I get a KeyError when I try to download the Client Certificate with the [Download Client Config] button.
The error dies not give me any hints on whats going wrong.
The overall scope is that I want to set up VPN server on my TrueNas Scale instance so I dont have to expose the GUI to the internet with ports.
I have a static IP address, added port forward to the VPN server and downloaded the OpenVPN app.
Is there any remedy for this issue with downloading the Client certificate?
I'm on the Bluefin version TrueNAS-SCALE-22.12-RC.1
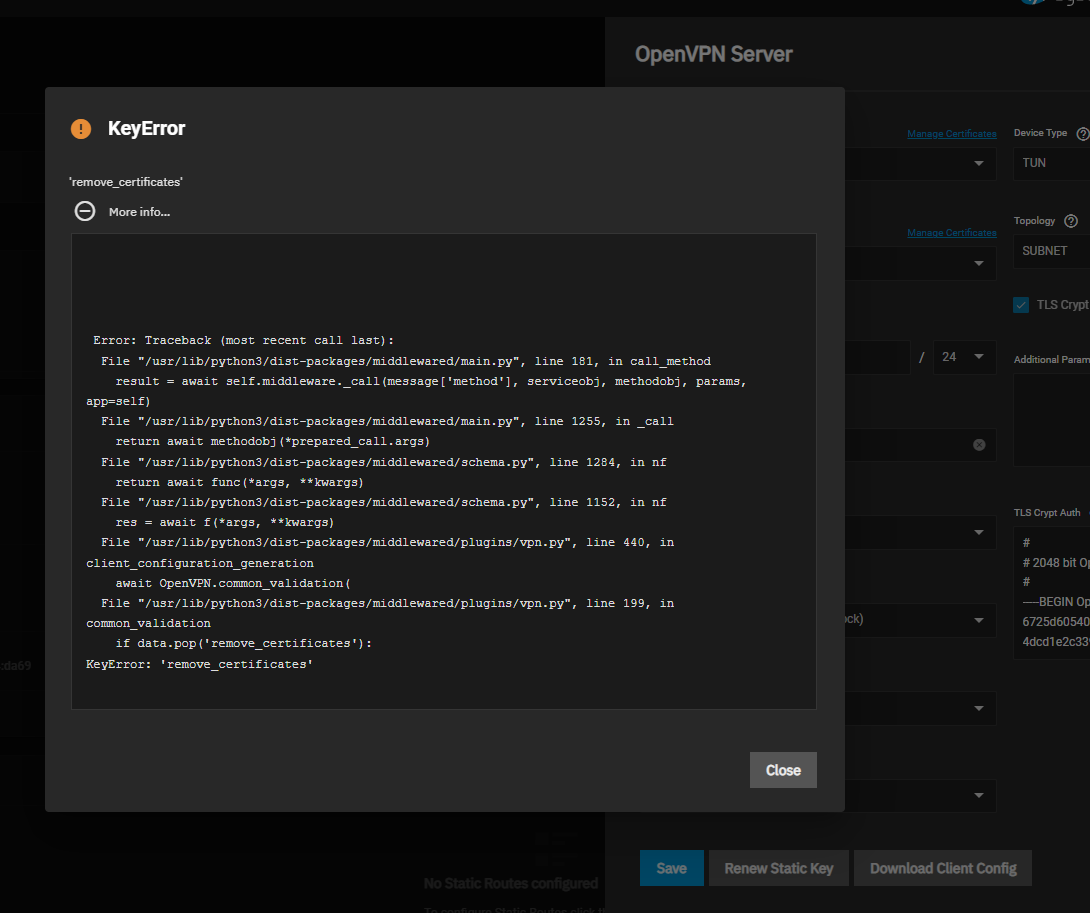
The error dies not give me any hints on whats going wrong.
The overall scope is that I want to set up VPN server on my TrueNas Scale instance so I dont have to expose the GUI to the internet with ports.
I have a static IP address, added port forward to the VPN server and downloaded the OpenVPN app.
Is there any remedy for this issue with downloading the Client certificate?
I'm on the Bluefin version TrueNAS-SCALE-22.12-RC.1
