rockybulwinkle
Dabbler
- Joined
- Aug 2, 2021
- Messages
- 25
Here is my setup:
I have a VPN server set up on an OpenWRT router on my home network, following these instructions: https://openwrt.org/docs/guide-user/services/vpn/openvpn/server
My home IP is dynamic, so I use an API my registrar provides (gandi) on my OpenWRT router to update a subdomain to keep pointing to my home address.
I have two TrueNAS servers, one is running Scale 22.02.0.1, the other Core 12.0-U8. Scale is my main server at home, Core is a replica off site. Core connects through OpenVPN to my router to have backups pushed to it.
This is almost working flawlessly, except my Core disconnects usually within 24 hours of coming up, and then I have to call someone to power cycle it.
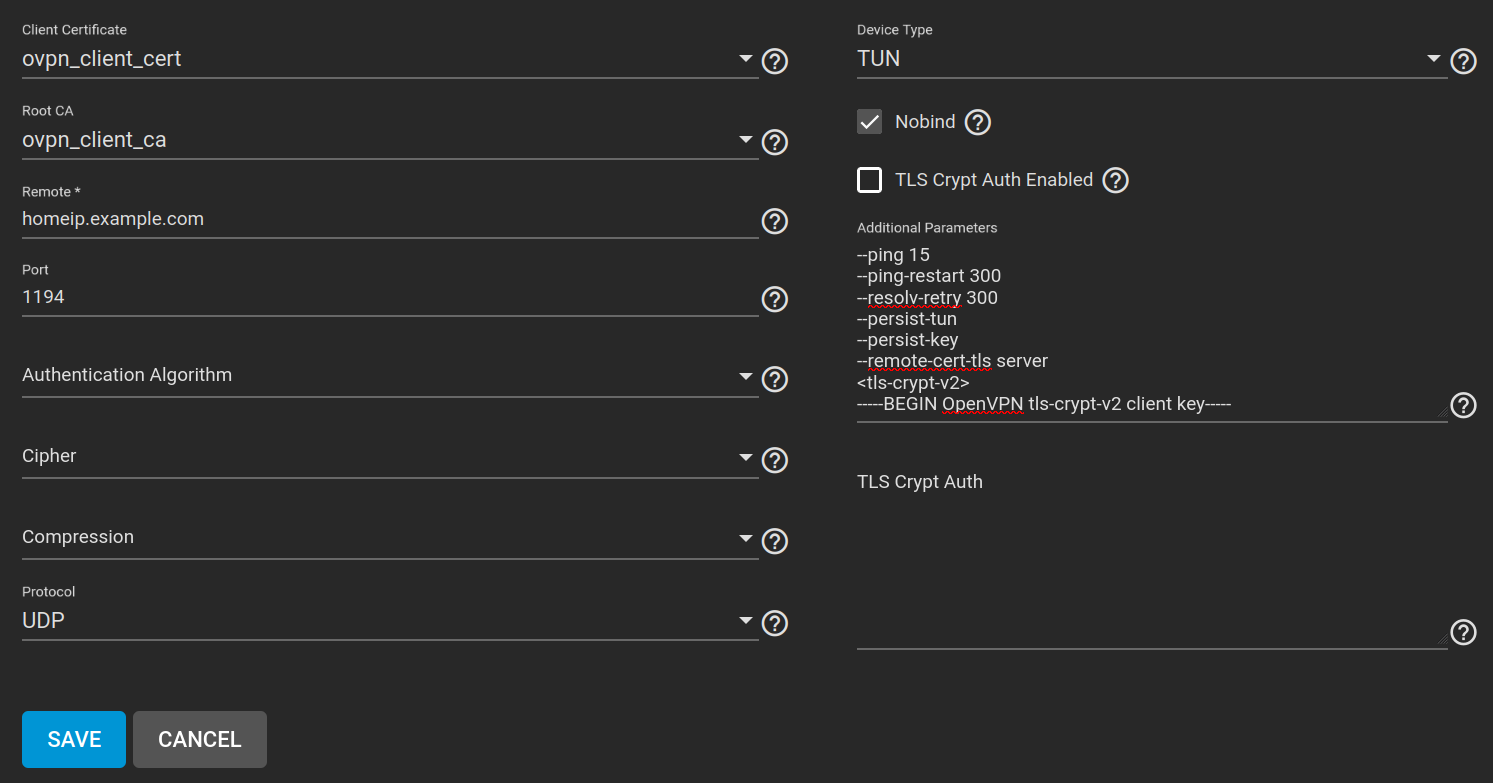
Here are the settings I have in my OpenVPN client config. Note that there are no further options beneath <tls-crypt-v2>, just the key.
I see the following in my messages, repeating over and over again. This is log is from *just* before Core was power cycled, while it was failing to connect to my network. I replaced my home IP with xxx.xxx.xxx.xxx. Are there other logs I should check? Note, atlas is the name of my Core server.
I'm hoping someone can provide some insight into why my client is losing connection. In the meantime, I'm going to try to narrow down the exact time that it loses connection by pinging 1 packet a second and recording the date and seeing when it stops responding, then cross reference with all the log files.
Thanks!
I have a VPN server set up on an OpenWRT router on my home network, following these instructions: https://openwrt.org/docs/guide-user/services/vpn/openvpn/server
My home IP is dynamic, so I use an API my registrar provides (gandi) on my OpenWRT router to update a subdomain to keep pointing to my home address.
I have two TrueNAS servers, one is running Scale 22.02.0.1, the other Core 12.0-U8. Scale is my main server at home, Core is a replica off site. Core connects through OpenVPN to my router to have backups pushed to it.
This is almost working flawlessly, except my Core disconnects usually within 24 hours of coming up, and then I have to call someone to power cycle it.
Here are the settings I have in my OpenVPN client config. Note that there are no further options beneath <tls-crypt-v2>, just the key.
I see the following in my messages, repeating over and over again. This is log is from *just* before Core was power cycled, while it was failing to connect to my network. I replaced my home IP with xxx.xxx.xxx.xxx. Are there other logs I should check? Note, atlas is the name of my Core server.
Code:
Jun 7 18:02:06 atlas 1 2022-06-07T18:02:06.597214-07:00 atlas.lan openvpn_client 1355 - - Restart pause, 300 second(s) Jun 7 18:07:06 atlas 1 2022-06-07T18:07:06.703711-07:00 atlas.lan openvpn_client 1355 - - Outgoing Control Channel Encryption: Cipher 'AES-256-CTR' initialized with 256 bit key Jun 7 18:07:06 atlas 1 2022-06-07T18:07:06.703751-07:00 atlas.lan openvpn_client 1355 - - Outgoing Control Channel Encryption: Using 256 bit message hash 'SHA256' for HMAC authentication Jun 7 18:07:06 atlas 1 2022-06-07T18:07:06.703758-07:00 atlas.lan openvpn_client 1355 - - Incoming Control Channel Encryption: Cipher 'AES-256-CTR' initialized with 256 bit key Jun 7 18:07:06 atlas 1 2022-06-07T18:07:06.703765-07:00 atlas.lan openvpn_client 1355 - - Incoming Control Channel Encryption: Using 256 bit message hash 'SHA256' for HMAC authentication Jun 7 18:07:17 atlas 1 2022-06-07T18:07:17.506162-07:00 atlas.lan openvpn_client 1355 - - TCP/UDP: Preserving recently used remote address: [AF_INET]xxx.xxx.xxx.xxx:1194 Jun 7 18:07:17 atlas 1 2022-06-07T18:07:17.506188-07:00 atlas.lan openvpn_client 1355 - - Socket Buffers: R=[42080->42080] S=[9216->9216] Jun 7 18:07:17 atlas 1 2022-06-07T18:07:17.506203-07:00 atlas.lan openvpn_client 1355 - - UDP link local: (not bound) Jun 7 18:07:17 atlas 1 2022-06-07T18:07:17.506209-07:00 atlas.lan openvpn_client 1355 - - UDP link remote: [AF_INET]xxx.xxx.xxx.xxx:1194 Jun 7 18:08:17 atlas 1 2022-06-07T18:08:17.768606-07:00 atlas.lan openvpn_client 1355 - - [UNDEF] Inactivity timeout (--ping-restart), restarting Jun 7 18:08:17 atlas 1 2022-06-07T18:08:17.768683-07:00 atlas.lan openvpn_client 1355 - - SIGUSR1[soft,ping-restart] received, process restarting Jun 7 18:08:17 atlas 1 2022-06-07T18:08:17.768703-07:00 atlas.lan openvpn_client 1355 - - Restart pause, 300 second(s) Jun 7 18:13:17 atlas 1 2022-06-07T18:13:17.825727-07:00 atlas.lan openvpn_client 1355 - - Outgoing Control Channel Encryption: Cipher 'AES-256-CTR' initialized with 256 bit key Jun 7 18:13:17 atlas 1 2022-06-07T18:13:17.825777-07:00 atlas.lan openvpn_client 1355 - - Outgoing Control Channel Encryption: Using 256 bit message hash 'SHA256' for HMAC authentication Jun 7 18:13:17 atlas 1 2022-06-07T18:13:17.825784-07:00 atlas.lan openvpn_client 1355 - - Incoming Control Channel Encryption: Cipher 'AES-256-CTR' initialized with 256 bit key Jun 7 18:13:17 atlas 1 2022-06-07T18:13:17.825791-07:00 atlas.lan openvpn_client 1355 - - Incoming Control Channel Encryption: Using 256 bit message hash 'SHA256' for HMAC authentication Jun 7 18:13:28 atlas 1 2022-06-07T18:13:28.628430-07:00 atlas.lan openvpn_client 1355 - - TCP/UDP: Preserving recently used remote address: [AF_INET]xxx.xxx.xxx.xxx:1194 Jun 7 18:13:28 atlas 1 2022-06-07T18:13:28.628454-07:00 atlas.lan openvpn_client 1355 - - Socket Buffers: R=[42080->42080] S=[9216->9216] Jun 7 18:13:28 atlas 1 2022-06-07T18:13:28.628469-07:00 atlas.lan openvpn_client 1355 - - UDP link local: (not bound) Jun 7 18:13:28 atlas 1 2022-06-07T18:13:28.628475-07:00 atlas.lan openvpn_client 1355 - - UDP link remote: [AF_INET]xxx.xxx.xxx.xxx:1194 Jun 7 18:14:28 atlas 1 2022-06-07T18:14:28.334816-07:00 atlas.lan openvpn_client 1355 - - [UNDEF] Inactivity timeout (--ping-restart), restarting Jun 7 18:14:28 atlas 1 2022-06-07T18:14:28.334912-07:00 atlas.lan openvpn_client 1355 - - SIGUSR1[soft,ping-restart] received, process restarting Jun 7 18:14:28 atlas 1 2022-06-07T18:14:28.334934-07:00 atlas.lan openvpn_client 1355 - - Restart pause, 300 second(s)
I'm hoping someone can provide some insight into why my client is losing connection. In the meantime, I'm going to try to narrow down the exact time that it loses connection by pinging 1 packet a second and recording the date and seeing when it stops responding, then cross reference with all the log files.
Thanks!
