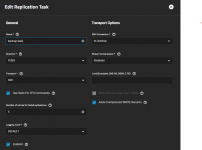
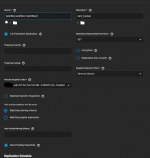
I have an unencrypted source dataset that I would like to replicate in a remote truenas but in an encrypted form.
My problem is that after the first replication with remote encryption, the remote dataset is unlocked.
How can I get replication to work but without leaving remote data exposed?
Where can I find the right RTFM?
Thanks!
My problem is that after the first replication with remote encryption, the remote dataset is unlocked.
How can I get replication to work but without leaving remote data exposed?
Where can I find the right RTFM?
Thanks!