Hello community,
I just bought a UPS (APC Back-UPS CS 350) which seems to work very fine to shutdown my FreeNAS server.
But: I want more ;)
I want to shutdown other critical devices in my network automatically too.
Unfortunately, the other devices are really heterogenous, so I couldn't use any standard mechanism like NUT.
What I did: I created a jail, installed python and started scripting.
The python scripts are now capable of shutting down several devices in my network, according to their needs (e.g. some via SSH, some via telnet...).
I added a shell script to my FreeNAS shell (I put it to /usr/local/bin/xxx.sh
The shell script consists of:
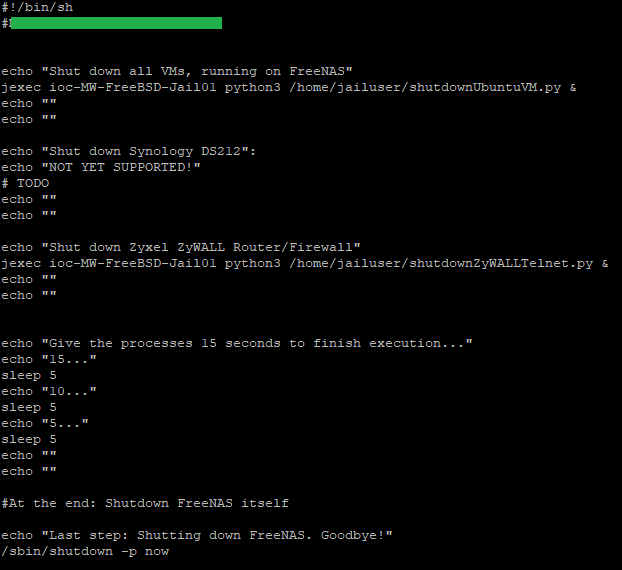
I set chmod 777 to the shell script, that all roles are able to execute the command.
When I execute the shell script as root, everything works fine.
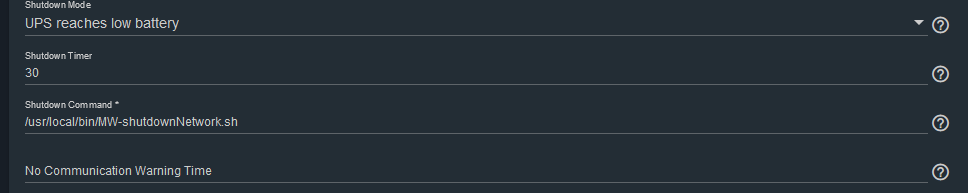
At the end, I replaced the "shutdown -h now" command in the UPS service with this:
Result: Only the FreeNAS server shutdown worked, all other commands aren't executed!
I did some research and I think I found the problem:
The UPS related processes (upsd is probably the one who does the actual call to the shutdown command?) all belong to the user "uucp"!
So I checked:
su -m uucp -c 'jexec ioc-MW-FreeBSD-Jail01 python3 /home/jailuser/shutdownUbuntuVM.py'
really results in jexec: jail_attach(1): Operation not permitted
This doesn't happen, when I execute that command as root.
I also tried chmod 777 for the command jexec. Still the same.
Problem is: I tried everything I could figure out by myself, but I can't get it running!
It seems that I can't put the user "uucp" to wheel, or at least, not effectively.
Is there a way to start the UPS processes as root and not with this uucp user?
pw group mod wheel -m uucp seems not to work
adding the uucp user in the FreeNAS web UI seems to be possible, but actually isn't! The change is not done...
I need some new ideas... please :)
I just bought a UPS (APC Back-UPS CS 350) which seems to work very fine to shutdown my FreeNAS server.
But: I want more ;)
I want to shutdown other critical devices in my network automatically too.
Unfortunately, the other devices are really heterogenous, so I couldn't use any standard mechanism like NUT.
What I did: I created a jail, installed python and started scripting.
The python scripts are now capable of shutting down several devices in my network, according to their needs (e.g. some via SSH, some via telnet...).
I added a shell script to my FreeNAS shell (I put it to /usr/local/bin/xxx.sh
The shell script consists of:
- several jexec calls, that execute python scripts in my jail
- the actual shutdown command for the FreeNAS
I set chmod 777 to the shell script, that all roles are able to execute the command.
When I execute the shell script as root, everything works fine.
At the end, I replaced the "shutdown -h now" command in the UPS service with this:
Result: Only the FreeNAS server shutdown worked, all other commands aren't executed!
I did some research and I think I found the problem:
The UPS related processes (upsd is probably the one who does the actual call to the shutdown command?) all belong to the user "uucp"!
So I checked:
su -m uucp -c 'jexec ioc-MW-FreeBSD-Jail01 python3 /home/jailuser/shutdownUbuntuVM.py'
really results in jexec: jail_attach(1): Operation not permitted
This doesn't happen, when I execute that command as root.
I also tried chmod 777 for the command jexec. Still the same.
Problem is: I tried everything I could figure out by myself, but I can't get it running!
It seems that I can't put the user "uucp" to wheel, or at least, not effectively.
Is there a way to start the UPS processes as root and not with this uucp user?
pw group mod wheel -m uucp seems not to work
adding the uucp user in the FreeNAS web UI seems to be possible, but actually isn't! The change is not done...
I need some new ideas... please :)
Last edited:
