danb35
Hall of Famer
- Joined
- Aug 16, 2011
- Messages
- 15,504
I'm looking into a scenario where I'd have a remote TrueNAS box connecting to my pfSense box via OpenVPN, so I could replicate to it from my main system. ZeroTier would have been perfect for this, but no, iX had to take that away (and never implemented it well to begin with). But no problem, TrueNAS now has an OpenVPN client, right?
Well... What I've done in the past is create the user (i.e., client) certificate in the pfSense web UI, then download the .ovpn file that contains all the relevant certs, keys, and other configuration settings. I can then import that into whatever client software I'm using, and configure the connection that way.
But I don't see a way to import such a file into TrueNAS. Instead, I see this:
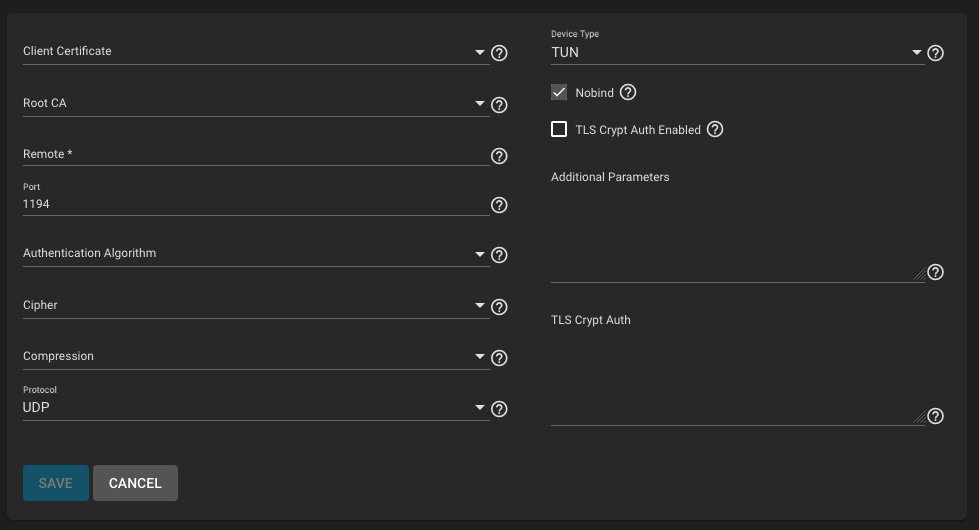
Lots of manual settings, lots of ways to get it wrong. Am I missing something here?
Well... What I've done in the past is create the user (i.e., client) certificate in the pfSense web UI, then download the .ovpn file that contains all the relevant certs, keys, and other configuration settings. I can then import that into whatever client software I'm using, and configure the connection that way.
But I don't see a way to import such a file into TrueNAS. Instead, I see this:
Lots of manual settings, lots of ways to get it wrong. Am I missing something here?
