panzerscope
Contributor
- Joined
- May 30, 2022
- Messages
- 146
Hello all,
I have come across an issue where the "Owner Group" regarding my file permissions keeps getting changes to "Apps". I will change it to the group I need it to be, which is the same name as my user. So in this instance the User is "fadmin" and I will set the Owner Group to "fadmin" as well. However after a time, it will be reverted to the "apps" group.
I have also added "apps" as a user and group to my permission structure to see if it would stop this, but no luck. Does anyone have any ideas ? As an FYI the apps pool is not on the storage volume.
A below example of a folder and permission structure where "Apps" has become the Owner Group again is below.
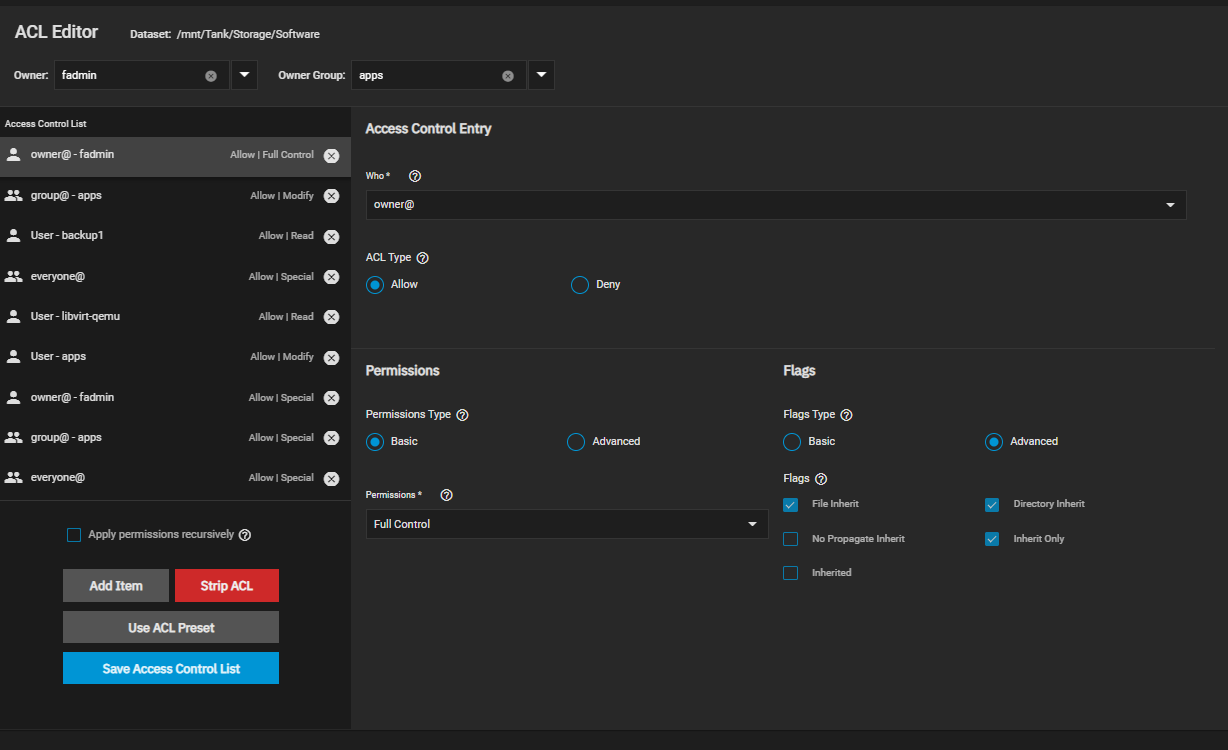
Many thanks,
p
I have come across an issue where the "Owner Group" regarding my file permissions keeps getting changes to "Apps". I will change it to the group I need it to be, which is the same name as my user. So in this instance the User is "fadmin" and I will set the Owner Group to "fadmin" as well. However after a time, it will be reverted to the "apps" group.
I have also added "apps" as a user and group to my permission structure to see if it would stop this, but no luck. Does anyone have any ideas ? As an FYI the apps pool is not on the storage volume.
A below example of a folder and permission structure where "Apps" has become the Owner Group again is below.
Many thanks,
p
