guemi
Dabbler
- Joined
- Apr 16, 2020
- Messages
- 48
Hello,
I recently reinstalled my home NAS from Core to SCALE as we're in the process of switching to SCALE at work for our storage systems since Linux has better compability with our hardware.
I run a very simple setup at home. Two samba shares, one needs to be fairly locked down because I use a sync app on my phone to instantly upload any pictures I take via samba to my NAS as a backup.
It's worked for years and it's been smooth. Not so much with SCALE.
I installed Scale, imported the Pools, the datasets for previous shares are there - so far so good.
Create a new local user on the NAS simply called "cloudsvc".
Enabled it for Samba Authentication.
Create a SMB share, left S-1-1-0 at full control since I'll be doing permissions on the dataset level - just as I did in CORE.
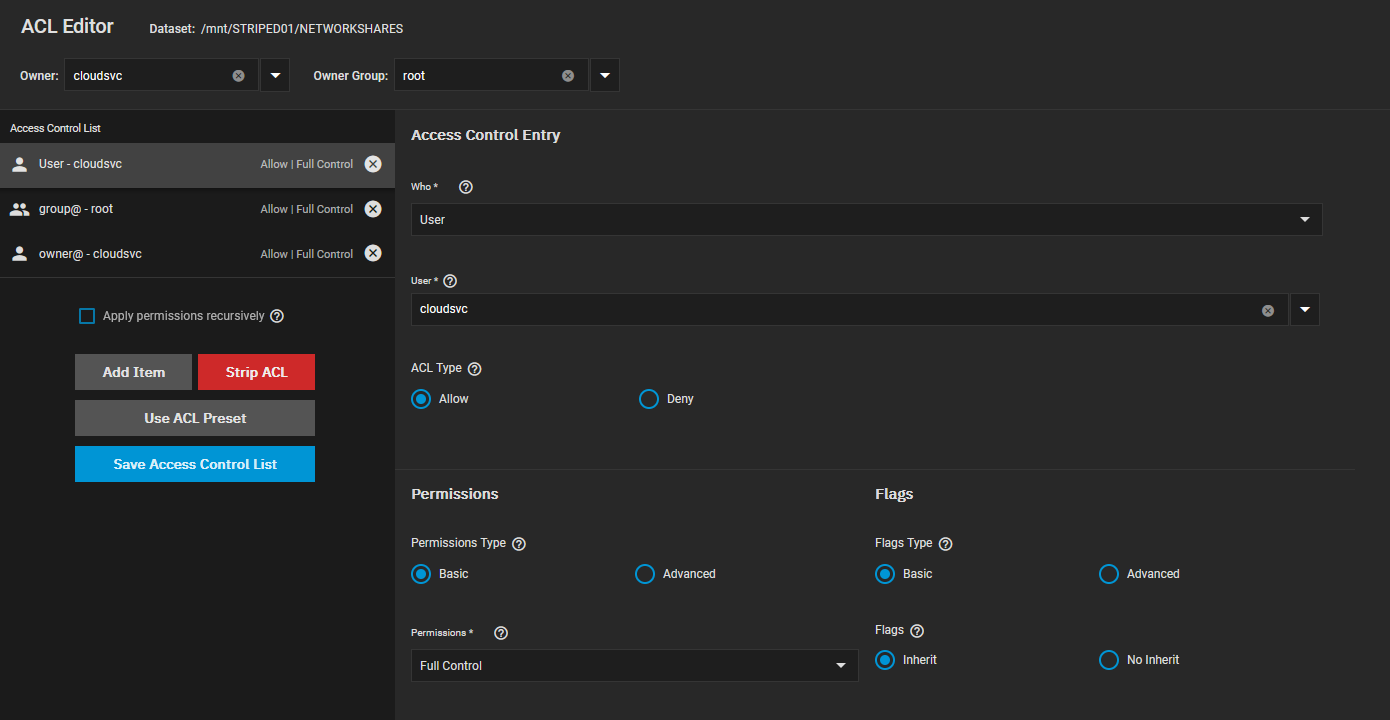
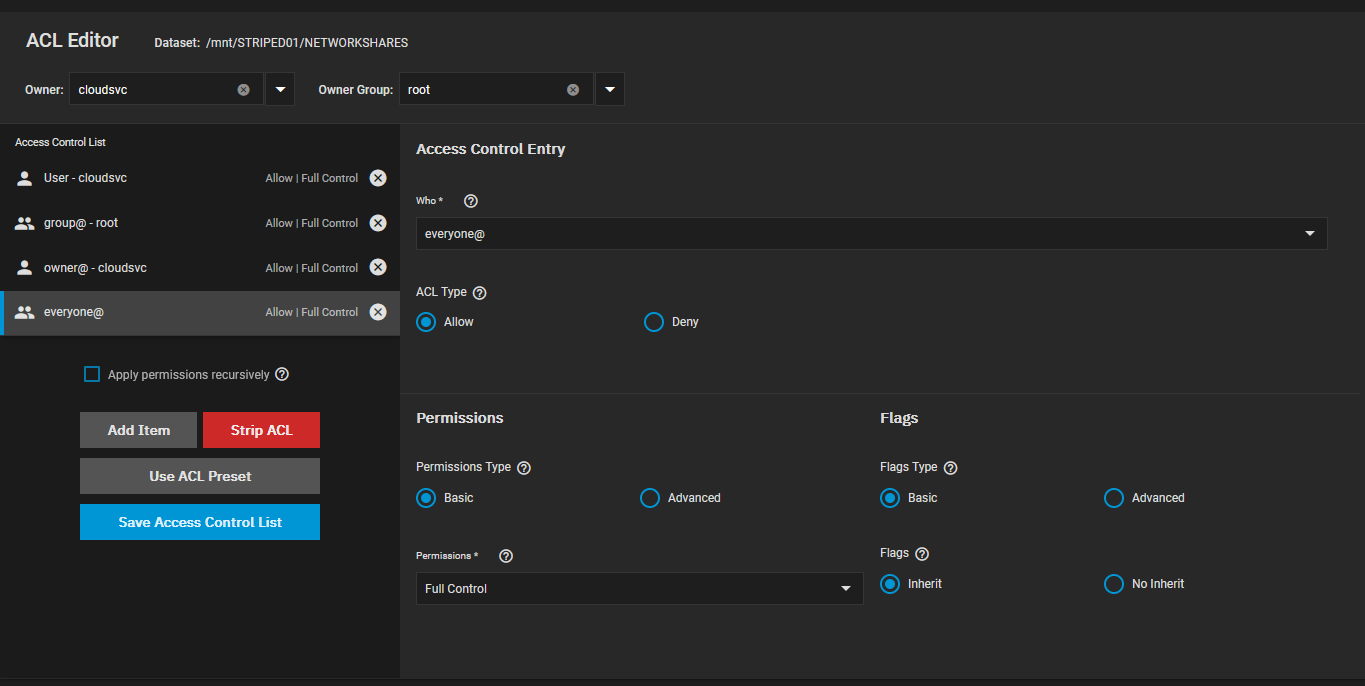
The folder shared is /mnt/STRIPED01/NETWORKSHARES/Cloud and the NETWORKSHARES dataset ACL looks like the following:
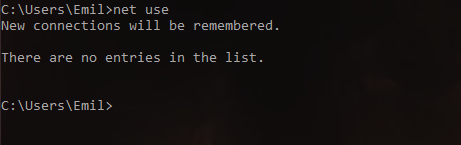
Go to windows, emty credential manager, delete all previous network shares with net use command for everything to be as good as new:
Try to go to \\10.10.10.100 - gets prompted for username / password - enter cloudsvc and password:
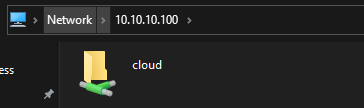
Network share is visible, and the samba log shows the auth and confirms it's OK and that the local INTERSTELLAR (NAS HOSTNAME) user was used:
{"timestamp": "2022-07-10T13:11:40.246925+0200", "type": "Authentication", "Authentication": {"version": {"major": 1, "minor": 2}, "eventId": 4624, "logonId": "0", "logonType": 3, "status": "NT_STATUS_OK", "localAddress": "ipv4:10.10.10.100:445", "remoteAddress": "ipv4:10.10.10.101:64919", "serviceDescription": "SMB2", "authDescription": null, "clientDomain": ".", "clientAccount": "cloudsvc", "workstation": "TITAN", "becameAccount": "cloudsvc", "becameDomain": "INTERSTELLAR", "becameSid": "S-1-5-21-3666039284-1560195053-518253317-20066", "mappedAccount": "cloudsvc", "mappedDomain": ".", "netlogonComputer": null, "netlogonTrustAccount": null, "netlogonNegotiateFlags": "0x00000000", "netlogonSecureChannelType": 0, "netlogonTrustAccountSid": null, "passwordType": "NTLMv2", "duration": 4763}}
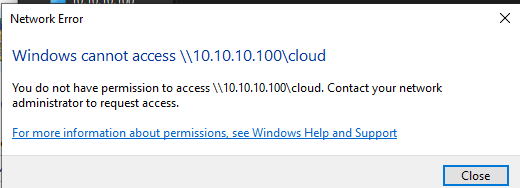
Try to enter the network share aaaaaand boom:
But if we added @Everyone with full permissions on the dataset?
Then it works great. And of course it does, it's never checking any permissions.
getfacl confirms the user has access and is even OWNED by the user I am trying to connect with:
root@INTERSTELLAR[~]# getfacl /mnt/STRIPED01/NETWORKSHARES
getfacl: Removing leading '/' from absolute path names
# file: mnt/STRIPED01/NETWORKSHARES
# owner: cloudsvc
# group: root
user::rwx
group::rwx
other::rwx
root@INTERSTELLAR[~]# ls -lh /mnt/STRIPED01/NETWORKSHARES
total 8.5K
drwxrwxrwx 12 cloudsvc root 17 May 7 12:05 CLOUD
This is the exact same process I've done on multiple CORE installs and it just works - Is SCALE ACL's just not ready to be used with Samba properly?
P.S
When going through SMB and hitting "View Filesystem ACL" in the UI, I get to /mnt/STRIPED01/NETWORKSHARES/CLOUD which is the actual folder that's being shared - but I made sure to mirror the settings of the NETWORKSHARES ACL on to that one, so there isn't a conflict there either.
I also tried directly sharing the path /mnt/STRIPED01/NETWORKSHARES with SMB just in case - but no dice.
I recently reinstalled my home NAS from Core to SCALE as we're in the process of switching to SCALE at work for our storage systems since Linux has better compability with our hardware.
I run a very simple setup at home. Two samba shares, one needs to be fairly locked down because I use a sync app on my phone to instantly upload any pictures I take via samba to my NAS as a backup.
It's worked for years and it's been smooth. Not so much with SCALE.
I installed Scale, imported the Pools, the datasets for previous shares are there - so far so good.
Create a new local user on the NAS simply called "cloudsvc".
Enabled it for Samba Authentication.
Create a SMB share, left S-1-1-0 at full control since I'll be doing permissions on the dataset level - just as I did in CORE.
The folder shared is /mnt/STRIPED01/NETWORKSHARES/Cloud and the NETWORKSHARES dataset ACL looks like the following:
Go to windows, emty credential manager, delete all previous network shares with net use command for everything to be as good as new:
Try to go to \\10.10.10.100 - gets prompted for username / password - enter cloudsvc and password:
Network share is visible, and the samba log shows the auth and confirms it's OK and that the local INTERSTELLAR (NAS HOSTNAME) user was used:
{"timestamp": "2022-07-10T13:11:40.246925+0200", "type": "Authentication", "Authentication": {"version": {"major": 1, "minor": 2}, "eventId": 4624, "logonId": "0", "logonType": 3, "status": "NT_STATUS_OK", "localAddress": "ipv4:10.10.10.100:445", "remoteAddress": "ipv4:10.10.10.101:64919", "serviceDescription": "SMB2", "authDescription": null, "clientDomain": ".", "clientAccount": "cloudsvc", "workstation": "TITAN", "becameAccount": "cloudsvc", "becameDomain": "INTERSTELLAR", "becameSid": "S-1-5-21-3666039284-1560195053-518253317-20066", "mappedAccount": "cloudsvc", "mappedDomain": ".", "netlogonComputer": null, "netlogonTrustAccount": null, "netlogonNegotiateFlags": "0x00000000", "netlogonSecureChannelType": 0, "netlogonTrustAccountSid": null, "passwordType": "NTLMv2", "duration": 4763}}
Try to enter the network share aaaaaand boom:
But if we added @Everyone with full permissions on the dataset?
Then it works great. And of course it does, it's never checking any permissions.
getfacl confirms the user has access and is even OWNED by the user I am trying to connect with:
root@INTERSTELLAR[~]# getfacl /mnt/STRIPED01/NETWORKSHARES
getfacl: Removing leading '/' from absolute path names
# file: mnt/STRIPED01/NETWORKSHARES
# owner: cloudsvc
# group: root
user::rwx
group::rwx
other::rwx
root@INTERSTELLAR[~]# ls -lh /mnt/STRIPED01/NETWORKSHARES
total 8.5K
drwxrwxrwx 12 cloudsvc root 17 May 7 12:05 CLOUD
This is the exact same process I've done on multiple CORE installs and it just works - Is SCALE ACL's just not ready to be used with Samba properly?
P.S
When going through SMB and hitting "View Filesystem ACL" in the UI, I get to /mnt/STRIPED01/NETWORKSHARES/CLOUD which is the actual folder that's being shared - but I made sure to mirror the settings of the NETWORKSHARES ACL on to that one, so there isn't a conflict there either.
I also tried directly sharing the path /mnt/STRIPED01/NETWORKSHARES with SMB just in case - but no dice.
