Hello All
Core 13.0-U5, 32GB Memory, Xeon E3-1200 4-core, 128K SSD boot, 12 8TB spinners in pool.
I currently have OpenVPN server running successfully on a Windows 10 box but, I prefer to have the server reside on a TrueNAS box.
The windows box gets rebooted too often to be a good OpenVPN server.
I have used easy-rsa to create a PKI, CA, certs and keys on the TrueNAS box.
I followed this forum post to get this far on TrueNAS:
https://www.truenas.com/community/t...envpn-inside-a-jail-in-freenas-11-1-u1.61681/
Although, I am not doing this in a jail.
I did all the easy-rsa work in the main TrueNAS shell because TrueNAS 13.0 has a builtin OpenVPN server.
Now I need to configure that builtin OpenVPN server to use the certs and keys that I have already generated.
The OpenVPN server setup GUI shows:
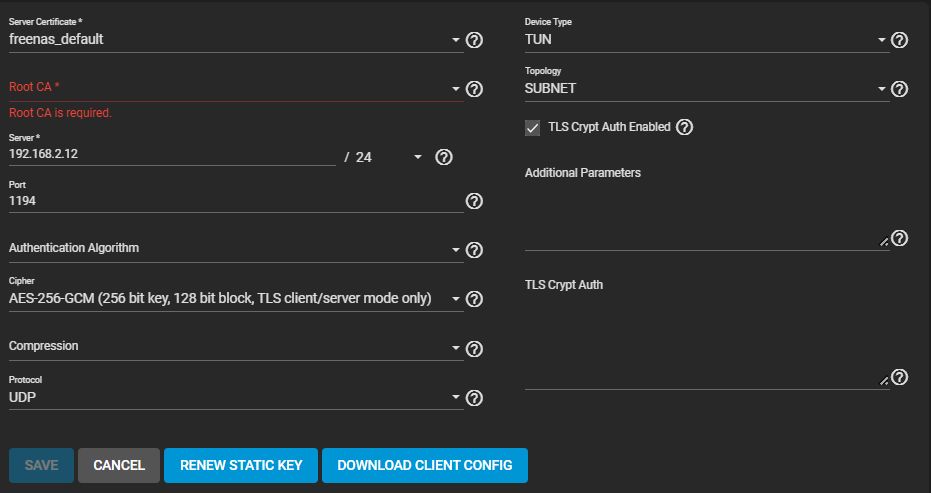
I have a server certificate "openvpn-server.crt" in "/usr/local/lib/openvpn/keys" and a "CA" also in "/usr/local/lib/openvpn/keys".
I cannot enter a path in either the "Server Certificate" nor the "Root CA" boxes to point to the existing location in "/usr/local/lib/openvpn/keys".
Where do I need to copy the "openvpn-server.crt" and ca.crt files to, so that they will show up and be selectable within the GUI shown above?
Also, what should I do in the "TLS Crypt Auth" box?
It appears that that entry will take a path but, I have no idea if entering "/usr/local/lib/openvpn/keys/ta.key" is the correct thing to do.
Also what "Authentication Algorithm" should I select corresponding to the certs/keys that I have generated?
Here is the contents of my "openvpn.conf" file:
END openvpn.conf
Thank You
Core 13.0-U5, 32GB Memory, Xeon E3-1200 4-core, 128K SSD boot, 12 8TB spinners in pool.
I currently have OpenVPN server running successfully on a Windows 10 box but, I prefer to have the server reside on a TrueNAS box.
The windows box gets rebooted too often to be a good OpenVPN server.
I have used easy-rsa to create a PKI, CA, certs and keys on the TrueNAS box.
root@plum[/usr/local/lib/openvpn/keys]# ls -l
-rw------- 1 root wheel 1233 Jul 30 06:41 ca.crt
-rw------- 1 root wheel 424 Jul 30 06:41 dh.pem
-rw------- 1 root wheel 4678 Jul 30 06:41 openvpn-server.crt
-rw------- 1 root wheel 1708 Jul 30 06:41 openvpn-server.key
-rw------- 1 root wheel 636 Jul 30 06:42 ta.keyI followed this forum post to get this far on TrueNAS:
https://www.truenas.com/community/t...envpn-inside-a-jail-in-freenas-11-1-u1.61681/
Although, I am not doing this in a jail.
I did all the easy-rsa work in the main TrueNAS shell because TrueNAS 13.0 has a builtin OpenVPN server.
Now I need to configure that builtin OpenVPN server to use the certs and keys that I have already generated.
The OpenVPN server setup GUI shows:
I have a server certificate "openvpn-server.crt" in "/usr/local/lib/openvpn/keys" and a "CA" also in "/usr/local/lib/openvpn/keys".
I cannot enter a path in either the "Server Certificate" nor the "Root CA" boxes to point to the existing location in "/usr/local/lib/openvpn/keys".
Where do I need to copy the "openvpn-server.crt" and ca.crt files to, so that they will show up and be selectable within the GUI shown above?
Also, what should I do in the "TLS Crypt Auth" box?
It appears that that entry will take a path but, I have no idea if entering "/usr/local/lib/openvpn/keys/ta.key" is the correct thing to do.
Also what "Authentication Algorithm" should I select corresponding to the certs/keys that I have generated?
Here is the contents of my "openvpn.conf" file:
server 10.8.0.0 255.255.255.0
port 1194
proto udp4
dev tun
topology subnet
ca /usr/local/lib/openvpn/keys/ca.crt
cert /usr/local/lib/openvpn/keys/openvpn-server.crt
key /usr/local/lib/openvpn/keys/openvpn-server.key # This file should be kept secret
dh /usr/local/lib/openvpn/keys/dh.pem
tls-auth /usr/local/lib/openvpn/keys/ta.key 0 # This file is secret
push "route 192.168.2.0 255.255.255.0" # Route to Server Network pushed to Client
# Created route in Server Gateway (10.8.0.0 255.255.255.0 192.168.2.12) # Anything destined for the VPN Tunnel goes to the VPN Server Box
route 192.168.3.0 255.255.255.0 # Route to Client Network used by Server
# Created route in Server Gateway (192.168.3.0 255.255.255.0 192.168.2.12) # Anything destined for the Client LAN goes to the VPN Server Box
client-config-dir /usr/local/lib/openvpn/ccd # Client specific push parameter files are stored here
push "route 192.168.3.0 255.255.255.0" # Client Network (also "iroute 192.168.3.0 255.255.255.0" is defined for client in CCD directory)
ifconfig-pool-persist /usr/local/lib/openvpn/ipp.txt
keepalive 10 120
data-ciphers CHACHA20-POLY1305:AES-256-GCM:AES-128-GCM # Prefer ChaCha, it's more secure.
max-clients 3
persist-key
persist-tun
status openvpn-status.log
verb 4
mute 20
explicit-exit-notify 1END openvpn.conf
Thank You
