impestrator
Dabbler
- Joined
- Feb 10, 2022
- Messages
- 26
Hello community,
I have the following problem with the "JDownloader App" (truecharts stable). As soon as I activate the OpenVPN option in the configuration, I am in the deployment loop and accordingly the web frontend is not accessible.
If I disable the OpenVPN option, the container starts and I can log in to the webfront normally.
Basically I change the following:
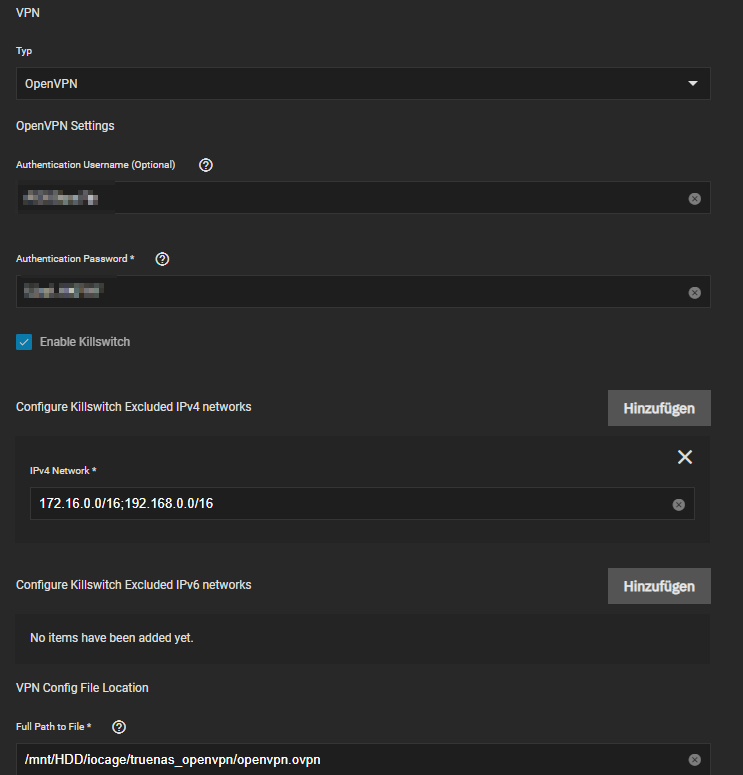
All other settings are by default.
Do you have any idea what I am doing wrong? Does the container start normal if the OpenVPN config file is corrupt?
Regards
I have the following problem with the "JDownloader App" (truecharts stable). As soon as I activate the OpenVPN option in the configuration, I am in the deployment loop and accordingly the web frontend is not accessible.
Code:
In the events I then see the following: Back-off restarting failed container Created container openvpn Container image "tccr.io/truecharts/openvpn-client:latest@sha256:1f83decdf614cbf48e2429921b6f0efa0e825f447f5c510b65bc90f660227688" already present Started container openvpn Started container jdownloader2 Created container jdownloader2
If I disable the OpenVPN option, the container starts and I can log in to the webfront normally.
Basically I change the following:
All other settings are by default.
Do you have any idea what I am doing wrong? Does the container start normal if the OpenVPN config file is corrupt?
Regards
