nemesis1782
Contributor
- Joined
- Mar 2, 2021
- Messages
- 105
Hi all,
I've been struggling with getting networking to work properly with TrueNAS SCALE. My goal is to have multiple network interfaces in multiple VLANS for segregation. Just to be clear we're talking different subnets. There are no IPs shared by the same subnets, each VLAN has it's own /24 subnet.
The "issues" I've been running into and question I have, issue does not per see mean that there is something wrong with TrueNAS:
- Just one interface can be configured using DHCP.
- Which gateway takes preference, the DHCP or the standard gateway? When using DHCP it does not set the standard gateway.
- Each interface seems to use the same standard gateway.
- How do you configure a gateway for an interface?
- From what I've read the Kubernetes implementation used can use only one external subnet. Is this indeed true?
- It seems established traffic is being routed back through the interface that has DHCP set. Either my networking knowledge is a lot worse then I though or that's really bad.
The network I'm testing this on allows traffic between all the vlans with a allow all rule.
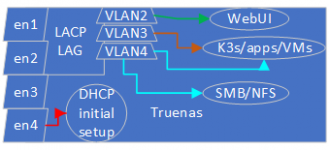
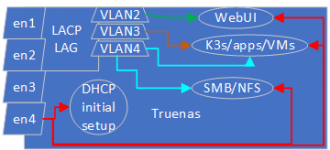
My envisioned setup would be as follows:
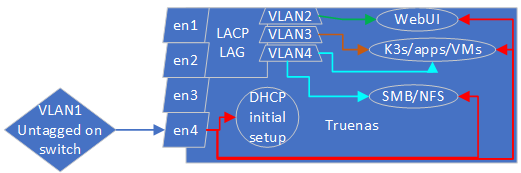
en1/2 are 10 Gb/s, en3/4 are 1 Gb/s
en4 would be disabled at the switch level unless there are issues with the other interfaces. Since there are many avenues for issues I decided to simplify.
VLAN1: 192.168.1.42/24
VLAN2: 192.168.2.42/24
VLAN3: 192.168.3.42/24
VLAN4: 192.168.4.42/24
VLAN5, client network accessible through the gateway of each VLAN: 192.168.5.42/24
I've simplified for testing:
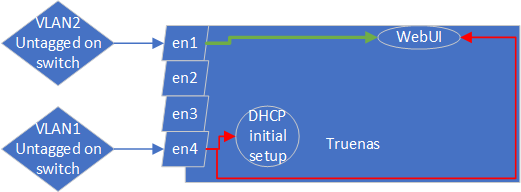
The WebUI is reachable on BOTH IPs from VLAN5 as long as both Interfaces en1, en4 are connected and active.
- 192.168.2.42 is not reachable if en1 is disconnected.
- The WebUI is not reachable from VLAN5 if en4 is disconnected
- The WebUI is reachable on 192.168.2.42 from a laptop connected to en1 with ip 192.168.2.41 and en4 is disconnected
- The WebUI is reachable on 192.168.2.42 from VLAN2 when en4 is disconnected
This leads me to believe that established traffic is routed back over the default gateway of vlan1 on en4. The weird thing is that en4 seems to keep it's ip configuration eventhough the nic en4 is down, I can see this when I login using the idrac virtual console.
I've tried setting the default gateway to 192.168.2.1 (default gateway for VLAN2), however that does make 192.168.2.42 available outside of VLAN2. It seems to ignore the defaut gateway.
The question is, was TrueNAS SCALE indeed designed to be segregated on a network. As it's fairly standard and TrueNAS is meant to be a enterprise level appliance I would assume so.
How would one go about defining multiple VLANS and routing the network traffic within TrueNAS properly?
I've been struggling with getting networking to work properly with TrueNAS SCALE. My goal is to have multiple network interfaces in multiple VLANS for segregation. Just to be clear we're talking different subnets. There are no IPs shared by the same subnets, each VLAN has it's own /24 subnet.
The "issues" I've been running into and question I have, issue does not per see mean that there is something wrong with TrueNAS:
- Just one interface can be configured using DHCP.
- Which gateway takes preference, the DHCP or the standard gateway? When using DHCP it does not set the standard gateway.
- Each interface seems to use the same standard gateway.
- How do you configure a gateway for an interface?
- From what I've read the Kubernetes implementation used can use only one external subnet. Is this indeed true?
- It seems established traffic is being routed back through the interface that has DHCP set. Either my networking knowledge is a lot worse then I though or that's really bad.
The network I'm testing this on allows traffic between all the vlans with a allow all rule.
My envisioned setup would be as follows:
en1/2 are 10 Gb/s, en3/4 are 1 Gb/s
en4 would be disabled at the switch level unless there are issues with the other interfaces. Since there are many avenues for issues I decided to simplify.
VLAN1: 192.168.1.42/24
VLAN2: 192.168.2.42/24
VLAN3: 192.168.3.42/24
VLAN4: 192.168.4.42/24
VLAN5, client network accessible through the gateway of each VLAN: 192.168.5.42/24
I've simplified for testing:
The WebUI is reachable on BOTH IPs from VLAN5 as long as both Interfaces en1, en4 are connected and active.
- 192.168.2.42 is not reachable if en1 is disconnected.
- The WebUI is not reachable from VLAN5 if en4 is disconnected
- The WebUI is reachable on 192.168.2.42 from a laptop connected to en1 with ip 192.168.2.41 and en4 is disconnected
- The WebUI is reachable on 192.168.2.42 from VLAN2 when en4 is disconnected
This leads me to believe that established traffic is routed back over the default gateway of vlan1 on en4. The weird thing is that en4 seems to keep it's ip configuration eventhough the nic en4 is down, I can see this when I login using the idrac virtual console.
I've tried setting the default gateway to 192.168.2.1 (default gateway for VLAN2), however that does make 192.168.2.42 available outside of VLAN2. It seems to ignore the defaut gateway.
The question is, was TrueNAS SCALE indeed designed to be segregated on a network. As it's fairly standard and TrueNAS is meant to be a enterprise level appliance I would assume so.
How would one go about defining multiple VLANS and routing the network traffic within TrueNAS properly?