Ive built (and am still testing/messing with), a large freenas server. It will have some personal and my own work files.
Below is most likely something i will not do, but wanted to get feedback from others. My question is only interms of storage security (ie NFS / iSCSI or cifs)
On the same rack as my FN machine, i will have a bare metal linux box, hosting a public facing, public accessible website.
This website/webserver will have about 4gb of (disk) content to serve visitors. I would LIKE to save some power/heat and have this 4tb of data stored on the FN machine (in its own zpool / dataset) and served to the "Bare metal public webserver" via NFS or iSCSI via a dedicated NIC / vlan.
My concern is the Bare metal public webserver gets fully exploited (ie an attacker has full root shell on this machine), and can then leverage the NFS or iSCSI share to gain access to other files on the FN box, or the FN box itself.
ie via:
https://www.securitynewspaper.com/2018/04/25/use-weak-nfs-permissions-escalate-linux-privileges/
(i realize FN does use the "nfsnobody" group, but im sure they are other nfs or iscsi exploits)
Would it be better if i ran "Bare metal public webserver" as a ESXi host, and then use nfs on ESXi to provide the httpd VM a 4tb datastore? (ie the web based attacker, would have to get exploit/access to ESXi first, to then pivot/see the FN NFS share).
Due to these reason (and that i will have other important data elsewhere on my FN box), i will most likely just run a few 2 or 4tb disks on the baremetal host and have it only connected to a separate, isolated network to the internet. But i wanted to get input. How do enterprises or large providers deal with NAS/SAN security in terms of the host accessing the SAN/NAS share getting exploited?
tks
rough/quick idea of how i would physically segment, hypothetically (click to enlarge):
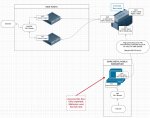
Below is most likely something i will not do, but wanted to get feedback from others. My question is only interms of storage security (ie NFS / iSCSI or cifs)
On the same rack as my FN machine, i will have a bare metal linux box, hosting a public facing, public accessible website.
This website/webserver will have about 4gb of (disk) content to serve visitors. I would LIKE to save some power/heat and have this 4tb of data stored on the FN machine (in its own zpool / dataset) and served to the "Bare metal public webserver" via NFS or iSCSI via a dedicated NIC / vlan.
My concern is the Bare metal public webserver gets fully exploited (ie an attacker has full root shell on this machine), and can then leverage the NFS or iSCSI share to gain access to other files on the FN box, or the FN box itself.
ie via:
https://www.securitynewspaper.com/2018/04/25/use-weak-nfs-permissions-escalate-linux-privileges/
(i realize FN does use the "nfsnobody" group, but im sure they are other nfs or iscsi exploits)
Would it be better if i ran "Bare metal public webserver" as a ESXi host, and then use nfs on ESXi to provide the httpd VM a 4tb datastore? (ie the web based attacker, would have to get exploit/access to ESXi first, to then pivot/see the FN NFS share).
Due to these reason (and that i will have other important data elsewhere on my FN box), i will most likely just run a few 2 or 4tb disks on the baremetal host and have it only connected to a separate, isolated network to the internet. But i wanted to get input. How do enterprises or large providers deal with NAS/SAN security in terms of the host accessing the SAN/NAS share getting exploited?
tks
rough/quick idea of how i would physically segment, hypothetically (click to enlarge):

