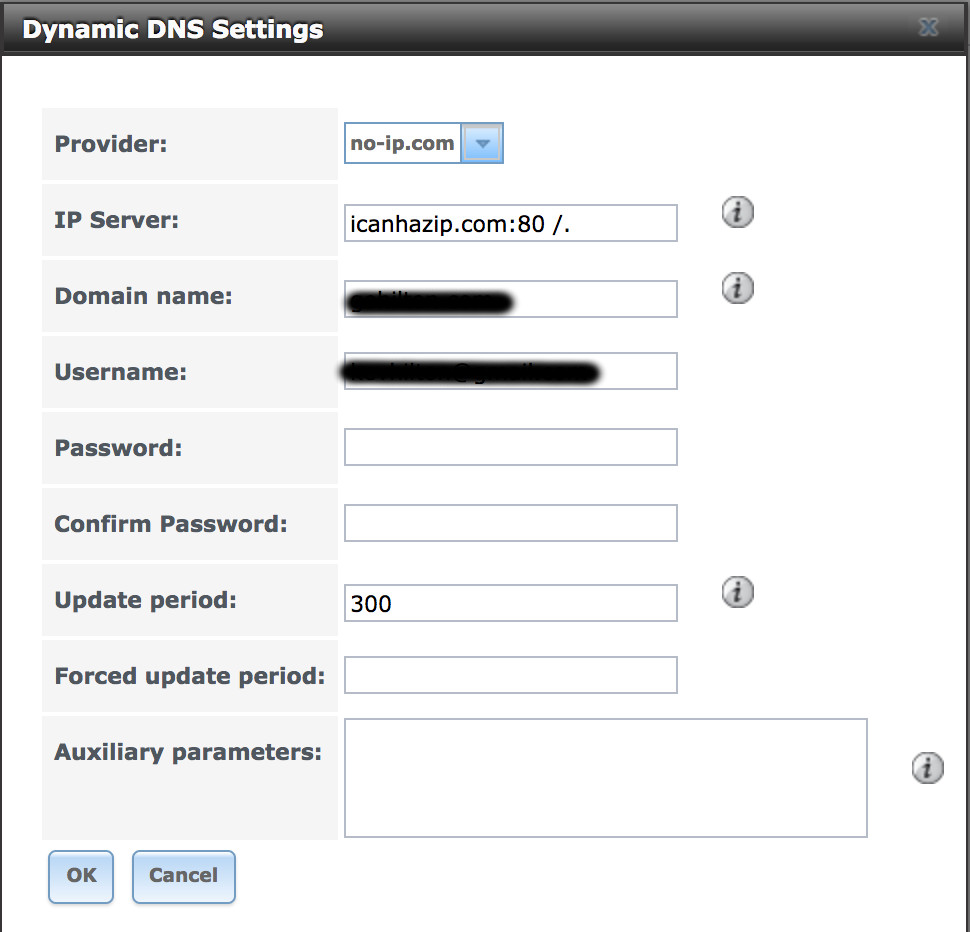
UPDATED: I edited this post to reflect my second build/rebuild of nextcloud. Also brought over a couple of changes (that were applicable) from my previous Owncloud server.
I have been searching high and low for a complete Nextcloud 11 installation on FreeBSD/FreeNAS. This thread was the best I could find, but it is a little out of date... so here is my contribution.... Maybe this could be inserted into a new thread?
I have Owncloud 8.x running on VBox (hosted from OSX). It's tuned the way I like it so will be comparing settings and trying to match 1 for 1 on my new FreeNAS Nextcloud jail.
THIS IS A MASHUP FROM Joshua Ruehlig's OWNCLOUD WRITE-UP from the beginning of this thread. [Many Thanks to Joshua!!]
I couldn't find anything recent on deploying NEXTCLOUD 11....
Create standard FreeNas Jail - Named it: "nextcloud"
added storage (external storage for data) - This will be connected at the end.
FROM:/mnt/abyss/nextcloud
TO:/mnt/nextcloud
jexec 5 /bin/sh
pkg update
pkg upgrade
pkg install bash wget
logout
jexec 5 /usr/local/bin/bash
pkg install mariadb101-server nginx redis php70-bz2 php70-ctype php70-curl php70-dom php70-exif php70-fileinfo php70-filter php70-gd php70-hash php70-iconv php70-intl php70-json php70-mbstring php70-mcrypt php70-pdo_mysql php70-openssl php70-posix php70-session php70-simplexml php70-xml php70-xmlreader php70-xmlwriter php70-xsl php70-wddx php70-zip php70-zlib php70-APCu php70-redis php70-pdo
sysrc 'nginx_enable=YES' 'php_fpm_enable=YES' 'mysql_enable=YES' 'redis_enable=YES'
CONFIG NGINX
rm -rf /usr/local/www/nginx
cp -rf /usr/local/www/nginx-dist /usr/local/www/nginx
mv /usr/local/etc/nginx/nginx.conf /usr/local/etc/nginx/nginx.conf.bak
vi /usr/local/etc/nginx/nginx.conf
#### THIS IS A FULL nginx.conf FILE
### MODIFIED FROM
https://docs.nextcloud.com/server/11/admin_manual/installation/nginx_nextcloud_9x.html
### It Could be tweaked some more
-- MAKE Sure you update your hostname and certname in this file.
Code:
load_module /usr/local/libexec/nginx/ngx_mail_module.so;
load_module /usr/local/libexec/nginx/ngx_stream_module.so;
#user nobody;
worker_processes 4; ##TUNE TO CPUS YOU HAVE
# This default error log path is compiled-in to make sure configuration parsing
# errors are logged somewhere, especially during unattended boot when stderr
# isn't normally logged anywhere. This path will be touched on every nginx
# start regardless of error log location configured here. See
# https://trac.nginx.org/nginx/ticket/147 for more info.
#
error_log /var/log/nginx/error.log;
#
#pid logs/nginx.pid;
events {
worker_connections 1024;
}
http {
include mime.types;
default_type application/octet-stream;
#log_format main '$remote_addr - $remote_user [$time_local] "$request" '
# '$status $body_bytes_sent "$http_referer" '
# '"$http_user_agent" "$http_x_forwarded_for"';
access_log /var/log/nginx/access.log;
sendfile on;
#tcp_nopush on;
#keepalive_timeout 0;
keepalive_timeout 65;
#gzip on;
upstream php-handler {
#server 127.0.0.1:9000;
server unix:/var/run/php-fpm.sock;
}
server {
listen 80;
server_name nextcloud.domain.com;
# enforce https
return 301 https://$server_name$request_uri;
}
# NGINX CAN USE HTTP/2 Protocol For Supported Browsers
server {
listen 443 ssl http2;
server_name nextcloud.domain.com;
ssl_certificate /usr/local/etc/nginx/ssl/nextcloud.domain.com.crt;
ssl_certificate_key /usr/local/etc/nginx/ssl/nextcloud.domain.com.key;
# Add headers to serve security related headers
# Before enabling Strict-Transport-Security headers please read into this
# topic first.
# add_header Strict-Transport-Security "max-age=15768000;
# includeSubDomains; preload;";
add_header Strict-Transport-Security "max-age=15768000; includeSubDomains; preload;";
add_header X-Content-Type-Options nosniff;
add_header X-Frame-Options "SAMEORIGIN";
add_header X-XSS-Protection "1; mode=block";
add_header X-Robots-Tag none;
add_header X-Download-Options noopen;
add_header X-Permitted-Cross-Domain-Policies none;
# Path to the root of your installation
root /usr/local/www/nextcloud/;
location = /robots.txt {
allow all;
log_not_found off;
access_log off;
}
# The following 2 rules are only needed for the user_webfinger app.
# Uncomment it if you're planning to use this app.
#rewrite ^/.well-known/host-meta /public.php?service=host-meta last;
#rewrite ^/.well-known/host-meta.json /public.php?service=host-meta-json
# last;
location = /.well-known/carddav {
return 301 $scheme://$host/remote.php/dav;
}
location = /.well-known/caldav {
return 301 $scheme://$host/remote.php/dav;
}
# set max upload size
client_max_body_size 512M;
fastcgi_buffers 64 4K;
# Disable gzip to avoid the removal of the ETag header
gzip off;
# Uncomment if your server is build with the ngx_pagespeed module
# This module is currently not supported.
#pagespeed off;
error_page 403 /core/templates/403.php;
error_page 404 /core/templates/404.php;
location / {
rewrite ^ /index.php$uri;
}
## THIS LOCATION BLOCK IS THROWING ERRORS - NEEDS REVIEW/EDITING
location ~ ^/(?:build|tests|config|lib|3rdparty|templates|data)/ {
deny all;
}
location ~ ^/(?:\.|autotest|occ|issue|indie|db_|console) {
deny all;
}
location ~ ^/(?:index|remote|public|cron|core/ajax/update|status|ocs/v[12]|updater/.+|ocs-provider/.+|core/templates/40[34])\.php(?:$|/) {
include fastcgi_params;
fastcgi_split_path_info ^(.+\.php)(/.*)$;
fastcgi_param SCRIPT_FILENAME $document_root$fastcgi_script_name;
fastcgi_param PATH_INFO $fastcgi_path_info;
fastcgi_param HTTPS on;
#Avoid sending the security headers twice
fastcgi_param modHeadersAvailable true;
fastcgi_param front_controller_active true;
fastcgi_pass php-handler;
fastcgi_intercept_errors on;
fastcgi_request_buffering off;
}
location ~ ^/(?:updater|ocs-provider)(?:$|/) {
try_files $uri/ =404;
index index.php;
}
# Adding the cache control header for js and css files
# Make sure it is BELOW the PHP block
location ~* \.(?:css|js|woff|svg|gif)$ {
try_files $uri /index.php$uri$is_args$args;
add_header Cache-Control "public, max-age=7200";
# Add headers to serve security related headers (It is intended to
# have those duplicated to the ones above)
# Before enabling Strict-Transport-Security headers please read into
# this topic first.
# add_header Strict-Transport-Security "max-age=15768000;
# includeSubDomains; preload;";
add_header X-Content-Type-Options nosniff;
add_header X-Frame-Options "SAMEORIGIN";
add_header X-XSS-Protection "1; mode=block";
add_header X-Robots-Tag none;
add_header X-Download-Options noopen;
add_header X-Permitted-Cross-Domain-Policies none;
# Optional: Don't log access to assets
access_log off;
}
location ~* \.(?:png|html|ttf|ico|jpg|jpeg)$ {
try_files $uri /index.php$uri$is_args$args;
# Optional: Don't log access to other assets
access_log off;
}
}
}
## Change '3650' to '365' For a 1 Year Cert
mkdir /usr/local/etc/nginx/ssl
openssl req -x509 -nodes -days 3650 -newkey rsa:2048 -keyout /usr/local/etc/nginx/ssl/nextcloud.domain.com.key -out /usr/local/etc/nginx/ssl/nextcloud.domain.com.crt
nginx -t
(should be successful on check)
CONFIG PHP
cp /usr/local/etc/php.ini-production /usr/local/etc/php.ini
vi /usr/local/etc/php.ini
Code:
cgi.fix_pathinfo=1
date.timezone = America/Denver
upload_max_filesize = 2048M
post_max_size = 2058M
vi /usr/local/etc/php-fpm.d/www.conf
Code:
;listen = 127.0.0.1:9000
listen = /var/run/php-fpm.sock
listen.owner = www
listen.group = www
env[PATH] = /usr/local/bin:/usr/bin:/bin
pm.max_children = 8 (I have an 8-core CPU, This is a tuneable)
pm.max_requests = 500 (uncomment this, This is a tuneable)
cp /usr/local/share/mysql/my-medium.cnf /usr/local/etc/my.cnf
vi /usr/local/etc/my.cnf
(These entries need to be present in the [mysql] section, MAKE SURE THERE ARE NOT DUPLICATE SETTINGS WITH DIFFERENT VALUES)
Code:
skip-networking
skip-name-resolve
expire_logs_days = 1
Find the section that says: # Uncomment the following if you are using InnoDB tables
And uncomment that block (should look like this):
Code:
innodb_data_home_dir = /var/db/mysql
innodb_data_file_path = ibdata1:10M:autoextend
innodb_log_group_home_dir = /var/db/mysql
# You can set .._buffer_pool_size up to 50 - 80 %
# of RAM but beware of setting memory usage too high
innodb_buffer_pool_size = 20M
innodb_additional_mem_pool_size = 2M
# Set .._log_file_size to 25 % of buffer pool size
innodb_log_file_size = 5M
innodb_log_buffer_size = 8M
innodb_lock_wait_timeout = 50
innodb_flush_method = O_DIRECT
skip-innodb_doublewrite
innodb_flush_log_at_trx_commit = 2
innodb_file_per_table
vi /usr/local/etc/redis.conf
Code:
port 0
unixsocket /tmp/redis.sock
unixsocketperm 777
service nginx start
service php-fpm start
service mysql-server start
service redis start
MORE CONFIG MARIADB/MYSQL
mysql_secure_installation
Enter current password for root (enter for none):
OK, successfully used password, moving on...
Set root password? [Y/n] y
New password:
Re-enter new password:
Password updated successfully!
Reloading privilege tables..
... Success!
Remove anonymous users? [Y/n]
... Success!
Disallow root login remotely? [Y/n]
... Success!
Remove test database and access to it? [Y/n]
- Dropping test database...
... Success!
- Removing privileges on test database...
... Success!
Reload privilege tables now? [Y/n]
... Success!
Cleaning up...
mysql -u root -p
Enter password:
CREATE DATABASE nextcloud;
GRANT ALL PRIVILEGES ON nextcloud.* TO 'nextcloud_user'@'localhost' IDENTIFIED BY 'nextcloud_pass'; (CHANGE USERNAME/PASSWD)
FLUSH PRIVILEGES;
exit;
cd /tmp
wget https://download.nextcloud.com/server/releases/nextcloud-11.0.0.zip (PROCEDURE BASED AROUND THIS VERSION)
cd /usr/local/www
unzip /tmp/nextcloud-11.0.0.zip
chown -R www:www /usr/local/www/nextcloud
CONFIG CRON (Once Nextcloud is online and senses the cron job running, it will auto switch from AJAX to Cron)
crontab -u www -e
Code:
*/15 * * * * /usr/local/bin/php -f /usr/local/www/nextcloud/cron.php
GOTO Browser
http://nextcloud.domain.com (or whatever you named your webserver, update your /etc/hosts if you need the domain to resolve locally)
Should be at the install wizard, so complete it.
Once complete, you will be logged into Nextcloud for the 1st time....
GOTO Top right <username>, then Admin page
will see some issues to resolve... (WE WILL GET BACK TO THESE)
now GO BACK TO CLI
NEXT SANITY CHECK
su -m www -c 'php /usr/local/www/nextcloud/occ status' (A SANITY CHECK)
- installed: true
- version: 11.0.0.10
- versionstring: 11.0.0
- edition:
su -m www -c 'php /usr/local/www/nextcloud/occ list' (to see options)
MEMCACHING/FILE LOCKING
https://docs.nextcloud.com/server/11/admin_manual/configuration_server/caching_configuration.html
su -m www -c 'php /usr/local/www/nextcloud/occ config:system:set memcache.local --value="\OC\Memcache\APCu"'
su -m www -c 'php /usr/local/www/nextcloud/occ config:system:set memcache.locking --value="\OC\Memcache\Redis"'
su -m www -c 'php /usr/local/www/nextcloud/occ config:system:set redis host --value="/tmp/redis.sock"'
su -m www -c 'php /usr/local/www/nextcloud/occ config:system:set redis port --value=0 --type=integer'
su -m www -c 'php /usr/local/www/nextcloud/occ config:system:set memcache.distributed --value="\OC\Memcache\Redis"'
Enable Avatars For User Profiles (optional)
FYI: I noticed I was still not seeing the place to upload my avatar. I had to manually edit /usr/local/www/nextcloud/config/config.php and remove the single quotes surrounding 'true' to be true, the restart your web services.... Now my avatar section was available.
su -m www -c 'php /usr/local/www/nextcloud/occ config:system:set enable_avatars --value=true'
TO ENABLE ALL PREVIEW PROVIDERS
su -m www -c 'php /usr/local/www/nextcloud/occ config:system:set enable_previews --value=true --type=boolean'
su -m www -c 'php /usr/local/www/nextcloud/occ config:system:set enabledPreviewProviders 0 --value="OC\Preview\PNG"'
su -m www -c 'php /usr/local/www/nextcloud/occ config:system:set enabledPreviewProviders 1 --value="OC\Preview\JPEG"'
su -m www -c 'php /usr/local/www/nextcloud/occ config:system:set enabledPreviewProviders 2 --value="OC\Preview\GIF"'
su -m www -c 'php /usr/local/www/nextcloud/occ config:system:set enabledPreviewProviders 3 --value="OC\Preview\BMP"'
su -m www -c 'php /usr/local/www/nextcloud/occ config:system:set enabledPreviewProviders 4 --value="OC\Preview\XBitmap"'
su -m www -c 'php /usr/local/www/nextcloud/occ config:system:set enabledPreviewProviders 5 --value="OC\Preview\MarkDown"'
su -m www -c 'php /usr/local/www/nextcloud/occ config:system:set enabledPreviewProviders 6 --value="OC\Preview\MP3"'
su -m www -c 'php /usr/local/www/nextcloud/occ config:system:set enabledPreviewProviders 7 --value="OC\Preview\TXT"'
su -m www -c 'php /usr/local/www/nextcloud/occ config:system:set enabledPreviewProviders 8 --value="OC\Preview\Illustrator"'
su -m www -c 'php /usr/local/www/nextcloud/occ config:system:set enabledPreviewProviders 9 --value="OC\Preview\Movie"'
su -m www -c 'php /usr/local/www/nextcloud/occ config:system:set enabledPreviewProviders 10 --value="OC\Preview\MSOffice2003"'
su -m www -c 'php /usr/local/www/nextcloud/occ config:system:set enabledPreviewProviders 11 --value="OC\Preview\MSOffice2007"'
su -m www -c 'php /usr/local/www/nextcloud/occ config:system:set enabledPreviewProviders 12 --value="OC\Preview\MSOfficeDoc"'
su -m www -c 'php /usr/local/www/nextcloud/occ config:system:set enabledPreviewProviders 13 --value="OC\Preview\OpenDocument"'
su -m www -c 'php /usr/local/www/nextcloud/occ config:system:set enabledPreviewProviders 14 --value="OC\Preview\PDF"'
su -m www -c 'php /usr/local/www/nextcloud/occ config:system:set enabledPreviewProviders 15 --value="OC\Preview\Photoshop"'
su -m www -c 'php /usr/local/www/nextcloud/occ config:system:set enabledPreviewProviders 16 --value="OC\Preview\Postscript"'
su -m www -c 'php /usr/local/www/nextcloud/occ config:system:set enabledPreviewProviders 17 --value="OC\Preview\StarOffice"'
su -m www -c 'php /usr/local/www/nextcloud/occ config:system:set enabledPreviewProviders 18 --value="OC\Preview\SVG"'
su -m www -c 'php /usr/local/www/nextcloud/occ config:system:set enabledPreviewProviders 19 --value="OC\Preview\TIFF"'
su -m www -c 'php /usr/local/www/nextcloud/occ config:system:set enabledPreviewProviders 20 --value="OC\Preview\Font"'
ENABLE VIDEO PREVIEWS
pkg install ffmpeg
RESTART SERVICES
service nginx restart
service php-fpm restart
service redis restart
CONFIG EXTERNAL STORAGE
Once logged in, GOTO TOP LEFT -> APPS -> NOT ENABLED -> ENABLE EXTERNAL STORAGE
GOTO TOP RIGHT -> USERNAME -> Admin -> EXTERNAL STORAGE -> Configure the EXTERNAL Storage to the Storage you attached to the jail.
Basic Install Completed, now configure your software however you want it!
I would highly recommend you restart your Jail at this point to validate everything works after a reboot.
==========================
#################################################
######### TROUBLESHOOTING/TUNING AREA ##########
#################################################
ISSUE #1
After restart, I see these in the error log: (Everytime I click somewhere one spawns)
2016/12/20 22:58:03 [error] 24805#102118: *44 access forbidden by rule, client: 192.168.1.xx, server: nextcloud.domain.com, request: "GET /data/.ocdata?t=1482299883686 HTTP/1.1", host: "nextcloud.domain.com"
2016/12/20 23:02:35 [error] 25779#100985: *20 access forbidden by rule, client: 192.168.1.xx, server: nextcloud.domain.com, request: "GET /data/.ocdata?t=1482300155871 HTTP/1.1", host: "nextcloud.domain.com"
2016/12/20 23:03:48 [error] 25905#100974: *15 access forbidden by rule, client: 192.168.1.xx, server: nextcloud.domain.com, request: "GET /data/.ocdata?t=1482300228746 HTTP/1.1", host: "nextcloud.domain.com"
2016/12/20 23:05:36 [error] 26142#102116: *3 access forbidden by rule, client: 192.168.1.xx, server: nextcloud.domain.com, request: "GET /data/.ocdata?t=1482300336618 HTTP/1.1", host: "nextcloud.domain.com"
2016/12/20 23:09:28 [error] 26369#102121: *26 access forbidden by rule, client: 192.168.1.xx, server: nextcloud.domain.com, request: "GET /data/.ocdata?t=1482300568421 HTTP/1.1", host: "nextcloud.domain.com"
2016/12/20 23:10:02 [error] 26369#102121: *30 access forbidden by rule, client: 192.168.1.xx, server: nextcloud.domain.com, request: "GET /data/.ocdata?t=1482300602480 HTTP/1.1", host: "nextcloud.domain.com"
2016/12/20 23:18:37 [error] 26818#102118: *2 access forbidden by rule, client: 192.168.1.xx, server: nextcloud.domain.com, request: "GET /data/.ocdata?t=1482301117857 HTTP/1.1", host: "nextcloud.domain.com"
....This block in the nginx.conf is causing it: (Need to figure out how to make this RULE Cleaner)
This block is directly from the Nextcloud documentation
Code:
location ~ ^/(?:build|tests|config|lib|3rdparty|templates|data)/ {
deny all;
}
#### DEATH ON THE LAST STEP ---- ARGH!!!!
#### I COULD HAVE JUST UNINSTALLED PHP56 and REINSTALLED THE PHP70 PKGS, BUT I HAVE NO IDEA HOW CLEAN IT WOULD BE
#### SO FOR NOW I WILL LIVE W/O DOC/DOCX PREVIEWS.
pkg install libreoffice pecl-imagick (TO ENABLE DOC/DOCX EDITING and PREVIEWS)
...<snippet from install>
Number of packages to be removed: 30
Number of packages to be installed: 117
The process will require 1 GiB more space.
Proceed with this action? [y/N]: y
[nextcloud] [1/147] Deinstalling php70-xsl-7.0.14...
[nextcloud] [1/147] Deleting files for php70-xsl-7.0.14: 100%
[nextcloud] [2/147] Deinstalling php70-wddx-7.0.14...
[nextcloud] [2/147] Deleting files for php70-wddx-7.0.14: 100%
[nextcloud] [3/147] Deinstalling php70-xmlreader-7.0.14...
[nextcloud] [3/147] Deleting files for php70-xmlreader-7.0.14: 100%
[nextcloud] [4/147] Deinstalling php70-redis-3.0.0_1...
[nextcloud] [4/147] Deleting files for php70-redis-3.0.0_1: 100%
[nextcloud] [5/147] Deinstalling php70-pdo_mysql-7.0.14...
[nextcloud] [5/147] Deleting files for php70-pdo_mysql-7.0.14: 100%
[nextcloud] [6/147] Deinstalling php70-xml-7.0.14...
[nextcloud] [6/147] Deleting files for php70-xml-7.0.14: 100%
[nextcloud] [7/147] Deinstalling php70-dom-7.0.14...
[nextcloud] [7/147] Deleting files for php70-dom-7.0.14: 100%
[nextcloud] [8/147] Deinstalling php70-xmlwriter-7.0.14...
[nextcloud] [8/147] Deleting files for php70-xmlwriter-7.0.14: 100%
[nextcloud] [9/147] Deinstalling php70-simplexml-7.0.14...
[nextcloud] [9/147] Deleting files for php70-simplexml-7.0.14: 100%
[nextcloud] [10/147] Deinstalling php70-gd-7.0.14...
[nextcloud] [10/147] Deleting files for php70-gd-7.0.14: 100%
[nextcloud] [11/147] Deinstalling php70-iconv-7.0.14...
[nextcloud] [11/147] Deleting files for php70-iconv-7.0.14: 100%
[nextcloud] [12/147] Deinstalling php70-intl-7.0.14...
[nextcloud] [12/147] Deleting files for php70-intl-7.0.14: 100%
[nextcloud] [13/147] Deinstalling php70-curl-7.0.14...
[nextcloud] [13/147] Deleting files for php70-curl-7.0.14: 100%
[nextcloud] [14/147] Deinstalling php70-session-7.0.14...
[nextcloud] [14/147] Deleting files for php70-session-7.0.14: 100%
[nextcloud] [15/147] Deinstalling php70-openssl-7.0.14...
[nextcloud] [15/147] Deleting files for php70-openssl-7.0.14: 100%
[nextcloud] [16/147] Deinstalling php70-posix-7.0.14...
[nextcloud] [16/147] Deleting files for php70-posix-7.0.14: 100%
[nextcloud] [17/147] Deinstalling php70-hash-7.0.14...
[nextcloud] [17/147] Deleting files for php70-hash-7.0.14: 100%
[nextcloud] [18/147] Deinstalling php70-exif-7.0.14...
[nextcloud] [18/147] Deleting files for php70-exif-7.0.14: 100%
[nextcloud] [19/147] Deinstalling php70-zlib-7.0.14...
[nextcloud] [19/147] Deleting files for php70-zlib-7.0.14: 100%
[nextcloud] [20/147] Deinstalling php70-mcrypt-7.0.14...
[nextcloud] [20/147] Deleting files for php70-mcrypt-7.0.14: 100%
[nextcloud] [21/147] Deinstalling php70-bz2-7.0.14...
[nextcloud] [21/147] Deleting files for php70-bz2-7.0.14: 100%
[nextcloud] [22/147] Deinstalling php70-ctype-7.0.14...
[nextcloud] [22/147] Deleting files for php70-ctype-7.0.14: 100%
[nextcloud] [23/147] Deinstalling php70-mbstring-7.0.14...
[nextcloud] [23/147] Deleting files for php70-mbstring-7.0.14: 100%
[nextcloud] [24/147] Deinstalling php70-json-7.0.14...
[nextcloud] [24/147] Deleting files for php70-json-7.0.14: 100%
[nextcloud] [25/147] Deinstalling php70-pdo-7.0.14...
[nextcloud] [25/147] Deleting files for php70-pdo-7.0.14: 100%
[nextcloud] [26/147] Deinstalling php70-fileinfo-7.0.14...
[nextcloud] [26/147] Deleting files for php70-fileinfo-7.0.14: 100%
[nextcloud] [27/147] Deinstalling php70-zip-7.0.14...
[nextcloud] [27/147] Deleting files for php70-zip-7.0.14: 100%
[nextcloud] [28/147] Deinstalling php70-filter-7.0.14...
[nextcloud] [28/147] Deleting files for php70-filter-7.0.14: 100%
[nextcloud] [29/147] Deinstalling php70-APCu-5.1.7...
[nextcloud] [29/147] Deleting files for php70-APCu-5.1.7: 100%
[nextcloud] [30/147] Deinstalling php70-7.0.14...
You may need to manually remove /usr/local/etc/php-fpm.d/
www.conf if it is no longer needed.
[nextcloud] [30/147] Deleting files for php70-7.0.14: 100%
...
[nextcloud] [144/147] Installing php56-5.6.29...
[nextcloud] [144/147] Extracting php56-5.6.29: 100%
ISSUE #3 . [Resolved - maybe be in next release of Nextcloud]
In the Admin section, if you view the "Server Info" it will prompt php to view the system memory, which it has no access to since it is jailed.
These are the errors I was gettings:
Code:
Error PHP file_get_contents(/proc/meminfo): failed to open stream: No such file or directory at /usr/local/www/nextcloud/apps/serverinfo/lib/SystemStatistics.php#71 2016-12-22T01:07:31-0700
Error PHP file_get_contents(/proc/meminfo): failed to open stream: No such file or directory at /usr/local/www/nextcloud/apps/serverinfo/lib/SystemStatistics.php#71 2016-12-22T01:07:30-0700
Error PHP file_get_contents(/proc/meminfo): failed to open stream: No such file or directory at /usr/local/www/nextcloud/apps/serverinfo/lib/SystemStatistics.php#71 2016-12-22T01:07:29-0700
Solution was to change the code in /usr/local/www/nextcloud/apps/serverinfo/lib/SystemStatistics.php
The restart your web services (nginx/php/redis)
Code:
-$memoryUsage = file_get_contents('/proc/meminfo');
+$memoryUsage = @file_get_contents('/proc/meminfo');
After adding in the external storage, I wanted to add a couple users to it, 1 user = contributor (create/change/no-delete) and the other user = viewer (read-only). Once you allow sharing and add a user, clicking the '...' next to their name will popup a dialogue to select the user access/mod level. This was missing.
Had to update the ownership to allow the webserver access, then rescan the files.
chmod -R www:www /mnt/nextcloud
su -m www -c 'php /usr/local/www/nextcloud/occ files:scan --all'
In the future I might allow my external storage to become a NFS/AFP share so that pictures or docs could be added from computers on my local network. This will require some more thought as a crontab would need to be added to re-scan periodically and this could mess up things with deleting files outside Nextcloud's knowledge/management.
UPDATE: Slight change to this config... I noticed that if I left the "Available for" field empty (defaults to ALL USERS), and checked the share button to add users, they would see every folder/file in the External Storage (not my intention to have that). So I ended up putting my admin username in the Available For field and then could add users to the folders/files in the External Storage.