-
Important Announcement for the TrueNAS Community.
The TrueNAS Community has now been moved. This forum has become READ-ONLY for historical purposes. Please feel free to join us on the new TrueNAS Community Forums
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
[How-To] ownCloud using NGINX, PHP-FPM, and MySQL
- Thread starter Joshua Parker Ruehlig
- Start date
Joshua Parker Ruehlig
Hall of Famer
- Joined
- Dec 5, 2011
- Messages
- 5,949
great! Haven't tried it myself yet with NGINX. They have pretty URLs now, (hide index.php) so gonna try to figure out how to get that working then I'll update the guide.Finished installing with oc-9.0.0 and it simply worked! Thank you.
Joshua Parker Ruehlig
Hall of Famer
- Joined
- Dec 5, 2011
- Messages
- 5,949
I might try this weekend.Hi Joshua,
would you Upgrade to 9.0 and Share with us the how-to soon? I am scared to do this by my self :/ :)
Gesendet von meinem SM-G900F mit Tapatalk
Sean Coston
Contributor
- Joined
- Jul 25, 2014
- Messages
- 128
Hi Joshua,
I've had nginx and oc up and running for over a year thanks to you, so...thanks.
I went through cyberjock's mod of the tutorial to use ssl with a self signed cert, and yes I do have my oc pointing at the wan. About three months ago I acquired a let's encrypt domain verification cert using one of the client tools posted on their website and a lot of command line machinations. Well this cert expired and I've come to realize I'd like to just install the regular let's encrypt client to keep my server cert up to date.
So sorry about the preamble...here's my question:
Will it break owncloud to use the Let'sEncrypt client? If this is a stupid question, please excuse me...I am a surgeon not an IT guy.
Sean
I've had nginx and oc up and running for over a year thanks to you, so...thanks.
I went through cyberjock's mod of the tutorial to use ssl with a self signed cert, and yes I do have my oc pointing at the wan. About three months ago I acquired a let's encrypt domain verification cert using one of the client tools posted on their website and a lot of command line machinations. Well this cert expired and I've come to realize I'd like to just install the regular let's encrypt client to keep my server cert up to date.
So sorry about the preamble...here's my question:
Will it break owncloud to use the Let'sEncrypt client? If this is a stupid question, please excuse me...I am a surgeon not an IT guy.
Sean
Joshua Parker Ruehlig
Hall of Famer
- Joined
- Dec 5, 2011
- Messages
- 5,949
nope, using a different certificate/letsencrypt doesn't affect the owncloud install. awesome a surgeon! I'm not in IT myself either, just do this as a hobby.
I haven't set this up myself but I did see packages for it. I do know to get your cert it requires binding to a port>1024 and being accessible from the WAN.
I think there are modules for nginx that will do this for you and even install the cert +reload nginx.
I use https through haproxy on my pfsense router so I haven't experimented with this.
I haven't set this up myself but I did see packages for it. I do know to get your cert it requires binding to a port>1024 and being accessible from the WAN.
I think there are modules for nginx that will do this for you and even install the cert +reload nginx.
I use https through haproxy on my pfsense router so I haven't experimented with this.
Hi everyone.
I would like to say Thank you Joshua and everyone else that has posted here you have been a great help and very useful source of information :)
I thought it time to share what I have setup and ask for advice and some help, so here it goes.
I setup OwnCloud 8.2.2, fail2ban and LetsEncrypt
For ownCloud I used Joshua's guide and for Fail2ban and LetsEncrypt I used Zaggynl's post on page 48.
in the hope some of you will point out any mistakes that I have made and help me improve my settings or that my post may help someone else.
Sean, as I say I followed the links below posted by Zaggynl for Letsencrypt the setup was clear & easy to follow.
the setup. https://adambard.com/blog/using-letsencrypt-with-nginx/
the Config. https://raymii.org/s/tutorials/Strong_SSL_Security_On_nginx.html and https://sethvargo.com/getting-an-a-plus-on-qualys-ssl-labs-tester/
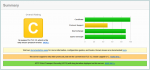
I have played around a bit with the config and so far only got a C on SSLabs test page which I'm happy with but would love to improve on ( image is attached )
Configuring Let's Encrypt for nginx with Automatic Renewal
I also setup a crontab for monthly auto renew LetsEncrypt Cert as it only lasts for 90 days and should be renewed 30 days before it runs out, the auto renew should renew it when it gets to within 30 days.
https://johnmaguire.me/2015/12/configuring-nginx-lets-encrypt-automatic-renewal/
my Nginx config is looking a bit of a mess but it seems to work ok I do not profess to understand any of it it's just been a lot of cut and paste then more reading and more cut and paste ;)
I also paid £9 for a domain name from Fasthosts and pointed it to my ip.
if you do use the below config don't forget to run the commented out openssl command that installs the /etc/nginx/dhparam.pem file this makes a big difference to your SSLabs score and i'm sure also to your security.
I also noticed that for me Nano missed out some ~ * Astrex or Tilde's when re-pasting :( this had me going nuts for a few days)
so here's what it consists of.
I would like to say Thank you Joshua and everyone else that has posted here you have been a great help and very useful source of information :)
I thought it time to share what I have setup and ask for advice and some help, so here it goes.
I setup OwnCloud 8.2.2, fail2ban and LetsEncrypt
For ownCloud I used Joshua's guide and for Fail2ban and LetsEncrypt I used Zaggynl's post on page 48.
in the hope some of you will point out any mistakes that I have made and help me improve my settings or that my post may help someone else.
Sean, as I say I followed the links below posted by Zaggynl for Letsencrypt the setup was clear & easy to follow.
the setup. https://adambard.com/blog/using-letsencrypt-with-nginx/
the Config. https://raymii.org/s/tutorials/Strong_SSL_Security_On_nginx.html and https://sethvargo.com/getting-an-a-plus-on-qualys-ssl-labs-tester/
I have played around a bit with the config and so far only got a C on SSLabs test page which I'm happy with but would love to improve on ( image is attached )
Configuring Let's Encrypt for nginx with Automatic Renewal
I also setup a crontab for monthly auto renew LetsEncrypt Cert as it only lasts for 90 days and should be renewed 30 days before it runs out, the auto renew should renew it when it gets to within 30 days.
https://johnmaguire.me/2015/12/configuring-nginx-lets-encrypt-automatic-renewal/
my Nginx config is looking a bit of a mess but it seems to work ok I do not profess to understand any of it it's just been a lot of cut and paste then more reading and more cut and paste ;)
I also paid £9 for a domain name from Fasthosts and pointed it to my ip.
if you do use the below config don't forget to run the commented out openssl command that installs the /etc/nginx/dhparam.pem file this makes a big difference to your SSLabs score and i'm sure also to your security.
- # Diffie-Hellman parameter for DHE ciphersuites, recommended 2048 bits
- # Generate with: openssl dhparam -out /etc/nginx/dhparam.pem 2048
I also noticed that for me Nano missed out some ~ * Astrex or Tilde's when re-pasting :( this had me going nuts for a few days)
so here's what it consists of.
Code:
worker_processes 2;
events {
worker_connections 1024;
}
http {
include mime.types;
default_type application/octet-stream;
sendfile off;
keepalive_timeout 65;
gzip off;
server {
listen 80;
server_name your.domain.com;
return 301 https://$server_name$request_uri;
}
server {
listen 443 ssl;
server_name your.domain.com;
ssl on;
ssl_certificate /etc/letsencrypt/live/your.domain.com/fullchain.pem;
ssl_certificate_key /etc/letsencrypt/live/your.domain.com/privkey.pem;
ssl_trusted_certificate /etc/letsencrypt/live/your.domain.com/fullchain.pem;
ssl_session_cache shared:SSL:50m;
# Diffie-Hellman parameter for DHE ciphersuites, recommended 2048 bits
# Generate with: openssl dhparam -out /etc/nginx/dhparam.pem 2048
ssl_dhparam /usr/local/etc/nginx/dhparam.pem;
ssl_session_timeout 24h;
ssl_buffer_size 1400;
ssl_session_tickets off;
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
ssl_ciphers 'ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA256:ECDHE-ECDSA-AES128-SHA:ECDHE-RSA-AES256-SHA384:ECDHE-RSA-AES128-SHA:ECDHE-ECDSA-AES256-SHA384:ECDHE-ECDSA-AES256-SHA:ECDHE-RSA-AES256-SHA:DHE-RSA-AES128-SHA256:DHE-RSA-AES128-SHA:DHE-RSA-AES256-SHA256:DHE-RSA-AES256-SHA:ECDHE-ECDSA-DES-CBC3-SHA:ECDHE-RSA-DES-CBC3-SHA:EDH-RSA-DES-CBC3-SHA:AES128-GCM-SHA256:AES256-GCM-SHA384:AES128-SHA256:AES256-SHA256:AES128-SHA:AES256-SHA:DES-CBC3-SHA:!DSS';
ssl_prefer_server_ciphers on;
ssl_stapling on;
ssl_stapling_verify on;
add_header Strict-Transport-Security "max-age=15768000; includeSubDomains; preload;";
add_header X-Content-Type-Options nosniff;
add_header X-Frame-Options "SAMEORIGIN";
add_header X-XSS-Protection "1; mode=block";
resolver 8.8.4.4 8.8.8.8 valid=300s;
resolver_timeout 10s;
root /usr/local/www/owncloud;
location = /robots.txt { allow all; access_log off; log_not_found off; }
location = /favicon.ico { access_log off; log_not_found off; }
location ^~ / {
index index.php;
try_files $uri $uri/ /index.php$is_args$args;
error_page 403 /core/templates/403.php;
error_page 404 /core/templates/404.php;
rewrite ^/caldav(.*)$ /remote.php/caldav$1 redirect;
rewrite ^/carddav(.*)$ /remote.php/carddav$1 redirect;
rewrite ^/webdav(.*)$ /remote.php/webdav$1 redirect;
client_max_body_size 2048M;
location ~ ^/(?:\.|build|tests|config|lib|3rdparty|templates|data|autotest|occ|issue|indie|db_|console)
{
deny all;
}
location ~ \.php(?:$|/) {
fastcgi_split_path_info ^(.+\.php)(/.*)$;
fastcgi_pass unix:/var/run/php-fpm.sock;
fastcgi_param SCRIPT_FILENAME $document_root$fastcgi_script_name;
fastcgi_param PATH_INFO $fastcgi_path_info;
fastcgi_intercept_errors on;
fastcgi_param modHeadersAvailable true;
include fastcgi_params;
}
location ~* \.(?:jpg|gif|ico|png|css|js|svg)$ {
expires 30d; add_header Cache-Control public;
}
}
}
}
Attachments
Last edited:
Although owncloud is working very well there are 2 errors in the owncloud admin log I would like help with if possible :)
Error PHP PHP Startup: Unable to load dynamic library '/usr/local/lib/php/20131226/redis.so' - /usr/local/lib/php/20131226/redis.so: Undefined symbol "php_session_create_id" at Unknown#0
Error PHP Array to string conversion at /usr/local/www/owncloud/lib/private/template/functions.php#36
Thank you for any help with these and of course any helpful tips on the Nginx.config file :)
Error PHP PHP Startup: Unable to load dynamic library '/usr/local/lib/php/20131226/redis.so' - /usr/local/lib/php/20131226/redis.so: Undefined symbol "php_session_create_id" at Unknown#0
Error PHP Array to string conversion at /usr/local/www/owncloud/lib/private/template/functions.php#36
Thank you for any help with these and of course any helpful tips on the Nginx.config file :)
Joshua Parker Ruehlig
Hall of Famer
- Joined
- Dec 5, 2011
- Messages
- 5,949
the guide has been slowly evolving. Maybe you enabled redis in the config but never installed the php moduleAlthough owncloud is working very well there are 2 errors in the owncloud admin log I would like help with if possible :)
Error PHP PHP Startup: Unable to load dynamic library '/usr/local/lib/php/20131226/redis.so' - /usr/local/lib/php/20131226/redis.so: Undefined symbol "php_session_create_id" at Unknown#0
Error PHP Array to string conversion at /usr/local/www/owncloud/lib/private/template/functions.php#36
Thank you for any help with these and of course any helpful tips on the Nginx.config file :)
pkg install php56-redis
Hi Joshua. Thank you for your reply :)
it seems to be installed ok.
root@owncloudjail:/ # pkg install php56-redis
Updating FreeBSD repository catalogue...
FreeBSD repository is up-to-date.
All repositories are up-to-date.
Checking integrity... done (0 conflicting)
The most recent version of packages are already installed
root@owncloudjail:/ #
it seems to be installed ok.
root@owncloudjail:/ # pkg install php56-redis
Updating FreeBSD repository catalogue...
FreeBSD repository is up-to-date.
All repositories are up-to-date.
Checking integrity... done (0 conflicting)
The most recent version of packages are already installed
root@owncloudjail:/ #
Ooo... I must have missed this one on google :( "pkg install -f databases/php56-redis" did the trick error has now gone.
https://bugs.freebsd.org/bugzilla/show_bug.cgi?id=205013
https://bugs.freebsd.org/bugzilla/show_bug.cgi?id=205013
I found a Fix for the "Error PHP Array to string conversion at /usr/local/www/owncloud/lib/private/template/functions.php#36"
https://github.com/owncloud/core/pull/18921/files
so now my OwnCloud Admin Log is error free :)
if anyone can give me any advice on the Nginx.config it would be much appreciated as i'm not sure if everything is in the right order or if there is stuff that doesn't even need to be in there or stuff that should be in there that isn't, I know that just because it works it doesn't mean it's right.
https://github.com/owncloud/core/pull/18921/files
so now my OwnCloud Admin Log is error free :)
if anyone can give me any advice on the Nginx.config it would be much appreciated as i'm not sure if everything is in the right order or if there is stuff that doesn't even need to be in there or stuff that should be in there that isn't, I know that just because it works it doesn't mean it's right.
I found a Fix for the "Error PHP Array to string conversion at /usr/local/www/owncloud/lib/private/template/functions.php#36"
https://github.com/owncloud/core/pull/18921/files
so now my OwnCloud Admin Log is error free :)
I know I sort of answered my own question but if anyone else is worried about the errors i hope this will help.
if anyone can give me any advice on the Nginx.config it would be as i'm not sure if everything is in the right order or if there is stuff that doesn't need to even be in there
https://github.com/owncloud/core/pull/18921/files
so now my OwnCloud Admin Log is error free :)
I know I sort of answered my own question but if anyone else is worried about the errors i hope this will help.
if anyone can give me any advice on the Nginx.config it would be as i'm not sure if everything is in the right order or if there is stuff that doesn't need to even be in there
Joshua Parker Ruehlig
Hall of Famer
- Joined
- Dec 5, 2011
- Messages
- 5,949
Im working on the nginx.conf and will post once it's done.
Sorry Joshua it wasn't meant as a poke/bump and I seem to have edited my last post and sort of double post :(
So I found out that the Nginx 1.8 couldn't use TLS 1.2, TLS 1.1 or OCSP stapling :(
so I installed Nginx 1.9.12 and Look what Happend :)
ok there was a webdav error that came up in the logs it was easier to just removed the webdav stuff in the nginx.config for the time being ;)
and a Memcache \OC\Memcache\APCu not available for distributed cache
Memcache \OC\Memcache\APCu not available for local cache



So I found out that the Nginx 1.8 couldn't use TLS 1.2, TLS 1.1 or OCSP stapling :(
so I installed Nginx 1.9.12 and Look what Happend :)
ok there was a webdav error that came up in the logs it was easier to just removed the webdav stuff in the nginx.config for the time being ;)
and a Memcache \OC\Memcache\APCu not available for distributed cache
Memcache \OC\Memcache\APCu not available for local cache
Last edited:
Joshua Parker Ruehlig
Hall of Famer
- Joined
- Dec 5, 2011
- Messages
- 5,949
what are you asking? if APCu is not avaialble make sure you installed it.Sorry Joshua it wasn't meant as a poke/bump and I seem to have edited my last post and sort of double post :(
So I found out that the Nginx 1.8 couldn't use TLS 1.2, TLS 1.1 or OCSP stapling :(
so I installed Nginx 1.9.12 and Look what Happend :)
ok there was a webdav error that came up in the logs it was easier to just removed the webdav stuff in the nginx.config for the time being ;)
and a Memcache \OC\Memcache\APCu not available for distributed cache
Memcache \OC\Memcache\APCu not available for local cache
View attachment 10989
View attachment 10990
View attachment 10991
I wasn't actually asking anything as I assumed that these were a side affect of the nginx update, I was just pointing out that they were the only 2 errors that I got due to the update.
yes "The most recent version of packages are already installed" as in your guide.
Sorry I am new to forums, if this is useless information I'll stop posting I had thought that it might be interesting as it's not been posted before.
yes "The most recent version of packages are already installed" as in your guide.
Sorry I am new to forums, if this is useless information I'll stop posting I had thought that it might be interesting as it's not been posted before.
Joshua Parker Ruehlig
Hall of Famer
- Joined
- Dec 5, 2011
- Messages
- 5,949
no worries, u just thought you might be asking something.
robuyo
Dabbler
- Joined
- Apr 13, 2015
- Messages
- 11
I've an owncloud 8.x jail working, so I've decided to create a fresh one with the 9.x version.
Just created a new jail following instructions from original post and everything seems nice until I try to upload a file from the web, I can upload any file with the Win/OSX client.
I received this error: (File size is 30Kb, I've tried different file sizes)

And when I go to /var/log/nginx-error.log this appears:
2016/03/27 11:11:38 [error] 7484#0: *5 FastCGI sent in stderr: "PHP message: PHP Fatal error: Class 'OC' not found in /usr/local/www/owncloud/apps/files/ajax/upload.php on line 36" while reading response header from upstream, client: 192.168.1.90, server: , request: "POST /owncloud/apps/files/ajax/upload.php HTTP/1.1", upstream: "fastcgi://unix:/var/run/php-fpm.sock:", host: "192.168.1.123"
Seems like a problem with php-fpm?
Just created a new jail following instructions from original post and everything seems nice until I try to upload a file from the web, I can upload any file with the Win/OSX client.
I received this error: (File size is 30Kb, I've tried different file sizes)
And when I go to /var/log/nginx-error.log this appears:
2016/03/27 11:11:38 [error] 7484#0: *5 FastCGI sent in stderr: "PHP message: PHP Fatal error: Class 'OC' not found in /usr/local/www/owncloud/apps/files/ajax/upload.php on line 36" while reading response header from upstream, client: 192.168.1.90, server: , request: "POST /owncloud/apps/files/ajax/upload.php HTTP/1.1", upstream: "fastcgi://unix:/var/run/php-fpm.sock:", host: "192.168.1.123"
Seems like a problem with php-fpm?
Joshua Parker Ruehlig
Hall of Famer
- Joined
- Dec 5, 2011
- Messages
- 5,949
hmm, it's the nginx config. still need to adjust it for OC9. you can always insert an /index.php after /owncloud in the URL
Important Announcement for the TrueNAS Community.
The TrueNAS Community has now been moved. This forum will now become READ-ONLY for historical purposes. Please feel free to join us on the new TrueNAS Community Forums.Related topics on forums.truenas.com for thread: "[How-To] ownCloud using NGINX, PHP-FPM, and MySQL"
Similar threads
- Replies
- 83
- Views
- 44K
- Locked
- Replies
- 78
- Views
- 68K
- Replies
- 10
- Views
- 5K
- Replies
- 4
- Views
- 5K
- Replies
- 8
- Views
- 9K