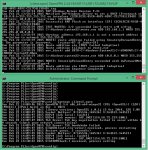
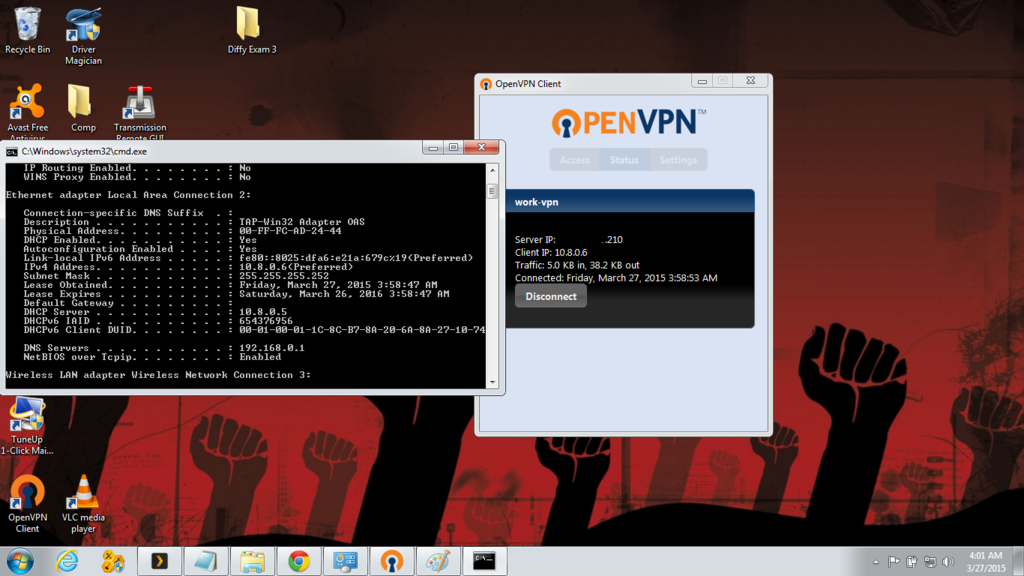
Wow, I FINALLLY got it working!! I kept everything as close to the tutorial as possible, even the john.appleseed part with the key names. I'm not sure exactly what it was but here are a few things that I did that might have made the difference.
- Dont spend too much time trying to fix your config, delete everything and start over. That includes the openvpn dataset you create as well. After you've been through the tutorial a few times, it doesnt take long at all to set up.
- Definitely add the below to your client config file. I think not routing all of your traffic through the VPN can potentially be confusing to your client on how to direct traffic.
- dhcp-option DNS 10.0.0.254
- redirect-gateway def1
- Instead of doing the 443 to 10011 port forward, I did 443 to 443. (Router issue?)
- Change to 10.0.8.0/24
- Just try and simplify as much as possible. Also, everytime you restart your jail, double check ifconfig to make sure your epair or tun #'s dont change on you. Mine did almost everytime. Make sure you're on the latest Freenas update. Reboot your server if it hasnt been restarted in a while.
Delete everything and start over, and if you're getting same results, post your config