keboose
Explorer
- Joined
- Mar 5, 2016
- Messages
- 92
It looks like your clients have never connected. If you look at mine:
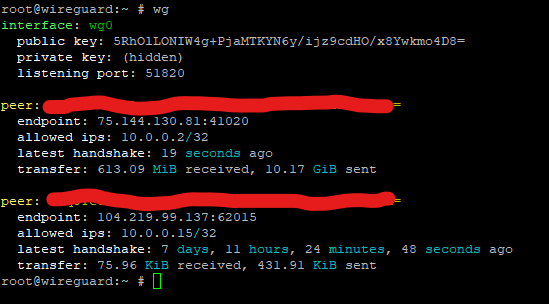
You'll see it has info on the last client that connected. Yours lacking info means the client never really completed the handshake procedure, so it never connected (even though the client says its connected, this is a massive shortcoming of all the official Wireguard clients: It shouldn't count as 'connected' until AFTER the handshake.) If you look at the log when you turn on the VPN on your client, what do you see?
You'll see it has info on the last client that connected. Yours lacking info means the client never really completed the handshake procedure, so it never connected (even though the client says its connected, this is a massive shortcoming of all the official Wireguard clients: It shouldn't count as 'connected' until AFTER the handshake.) If you look at the log when you turn on the VPN on your client, what do you see?
