Mannekino
Patron
- Joined
- Nov 14, 2012
- Messages
- 332
After dealing with unexplained problems related to using OpenVPN and PIA in my Transmission Jail I decided to switch to something else. I spent the last 5 days trying to troubleshoot the problem but got nowhere. After discussing my problems on Discord it was suggested I switch to a different VPN provider and I got suggested Mullvad. On the website of Mullvad they recommended the use of WireGuard instead of OpenVPN so I changed that also.
Prerequisites
This guide assumes you have a Transmission Jail running on the latest version of TrueNAS with your Jails at version 12.2-RELEASE-p2. It will most likely work on older versions also for FreeNAS 11.3 with Jails at either 11.3-RELEASE or 11.4-RELEASE.
If you're currently using OpenVPN with PIA you need to disable that which I will cover in the guide. If you don't have a VPN currently you can skip that part.
Make sure you have enabled to latest packages in your Jail. You can follow these two guides for that, depending if you're using a plugin or manual Jail.
Basic information
I am running my Jail with VNET and a static IP address. I haven't tested this with any other networking configuration so be aware of that.
I believe you need to enable the Berkeley Packet Filter if you're using DHCP but I'm not sure about that, maybe someone more knowledgeable can comment on that.
Making sure your Jail can create a VPN connection
In order for your Jail to create a VPN connection you need to enable
Under:
If you're currently using OpenVPN with PIA or another VPN provider you need to disable that. Also stop the OpenVPN service if it's currently running.
Alternatively you can edit
Stop Transmission
Before we continue make sure to stop the Transmission daemon.
Get a Mullvad account and subscription
After you made your account on Mullvad and paid for some server time you can generate a configuration file for WireGuard.
Go to: https://mullvad.net/en/account/#/wireguard-config/
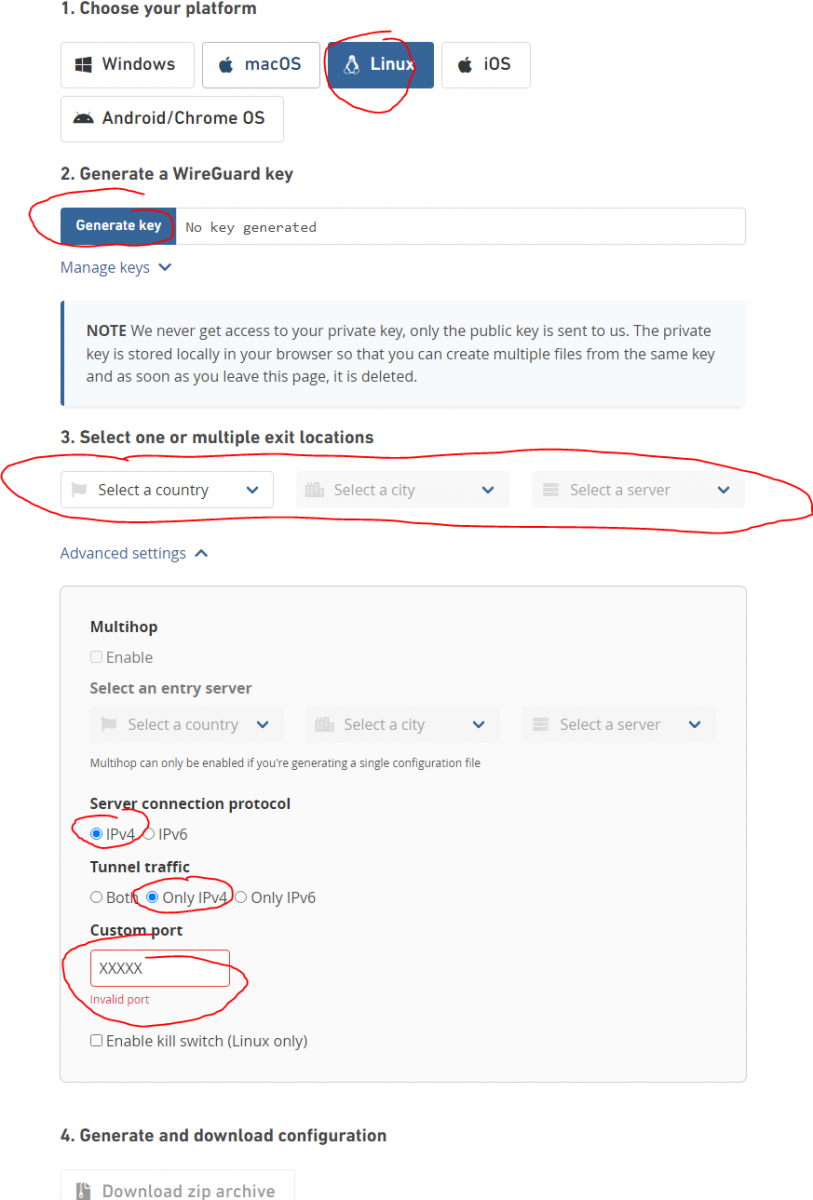
If you only selected a single server it should download a single plain text file, otherwise you will get an archive for each server. You need this later. Mine was very simple with this:
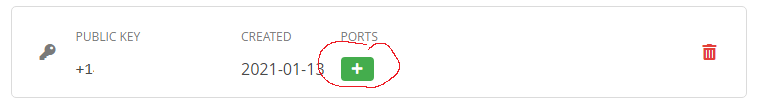
After downloading the file you need to generate a random port you can use for port forwarding.
Go to: https://mullvad.net/en/account/#/ports and click on the + icon next to your newly generated key to get a new random port. This is what we will configure in Transmission later
Install WireGuard
For the most part I've used this guide for installing WireGuard so credits to go that author I just skipped some parts. To make sure this guide is complete I will include all the steps I've done here.
Installing the package
Create a PostDown script to restore the default nameserver
I noticed after stopping WireGuard I could no longer resolve hostnames. WireGuard enables its own DNS server after the VPN connection is established. I created a basic PostDown script to restore my own nameserver.
Use your favorite editor to put contents below in the file. Normally I would be using my router's IP address. You can check what you have now by looking into
Create a WireGuard configuration file
We need to create a configuration file for WireGuard to use when you start the service
Put the contents of the configuration file you downloaded from Mullvad in this file except we need to add a line for the
Activate the WireGuard service
Type the following to lines to activate the WireGuard service on startup of the Jail and to point it to the right configuration file
Start WireGuard
Now you can start WireGuard and should give you a similar output:
Check if you have a connection
Check if you're using the Mullvad DNS server, look at the line that starts with
To get your new external IP address you can curl the Mullvad Connection check API
Configure IPFW to block internet traffic not going over WireGuard
To make sure Transmission can't connect to the internet when WireGuard goes down we will configure IPFW. I'm using the same IPFW rules from @dak180 that he uses for his Transmission Jail with PIA and OpenVPN.
Enable IPFW if that's not already the case.
Create the IPFW rules file.
Use your favorite text editor to put the contents below in the IPFW rules file. Make sure to set the variables correctly to match the user Transmission is running under and your LAN subnet.
Start Transmission and configure the forwarded port
Start Transmission again
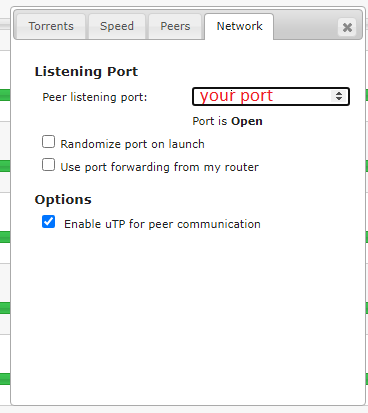
Go to the Transmission Web UI and click on the wrench icon bottom left. Switch to the Network tab and enter the randomly forwarded port you got from Mullvad.
Alternatively you can change the port from the command line
Or if you're using authorization for Transmission
That should be it!
Optional: firewall logging per rule
If you're having issues with IPFW you can enable logging for a rule. For example you can change:
To
If you get any hits on that rule it will be logged into
Prerequisites
This guide assumes you have a Transmission Jail running on the latest version of TrueNAS with your Jails at version 12.2-RELEASE-p2. It will most likely work on older versions also for FreeNAS 11.3 with Jails at either 11.3-RELEASE or 11.4-RELEASE.
If you're currently using OpenVPN with PIA you need to disable that which I will cover in the guide. If you don't have a VPN currently you can skip that part.
Make sure you have enabled to latest packages in your Jail. You can follow these two guides for that, depending if you're using a plugin or manual Jail.
- How to Correct package updates issues in an IOCAGE Plugin JAIL
- How to correct package update issues in a manual IOCAGE JAIL
12 whenever I encountered that and it seemed to have worked just fine.Basic information
I am running my Jail with VNET and a static IP address. I haven't tested this with any other networking configuration so be aware of that.
I believe you need to enable the Berkeley Packet Filter if you're using DHCP but I'm not sure about that, maybe someone more knowledgeable can comment on that.
Making sure your Jail can create a VPN connection
In order for your Jail to create a VPN connection you need to enable
allow_tun under the Custom Properties section. I've also disabled IPv6 in my Jail because I had problems with that while using OpenVPN. I don't know if this is nessacary for this setup, since I didn't change those settings I'm including them here in case you run into issues with that also.Under:
- Basic Properties: write in
noneat IPv6 Default Router - Jail Properties: enable
allow_raw_sockets - Network Properties: select
Disabledfor ip6 - Custom Properties: enable
allow_tun
If you're currently using OpenVPN with PIA or another VPN provider you need to disable that. Also stop the OpenVPN service if it's currently running.
Code:
# sysrc openvpn_enable="NO" # service openvpn stop
Alternatively you can edit
/etc/rc.conf manually to set OpenVPN to disabled. Completely removing the OpenVPN package is an option also, but I kept it installed just in case.Stop Transmission
Before we continue make sure to stop the Transmission daemon.
Code:
# service transmission stop
Get a Mullvad account and subscription
After you made your account on Mullvad and paid for some server time you can generate a configuration file for WireGuard.
Go to: https://mullvad.net/en/account/#/wireguard-config/
- I selected Linux
- Generate your key
- I selected a single country, city and server
- Opted for IPv4 only
- Left the custom port at default value that was filled in
- Download the configuration file
If you only selected a single server it should download a single plain text file, otherwise you will get an archive for each server. You need this later. Mine was very simple with this:
Code:
[Interface] PrivateKey = <private_key> Address = 10.xxx.xxx.xxx/32 DNS = 193.xxx.xxx.xxx [Peer] PublicKey = <public_key> AllowedIPs = 0.0.0.0/0 Endpoint = 193.xxx.xxx.xxx:xxxxx
After downloading the file you need to generate a random port you can use for port forwarding.
Go to: https://mullvad.net/en/account/#/ports and click on the + icon next to your newly generated key to get a new random port. This is what we will configure in Transmission later
Install WireGuard
For the most part I've used this guide for installing WireGuard so credits to go that author I just skipped some parts. To make sure this guide is complete I will include all the steps I've done here.
Installing the package
Code:
# pkg install wireguard
Create a PostDown script to restore the default nameserver
I noticed after stopping WireGuard I could no longer resolve hostnames. WireGuard enables its own DNS server after the VPN connection is established. I created a basic PostDown script to restore my own nameserver.
Code:
# touch /usr/local/etc/wireguard/postdown.sh # chmod+x /usr/local/etc/wireguard/postdown.sh
Use your favorite editor to put contents below in the file. Normally I would be using my router's IP address. You can check what you have now by looking into
/etc/resolv.conf and putting that in the script.Code:
#!/usr/local/bin/bash # Replace resolv.conf with original echo "# Generated by resolvconf search <local_domain> nameserver <local_dns>" > /etc/resolv.conf
Create a WireGuard configuration file
We need to create a configuration file for WireGuard to use when you start the service
Code:
touch /usr/local/etc/wireguard/wg0.conf
Put the contents of the configuration file you downloaded from Mullvad in this file except we need to add a line for the
PostDown script in the [Interface] section. Mine ended up looking like this:Code:
[Interface] PrivateKey = <private_key> Address = 10.xxx.xxx.xxx/32 DNS = 193.xxx.xxx.xxx PostDown = /usr/local/etc/wireguard/postdown.sh [Peer] PublicKey = <public_key> AllowedIPs = 0.0.0.0/0 Endpoint = 193.xxx.xxx.xxx:xxxxx
Activate the WireGuard service
Type the following to lines to activate the WireGuard service on startup of the Jail and to point it to the right configuration file
Code:
# sysrc wireguard_interfaces="wg0" # sysrc wireguard_enable="YES"
Start WireGuard
Now you can start WireGuard and should give you a similar output:
Code:
# service wireguard start [#] wireguard-go wg0 INFO: (wg0) 2021/01/13 14:42:11 Starting wireguard-go version 0.0.20201118 [#] wg setconf wg0 /tmp/tmp.3EiiwRXA/sh-np.ycuyMB [#] ifconfig wg0 inet 10.xxx.xxx.xxx/32 10.69.215.15 alias [#] ifconfig wg0 mtu 1420 [#] ifconfig wg0 up [#] resolvconf -a wg0 -x [#] route -q -n add -inet 0.0.0.0/1 -interface wg0 [#] route -q -n add -inet 128.0.0.0/1 -interface wg0 [#] route -q -n add -inet 193.xxx.xxx.xxx -gateway 192.168.178.1 [+] Backgrounding route monitor
Check if you have a connection
Code:
# ping truenas.com PING truenas.com (38.109.202.235): 56 data bytes 64 bytes from 38.109.202.235: icmp_seq=0 ttl=49 time=129.267 ms
Check if you're using the Mullvad DNS server, look at the line that starts with
;; SERVERCode:
# drill truenas.com ;; ->>HEADER<<- opcode: QUERY, rcode: NOERROR, id: 11097 ;; flags: qr rd ra ; QUERY: 1, ANSWER: 1, AUTHORITY: 2, ADDITIONAL: 0 ;; QUESTION SECTION: ;; truenas.com. IN A ;; ANSWER SECTION: truenas.com. 3552 IN A 38.109.202.235 ;; AUTHORITY SECTION: truenas.com. 172752 IN NS ns2.ixsystems.com. truenas.com. 172752 IN NS ns1.ixsystems.com. ;; ADDITIONAL SECTION: ;; Query time: 5 msec ;; SERVER: 193.xxx.xxx.xxx ;; WHEN: Wed Jan 13 14:45:36 2021 ;; MSG SIZE rcvd: 91
To get your new external IP address you can curl the Mullvad Connection check API
Code:
# curl https://am.i.mullvad.net/connected You are connected to Mullvad (server <server_name>). Your IP address is 193.xxx.xxx.xxx
Configure IPFW to block internet traffic not going over WireGuard
To make sure Transmission can't connect to the internet when WireGuard goes down we will configure IPFW. I'm using the same IPFW rules from @dak180 that he uses for his Transmission Jail with PIA and OpenVPN.
Enable IPFW if that's not already the case.
Code:
# sysrc firewall_enable="YES" # sysrc firewall_script="/etc/ipfw.rules" # sysrc firewall_logging="YES"
Create the IPFW rules file.
Code:
# touch /etc/ipfw.rules
Use your favorite text editor to put the contents below in the IPFW rules file. Make sure to set the variables correctly to match the user Transmission is running under and your LAN subnet.
Code:
#!/usr/local/bin/bash
# Config
# Set rules command prefix
cmd="ipfw -q add"
vpn="wg0"
user="transmission"
localLan="192.168.178.0/24"
# Flush out the list before we begin
ipfw -q -f flush
# Allow all local traffic on the loopback interface
${cmd} 00001 allow all from any to any via lo0
# Allow any connection to/from VPN interface
${cmd} 00010 allow all from any to any via ${vpn}
# Allow connection to/from LAN by User
${cmd} 00101 allow all from me to ${localLan} uid ${user}
${cmd} 00102 allow all from ${localLan} to me uid ${user}
# Deny any User connection outside LAN that does not use VPN
${cmd} 00103 deny all from any to any uid ${user}Start Transmission and configure the forwarded port
Start Transmission again
Code:
# service transmission start
Go to the Transmission Web UI and click on the wrench icon bottom left. Switch to the Network tab and enter the randomly forwarded port you got from Mullvad.
Alternatively you can change the port from the command line
Code:
transmission-remote -p <forwarded_port>
Or if you're using authorization for Transmission
Code:
transmission-remote --auth <user>:<password> -p <forwarded_port>
That should be it!
Optional: firewall logging per rule
If you're having issues with IPFW you can enable logging for a rule. For example you can change:
Code:
${cmd} 00103 deny all from any to any uid ${user}To
Code:
${cmd} 00103 deny log all from any to any uid ${user}If you get any hits on that rule it will be logged into
/var/log/security on the TrueNAS root environment; not in your Jail! I believe this can be fixed so the logging will happen inside the Jail but I haven't figured that out yet.
Last edited:
