Hmm is there are way to delete/edit my post above? Made some changes/fixes to my post and want to update as follows:
Sharing to all my personal experience:
So based on input from this thread and others, I think everything is working the way I want where ALL traffic goes through the VPN. I've tried signing into my VPN via my mobile wireless (LTE) connection from my Samsung Galaxy S10+ using Android OpenVPN and it appears to be working. I had to do the following to get it to work:
1) Setup the OpenVPN CA using the OpenVPN CA template.
2) Setup the OpenVPN Server Certificate using the OpenVPN Server template.
3) Setup the OpenVPN Client Certificate using the OpenVPN Client template.
(There is a video walkthrough guide for steps 1-3 above on YouTube.)
4) Forward the appropriate port from your router to your TrueNAS server IP. 1194 is the default port so I just stuck with that. My TrueNAS server's IP on my LAN is 192.168.0.2 (yes, I know, I should change it to something else that is unlikely to be used in the outside world... I will in due time.
Once I confirmed the above was working and I could connect from my phone to my VPN, I disconnected and got to the real work, namely routing everything through the VPN, which is where I think most people get the hangup.
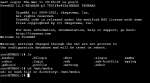
1) From TrueNAS WebGUI, go to System->Tunables and add the following 3 tunables:
Code:
Variable: firewall_enable
Value: yes
Type: rc.conf
Description: enable firewall
Code:
Variable: gateway_enable
Value: yes
Type: rc.conf
Description: enable gateway
Code:
Variable: firewall_script
Value: /mnt/NAME_OF_POOL/ipfwrules.sh
Type: rc.conf
Description: ipfw script to execute at boot time. I put it in the pool to ensure that it carries should I have to reinstall and restore from a config.
2) Open a console/shell. Personally, I SSH in with PuTTY as root. But the WebGUI Shell will suffice.
3) input the following line by line into the shell. Change 10.8.8.0/24 to whatever you configured OpenSSH to use for VPN devices and NAME_OF_POOL to the correct location of your ipfwrules.sh that you decided above in the Tunables.
Code:
cd /mnt/NAME_OF_POOL
echo ipfw -q -f flush > ipfwrules.sh
echo ipfw -q nat 1 config if re0 >> ipfwrules.sh
echo ipfw -q add nat 1 all from 10.8.8.0/24 to any out via re0 >> ipfwrules.sh
echo ipfw -q add nat 1 all from any to any in via re0 >> ipfwrules.sh
chmod 755 ipfwrules.sh
4) Under the OpenVPN server settings, put the following in additional parameters:
Code:
push "redirect-gateway def1"
push "remote-gateway vpn_server_ip"
push "dhcp-option DNS 8.8.8.8"
push "dhcp-option DNS 8.8.4.4"
duplicate-cn
The last line for "duplicate-cn" is only if you want to have the same user client/certificate be used simultaneously by multiple devices. (i.e. I use the same client configuration for my laptop and my smartphone, so this option must be included. Otherwise, OpenVPN will assign the same IP address to both devices and cause a conflict and cease working correctly.)
5) Save and download the new Client Configuration, choosing the correct Certificate.
6) Restart the TrueNAS server
7) EDIT the client configuration file with a text editor and change the line that starts with "remote" to reflect the correct address whether it is a static IP address or the Dynamic DNS you have setup. I use dynamic DNS so mine looks like so:
Code:
remote "mydomain.privatedns.org"
8) Test connect. Hopefully it works for you!
Note how I did NOT make any configuration changes to my router other than the port forwarding. I do NOT have any static routes setup anywhere, and I believe this should work fine as the TrueNAS server is performing NAT for anything originating to and going back to a VPN device.
Good luck!