Hi there, I've checked around and it seems like a few people have had this issue in the past with little to no resolution.. just random success here and there with no documentation...
I have OpenVPN server running on my OPNsense firewall. My phone, laptop and desktop are all capable of connecting to the VPN successfully.
However, I cannot connect the TrueNAS box to the VPN using the OpenVPN client under services.
I've setup the CA and Certs as documented by a few others on this forum with no success.
I do have the OPNsense set to local directory username / password authentication. I assume when it succesfully connects to the VPN I'll get to enter those credentials...
On a side note, are my settings 'Secure enough' or should I up them to AES-256-CBC, SHA512 etc? I've heard that leaving the default port 1194 isn't entirely wise, so I'll change that when or if I get this figured out.
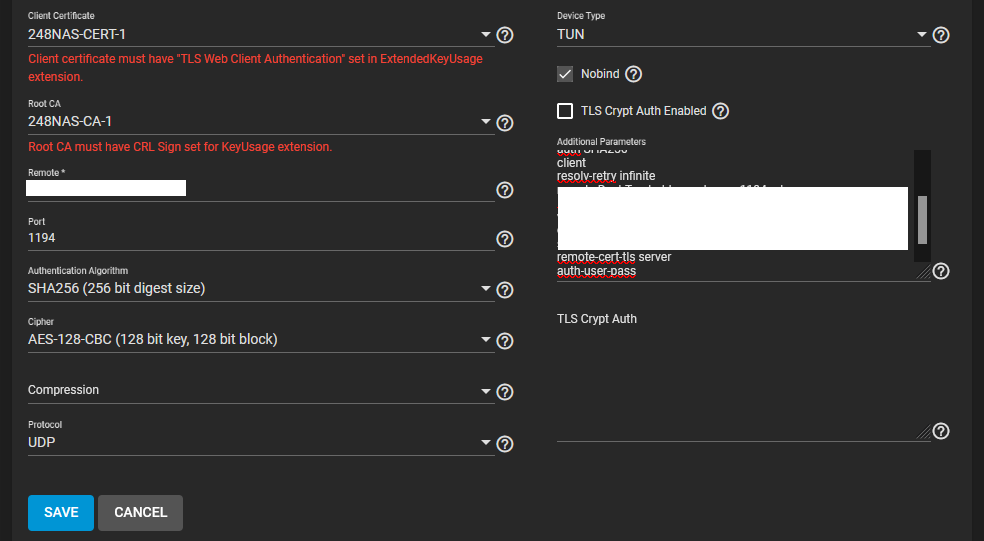
I have OpenVPN server running on my OPNsense firewall. My phone, laptop and desktop are all capable of connecting to the VPN successfully.
However, I cannot connect the TrueNAS box to the VPN using the OpenVPN client under services.
I've setup the CA and Certs as documented by a few others on this forum with no success.
I do have the OPNsense set to local directory username / password authentication. I assume when it succesfully connects to the VPN I'll get to enter those credentials...
On a side note, are my settings 'Secure enough' or should I up them to AES-256-CBC, SHA512 etc? I've heard that leaving the default port 1194 isn't entirely wise, so I'll change that when or if I get this figured out.
cipher AES-128-CBC
auth SHA256
client
resolv-retry infinite
remote someobscured.domainontheinternet.com 1194 udp
lport 0
verify-x509-name " ------------ , CN=OpenVPN-Cert" subject
remote-cert-tls server
auth-user-pass
auth SHA256
client
resolv-retry infinite
remote someobscured.domainontheinternet.com 1194 udp
lport 0
verify-x509-name " ------------ , CN=OpenVPN-Cert" subject
remote-cert-tls server
auth-user-pass
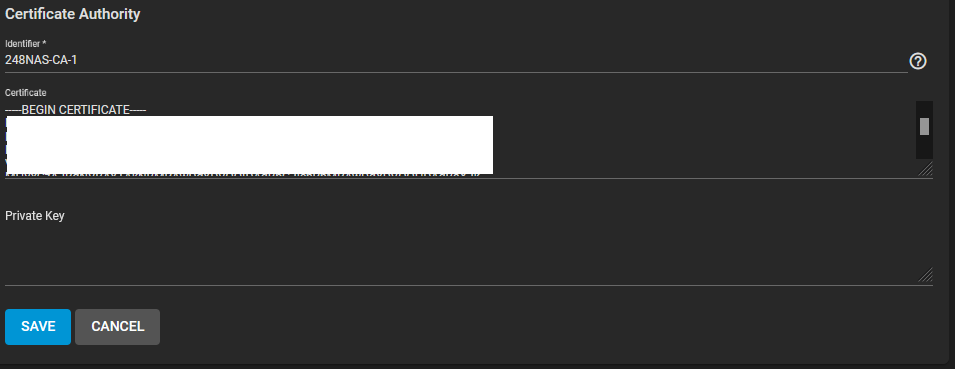
I inserted what was inside the <ca> </ca>
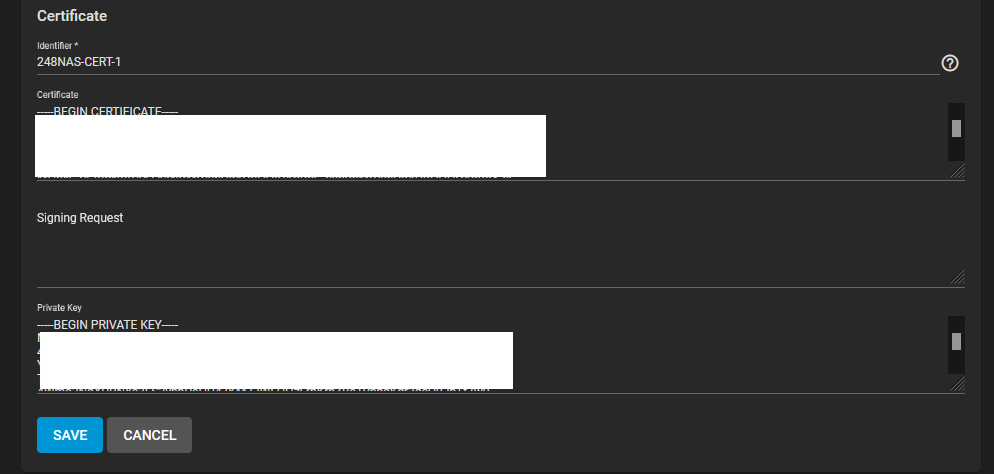
I inserted what was inside the <cert> </cert> and <key> </key>
Last edited by a moderator:

