I want to move my second TrueNAS server to a remote location and use the OpenVPN client to have it connect to my LAN. That way it can be discoverable by the devices in my LAN and use it as remote target for the replication tasks of my main TrueNAS server.
I followed the instructions on https://www.truenas.com/community/resources/truenas-and-openvpn-client-configuration.158/ and, for the most part, i think i got it set correctly.
Yesterday i was doing some testings and i connected that system to an external network. It seems that it can find and connect to the OpenVPN server in my LAN because i was able to access its web GUI from a PC in my LAN.
However, my main TrueNAS server in my LAN could not connect to the second TrueNAS server that was using the OpenVPN client. I couldn’t connect to it via SSH either nor could I ping it. Do any of you know what i may be missing? Or how can this be diagnosed better in order for me to find a solution?
My other OpenVPN clients can connect to my OpenVPN server without a problem, this is what makes me believe is something to do with the settings inside TrueNAS.
My LAN network is 10.0.0.0/24
My LAN2 network is 10.0.20.0/24 (currently unused)
My OpenVPN Tunnel network is 10.40.0.0/24
The OpenVPN server is installed on a PFSense router and is set to establish the routes of the OpenVPN server via the following custom options:
The following is the client’s ovpn file (created by the OpenVPN server):
And this is the content of the TrueNAS OpenVPN Client conf file located at
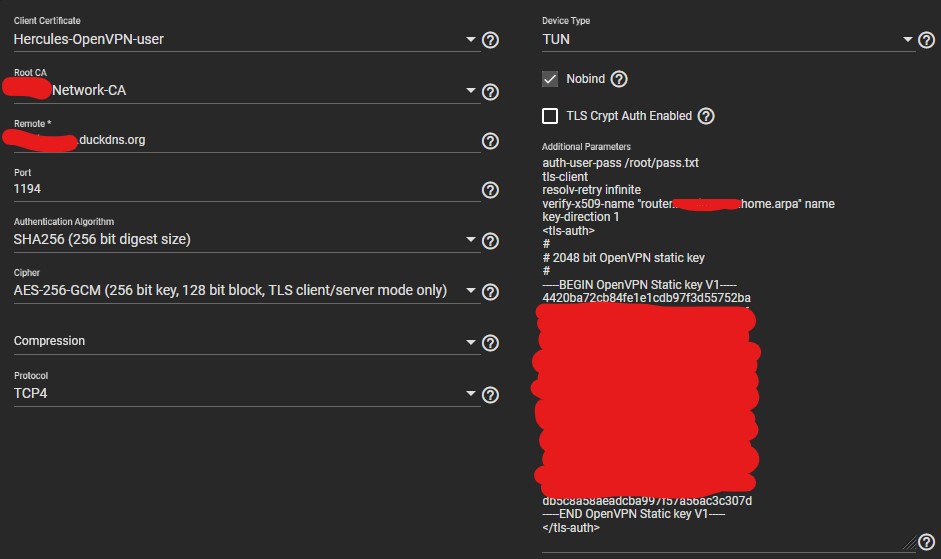
Lastly, these are my TrueNAS Client settings set via the GUI
Any suggestions are welcome.
I followed the instructions on https://www.truenas.com/community/resources/truenas-and-openvpn-client-configuration.158/ and, for the most part, i think i got it set correctly.
Yesterday i was doing some testings and i connected that system to an external network. It seems that it can find and connect to the OpenVPN server in my LAN because i was able to access its web GUI from a PC in my LAN.
However, my main TrueNAS server in my LAN could not connect to the second TrueNAS server that was using the OpenVPN client. I couldn’t connect to it via SSH either nor could I ping it. Do any of you know what i may be missing? Or how can this be diagnosed better in order for me to find a solution?
My other OpenVPN clients can connect to my OpenVPN server without a problem, this is what makes me believe is something to do with the settings inside TrueNAS.
My LAN network is 10.0.0.0/24
My LAN2 network is 10.0.20.0/24 (currently unused)
My OpenVPN Tunnel network is 10.40.0.0/24
The OpenVPN server is installed on a PFSense router and is set to establish the routes of the OpenVPN server via the following custom options:
push "route 10.0.0.0 255.255.255.0";
push "route 10.0.20.0 255.255.255.0";
The following is the client’s ovpn file (created by the OpenVPN server):
dev tun
persist-tun
persist-key
data-ciphers AES-256-GCM:AES-128-GCM:CHACHA20-POLY1305:AES-256-CBC
data-ciphers-fallback AES-256-CBC
auth SHA256
tls-client
client
resolv-retry infinite
remote ABCDEF.duckdns.org 1194 tcp4
setenv opt block-outside-dns
nobind
verify-x509-name "router.ABCDEF.home.arpa" name
auth-user-pass
remote-cert-tls server
<ca>
-----BEGIN CERTIFICATE-----
MIIEMzCCAxugAwIBAgIBADANBgkqhkiG9w0BAQsFADBvMR4wHAYDVQQDExVSb3Nz
...
...
8UF9YbZV4c2Q9wySC/gDC3HmT3lj+08=
-----END CERTIFICATE-----
</ca>
<cert>
-----BEGIN CERTIFICATE-----
MIIEhzCCA2+gAwIBAgIBJDANBgkqhkiG9w0BAQsFADBvMR4wHAYDVQQDExVSb3Nz
...
...
aCeihczmgMYatxVGaobP8Y/kkU/NR0oMrc4T3TU9kfgaKbrilc1yrdn7apJ27hhr
UgboHhJouQn3nwA=
-----END CERTIFICATE-----
</cert>
<key>
-----BEGIN PRIVATE KEY-----
MIIEvAIBADANBgkqhkiG9w0BAQEFAASCBKYwggSiAgEAAoIBAQDIXiBbfPVjZTHb
...
...
d01rnP1LpudHBHJigIc0XegW0/PGmgoLqAF6c9ufMX+nXjP6J1OIUBm5q7UfXlaz
MXFBQxKX5hvm77oF5B48Ig==
-----END PRIVATE KEY-----
</key>
key-direction 1
<tls-auth>
#
# 2048 bit OpenVPN static key
#
-----BEGIN OpenVPN Static key V1-----
4420ba72cb84fe1e1cdb97f3d55752ba
...
...
db5c8a58aeadcba997f57a56ac3c307d
-----END OpenVPN Static key V1-----
</tls-auth>
persist-tun
persist-key
data-ciphers AES-256-GCM:AES-128-GCM:CHACHA20-POLY1305:AES-256-CBC
data-ciphers-fallback AES-256-CBC
auth SHA256
tls-client
client
resolv-retry infinite
remote ABCDEF.duckdns.org 1194 tcp4
setenv opt block-outside-dns
nobind
verify-x509-name "router.ABCDEF.home.arpa" name
auth-user-pass
remote-cert-tls server
<ca>
-----BEGIN CERTIFICATE-----
MIIEMzCCAxugAwIBAgIBADANBgkqhkiG9w0BAQsFADBvMR4wHAYDVQQDExVSb3Nz
...
...
8UF9YbZV4c2Q9wySC/gDC3HmT3lj+08=
-----END CERTIFICATE-----
</ca>
<cert>
-----BEGIN CERTIFICATE-----
MIIEhzCCA2+gAwIBAgIBJDANBgkqhkiG9w0BAQsFADBvMR4wHAYDVQQDExVSb3Nz
...
...
aCeihczmgMYatxVGaobP8Y/kkU/NR0oMrc4T3TU9kfgaKbrilc1yrdn7apJ27hhr
UgboHhJouQn3nwA=
-----END CERTIFICATE-----
</cert>
<key>
-----BEGIN PRIVATE KEY-----
MIIEvAIBADANBgkqhkiG9w0BAQEFAASCBKYwggSiAgEAAoIBAQDIXiBbfPVjZTHb
...
...
d01rnP1LpudHBHJigIc0XegW0/PGmgoLqAF6c9ufMX+nXjP6J1OIUBm5q7UfXlaz
MXFBQxKX5hvm77oF5B48Ig==
-----END PRIVATE KEY-----
</key>
key-direction 1
<tls-auth>
#
# 2048 bit OpenVPN static key
#
-----BEGIN OpenVPN Static key V1-----
4420ba72cb84fe1e1cdb97f3d55752ba
...
...
db5c8a58aeadcba997f57a56ac3c307d
-----END OpenVPN Static key V1-----
</tls-auth>
And this is the content of the TrueNAS OpenVPN Client conf file located at
/usr/local/etc/openvpn/client/ after i manually added all the settings via the GUIclient
dev tun
#dev-type tun -FIXME: This does not work, it is an openvpn issue in FreeBSD
proto tcp4
port 1194
remote ABCDEF.duckdns.org
user nobody
group nobody
persist-key
persist-tun
ca /etc/certificates/CA/ABCDEF-Network-CA.crt
cert /etc/certificates/Hercules-OpenVPN-user.crt
key /etc/certificates/Hercules-OpenVPN-user.key
verb 3
remote-cert-tls server
auth SHA256
cipher AES-256-GCM
nobind
auth-user-pass /root/pass.txt
tls-client
resolv-retry infinite
verify-x509-name "router.ABCDEF.home.arpa" name
key-direction 1
<tls-auth>
#
# 2048 bit OpenVPN static key
#
-----BEGIN OpenVPN Static key V1-----
4420ba72cb84fe1e1cdb97f3d55752ba
...
...
...
db5c8a58aeadcba997f57a56ac3c307d
-----END OpenVPN Static key V1-----
</tls-auth>
dev tun
#dev-type tun -FIXME: This does not work, it is an openvpn issue in FreeBSD
proto tcp4
port 1194
remote ABCDEF.duckdns.org
user nobody
group nobody
persist-key
persist-tun
ca /etc/certificates/CA/ABCDEF-Network-CA.crt
cert /etc/certificates/Hercules-OpenVPN-user.crt
key /etc/certificates/Hercules-OpenVPN-user.key
verb 3
remote-cert-tls server
auth SHA256
cipher AES-256-GCM
nobind
auth-user-pass /root/pass.txt
tls-client
resolv-retry infinite
verify-x509-name "router.ABCDEF.home.arpa" name
key-direction 1
<tls-auth>
#
# 2048 bit OpenVPN static key
#
-----BEGIN OpenVPN Static key V1-----
4420ba72cb84fe1e1cdb97f3d55752ba
...
...
...
db5c8a58aeadcba997f57a56ac3c307d
-----END OpenVPN Static key V1-----
</tls-auth>
Any suggestions are welcome.
