Yatti420
Wizard
- Joined
- Aug 12, 2012
- Messages
- 1,437
Hi everybody,
I completed taking a look at DenyHosts and thought this would be useful for anybody running SSH over the internet especially with only password protection enabled.. If you take a look at on your FN box you will probably see quite a few hosts hammering your server throughout the day.. I wanted a way to automatically filter these hosts and potentially other bad hosts and went looking for a suitable application.. DenyHosts is perfect for giving SSH that little bit of extra edge while providing extra peace of mind.. The install is as follows.. This thread originated from my original discussion here and applies to FN 9.1.1..
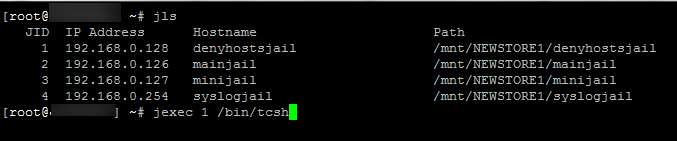
3. Using putty(recommended) or the WebGUI shell enter/access into the jail..
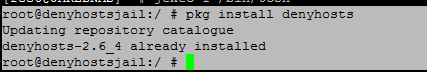
4. Review installing non-pbi software. Within the Jail - Install DenyHosts via Freshports with the pkg install command.
The following directories are applicable to DenyHosts within the jail..
CONFIG = /usr/local/etc/denyhosts.conf *
WORK_DIR = /usr/local/share/denyhosts/data *
PY SCRIPT =/usr/local/bin/denyhosts.py
RC Jail = /usr/local/etc/rc.d/denyhosts (start/stop/restart/status..)
Hosts.Evil = /etc/hosts.evil*
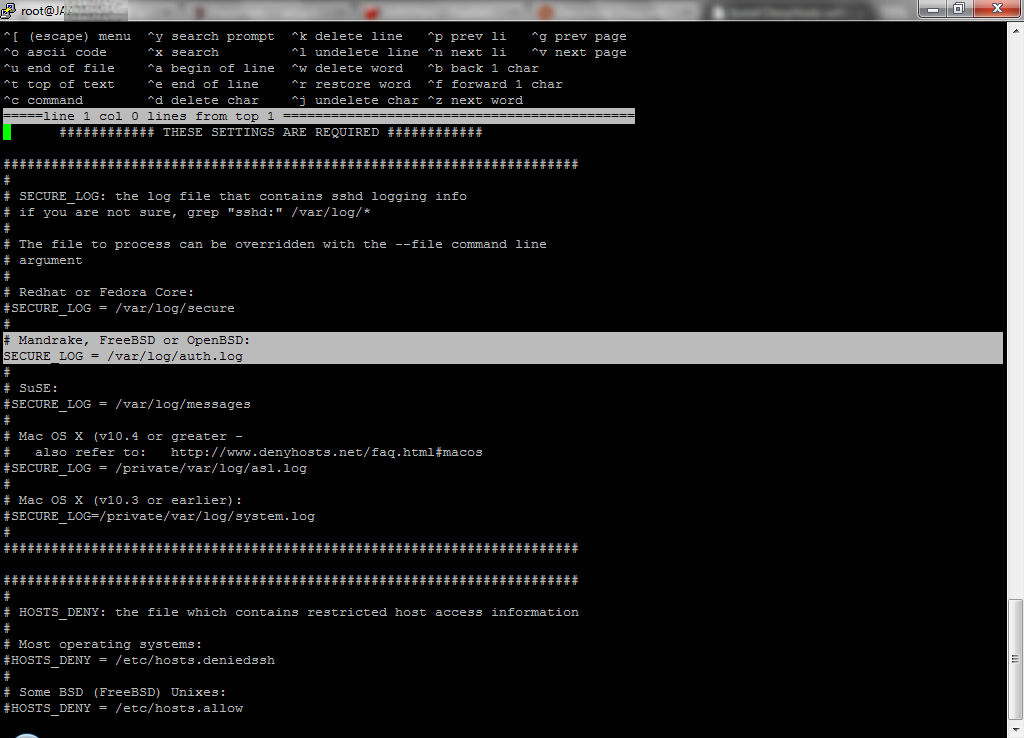
5.From within the newly crated jail - access the DenyHosts configuration and uncomment the appropriate lines for FreeBSD.. You may have to comment-out the linux specific lines..
SECURE LOG
HOSTS_DENY: the file which contains restricted host access information
HOSTS_DENY = /etc/hosts.evil
** output to new file (hosts.evil) instead of hosts.allow for freebsd and/or linux setup equivalent ..
BLOCK_SERVICE: the service name that should be blocked in HOSTS_DENY
# To block only sshd:
BLOCK_SERVICE = sshd
LOCK_FILE
# Debian (and FreeBSD)
LOCK_FILE = /var/run/denyhosts.pid
RESET_ON_SUCCESS: If this parameter is set to "yes" then the failed count for the respective ip address will be reset to 0 if the login is successful.
RESET_ON_SUCCESS = yes
I recommend leaving everything else as default currently..
6. Exit the jail using "exit" command. Within base freenas install edit /etc/hosts.allow with the following to instruct ssd to check the hosts.evil file before allowing all other connections.. Find the ALL : ALL : allow (Note full path) and place your deny instruction above.. See below..
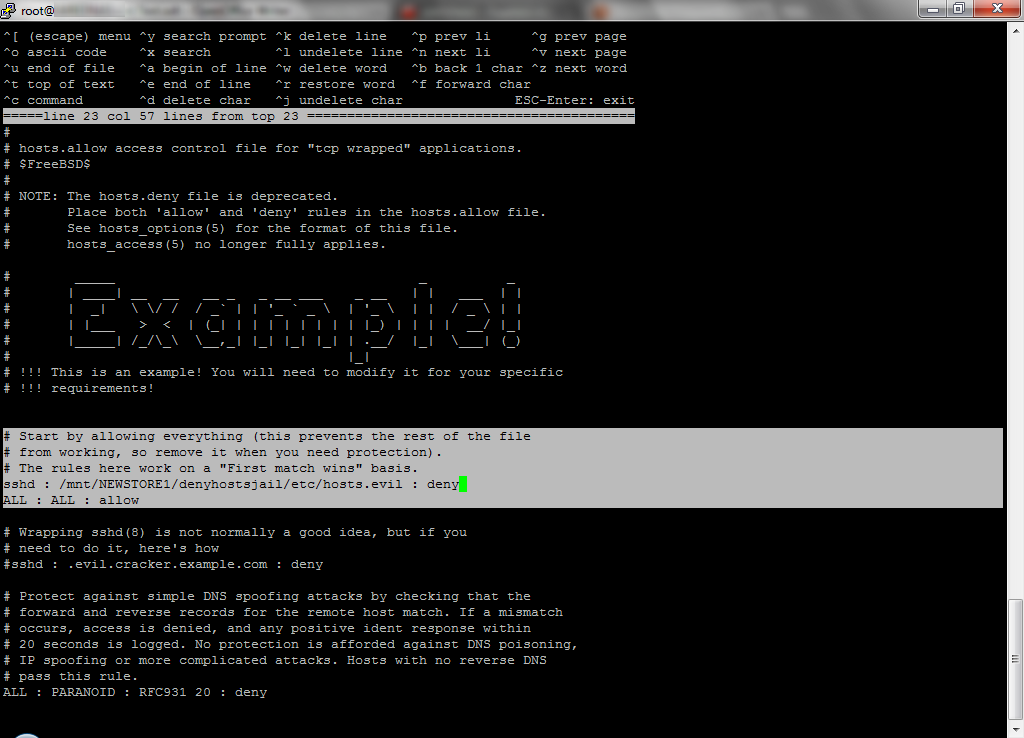
Save the new hosts.allow and restart SSH..
7. For a test.. Launch DenyHosts daemon manually within the jail created previously.
8. Verify operations by watching the following logs..
9. When satisfied everything is operational edit rc.conf setup to automatically launch daemon on start-up of jail..
10. Exit the jail and mount your freenas USB for config editing..
Repeat step #5 - edit /conf/base/etc/hosts.allow to make changes persistent across reboots.. Becareful what you do with USB mounted.. You can brick your system.. This will allow your instruction to check hosts.evil to be re-applied at startup..
11. Verify operations by watching the following logs..
11A. I recommend you add a allowed-hosts file to the work directory in order for your local addresses and domains to not be blocked/counted and eventually filtered if you have fat fingers etc.. From within the jail perform the following..
Uncomment the appropriate lines and edit as applicable.. Or append your entries to the bottom of the allowed-hosts file..
12. OPTIONAL: Enable synch mode (up/down) and/or purging for known bad hosts & added protection/flexibility..
Note:If you block an ip you didn't intend to via testing shutdown DenyHosts and ssh..First use the WebGUI (or any previously opened/connected putty window) to remove the entry from hosts.evil.. When completed restart ssh / DenyHosts.. You can now start putty then access the work directory and remove the entries from the following files.. If you don't do this when you login again you may be re-added to the hosts.evil as you exceeded thresholds in the past..
Edit: My security logs don't look they are being targeted brute forced anymore.. Works great :)
I completed taking a look at DenyHosts and thought this would be useful for anybody running SSH over the internet especially with only password protection enabled.. If you take a look at
Code:
cat /var/log/auth.log
- Create a jail applicable for non-pbi software from the WebGUI. An ip shouldn't be required for this setup (unless synch bad hosts required).. Ensure jail startup is automatic..
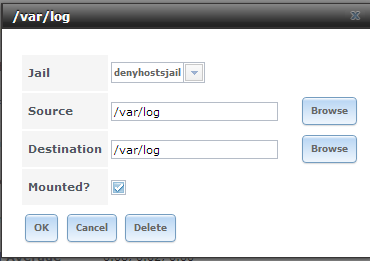
- Still within the GUI create a mount storage point for the jail .. /var/log/ (freenas usb) >>> /var/newlogmount (new denyhosts jail - see image below) ** See Corection Here..
3. Using putty(recommended) or the WebGUI shell enter/access into the jail..
4. Review installing non-pbi software. Within the Jail - Install DenyHosts via Freshports with the pkg install command.
Code:
pkg install denyhosts
The following directories are applicable to DenyHosts within the jail..
CONFIG = /usr/local/etc/denyhosts.conf *
WORK_DIR = /usr/local/share/denyhosts/data *
PY SCRIPT =/usr/local/bin/denyhosts.py
RC Jail = /usr/local/etc/rc.d/denyhosts (start/stop/restart/status..)
Hosts.Evil = /etc/hosts.evil*
5.From within the newly crated jail - access the DenyHosts configuration and uncomment the appropriate lines for FreeBSD.. You may have to comment-out the linux specific lines..
SECURE LOG
HOSTS_DENY: the file which contains restricted host access information
HOSTS_DENY = /etc/hosts.evil

** output to new file (hosts.evil) instead of hosts.allow for freebsd and/or linux setup equivalent ..
BLOCK_SERVICE: the service name that should be blocked in HOSTS_DENY
# To block only sshd:
BLOCK_SERVICE = sshd
LOCK_FILE
# Debian (and FreeBSD)
LOCK_FILE = /var/run/denyhosts.pid
RESET_ON_SUCCESS: If this parameter is set to "yes" then the failed count for the respective ip address will be reset to 0 if the login is successful.
RESET_ON_SUCCESS = yes
I recommend leaving everything else as default currently..
6. Exit the jail using "exit" command. Within base freenas install edit /etc/hosts.allow with the following to instruct ssd to check the hosts.evil file before allowing all other connections.. Find the ALL : ALL : allow (Note full path) and place your deny instruction above.. See below..
Code:
sshd : /mnt/NEWSTORE1/denyhostsjail/etc/hosts.evil : deny ALL : ALL : allow
Save the new hosts.allow and restart SSH..
7. For a test.. Launch DenyHosts daemon manually within the jail created previously.
Code:
/usr/local/etc/rc.d/denyhosts onestart
8. Verify operations by watching the following logs..
Code:
tail -f /var/log/auth.log tail -f /var/log/denyhosts
9. When satisfied everything is operational edit rc.conf setup to automatically launch daemon on start-up of jail..
Code:
denyhosts_enable="YES"
10. Exit the jail and mount your freenas USB for config editing..
Code:
mount -uw /
Repeat step #5 - edit /conf/base/etc/hosts.allow to make changes persistent across reboots.. Becareful what you do with USB mounted.. You can brick your system.. This will allow your instruction to check hosts.evil to be re-applied at startup..

11. Verify operations by watching the following logs..
Code:
tail -f /var/log/auth.log tail -f /var/log/denyhosts

11A. I recommend you add a allowed-hosts file to the work directory in order for your local addresses and domains to not be blocked/counted and eventually filtered if you have fat fingers etc.. From within the jail perform the following..
Code:
cd /usr/local/share/denyhosts/data touch allowed-hosts ee allowed-hosts
Uncomment the appropriate lines and edit as applicable.. Or append your entries to the bottom of the allowed-hosts file..
Code:
#Allowed Hosts Template # the following line prevents DenyHosts from blocking IP address 1.1.1.1 #1.1.1.1 # # The following lines prevent IP addresses 1.1.1.2 and 1.1.1.3 from being blocked #1.1.1.2 #1.1.1.3 # # The first 3 parts of the IP address must be provided (eg. 1.2.3.) # The last part of the IP address can be a wildcard. # The wildcard can be given with an asterisk -or- as a range. # # This line prevents all IP address in the 1.1.1 network from being blocked # 192.168.0.* # # This line prevents IP addresses in the range 1.1.1.6 to 1.1.1.23 from being blocked # 1.1.1.[6-23] # the following line prevents DenyHosts from blocking the host foo #foo #bar
12. OPTIONAL: Enable synch mode (up/down) and/or purging for known bad hosts & added protection/flexibility..
Note:If you block an ip you didn't intend to via testing shutdown DenyHosts and ssh..First use the WebGUI (or any previously opened/connected putty window) to remove the entry from hosts.evil.. When completed restart ssh / DenyHosts.. You can now start putty then access the work directory and remove the entries from the following files.. If you don't do this when you login again you may be re-added to the hosts.evil as you exceeded thresholds in the past..
Code:
-rw-r--r-- 1 root wheel 165 Oct 27 21:53 hosts -rw-r--r-- 1 root wheel 327 Oct 27 21:53 hosts-restricted -rw-r--r-- 1 root wheel 166 Oct 27 21:53 hosts-root -rw-r--r-- 1 root wheel 164 Oct 27 21:53 hosts-valid -rw-r--r-- 1 root wheel 0 Oct 27 21:53 suspicious-logins -rw-r--r-- 1 root wheel 146 Oct 27 21:53 users-hosts -rw-r--r-- 1 root wheel 1435 Oct 27 21:53 users-invalid -rw-r--r-- 1 root wheel 65 Oct 27 21:53 users-valid
Edit: My security logs don't look they are being targeted brute forced anymore.. Works great :)
Last edited:
