drinking12many
Contributor
- Joined
- Apr 8, 2012
- Messages
- 148
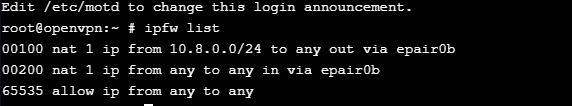
I have been trying for a bit to get this to work and I feel like I am missing something. I followed a guide I found for 11.1 I think it was. I have it working in that I can use my S9 and connect over the cell network to my openvpn jail. I can ping anything on my network internally and they can ping me back. I can resolve and ping websites external and internal to my network. Though when I open chrome and try to load any web pages they fail internal or external. Almost like its using a proxy or something though I can find nothing to confirm that. I did add a static route to my home router which is when I started being able to ping back into my vpn from internal machines.
I had an openvpn appliance running on Debian under ESX for years and it always worked fine though it has a web interface and has been generally reliable, but I am trying to move it to a jail so I dont have to keep that Dell server on all the time yet still be able to connect hit the idrac and turn it on when needed.
openvpn.conf
I had an openvpn appliance running on Debian under ESX for years and it always worked fine though it has a web interface and has been generally reliable, but I am trying to move it to a jail so I dont have to keep that Dell server on all the time yet still be able to connect hit the idrac and turn it on when needed.
openvpn.conf
Code:
port 1194 proto udp dev tun ca /usr/local/etc/openvpn/keys/ca.crt cert /usr/local/etc/openvpn/keys/openvpn-server.crt key /usr/local/etc/openvpn/keys/openvpn-server.key # This file should be kept secret dh /usr/local/etc/openvpn/keys/dh2048.pem topology subnet server 10.8.0.0 255.255.255.0 ifconfig-pool-persist ipp.txt push "route 192.168.1.0 255.255.255.0" push "redirect-gateway def1 bypass-dhcp" push "dhcp-option DNS 192.168.1.96" push "dhcp-option DNS 192.168.1.98" push "dhcp-option DOMAIN home.local" client-to-client keepalive 10 120 tls-auth /usr/local/etc/openvpn/keys/ta.key 0 # This file is secret cipher AES-256-CBC compress lz4-v2 push "compress lz4-v2" max-clients 10 user nobody group nobody persist-key persist-tun status openvpn-status.log verb 3 explicit-exit-notify 1
Last edited:
