Hi,
I have an old GELI encrypted pool. One of the disk failed. I got a new disk and I followed the instruction from [1]. However, the replacement procedure asks for a passphrase which I don't have; I only have a key file without a passphrase.
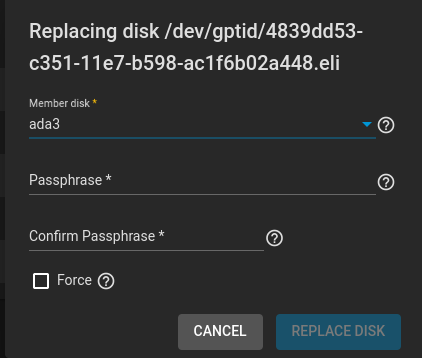
How does one replace a GELI encrypted disk in TrueNAS Core 13? The only thing mentioned in the current disk replacement documentation about GELI is
which is not helpful.
[1]: https://www.truenas.com/docs/core/coretutorials/storage/disks/diskreplace/
Best,
-F
I have an old GELI encrypted pool. One of the disk failed. I got a new disk and I followed the instruction from [1]. However, the replacement procedure asks for a passphrase which I don't have; I only have a key file without a passphrase.
How does one replace a GELI encrypted disk in TrueNAS Core 13? The only thing mentioned in the current disk replacement documentation about GELI is
Can I replace a disk in a GELI-encrypted (Legacy) pool?
Although GELI encryption is deprecated, TrueNAS implements GELI encryption during a “GELI-Encrypted (Legacy) pool” disk replacement. TrueNAS uses GELI encryption for the lifetime of that pool, even after replacement.
which is not helpful.
[1]: https://www.truenas.com/docs/core/coretutorials/storage/disks/diskreplace/
Best,
-F
