MrGuvernment
Patron
- Joined
- Jun 15, 2017
- Messages
- 268
First they stored stuff in plain text in 2014, and now this..
For those who do not know. you should NEVER EVER EVER expose any out of band interface direct to the internet, ever, If you are, please turn in your IT / Home Lab / Geek card and exit that way....(but first remove said devices from Inet access)

 thehackernews.com
thehackernews.com
For those who do not know. you should NEVER EVER EVER expose any out of band interface direct to the internet, ever, If you are, please turn in your IT / Home Lab / Geek card and exit that way....(but first remove said devices from Inet access)

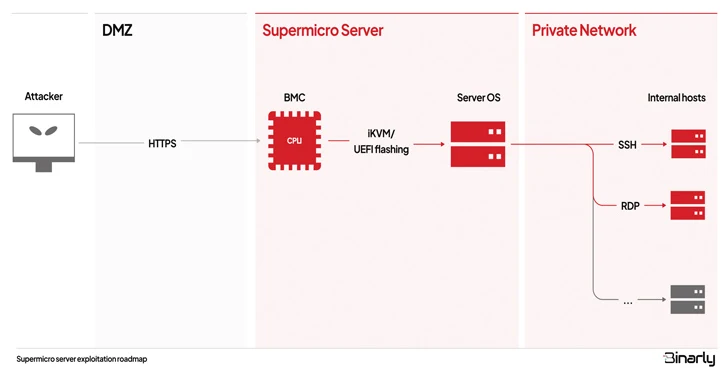
Supermicro's BMC Firmware Found Vulnerable to Multiple Critical Vulnerabilities
Multiple security flaws in Supermicro's BMC firmware pose severe risks. Know the risks from CVE-2023-40284 to CVE-2023-40290.
 thehackernews.com
thehackernews.com

A brief explainer of each of the vulnerabilities is below -
CVE-2023-40284, CVE-2023-40287, and CVE-2023-40288 (CVSS scores: 9.6) - Three cross-site scripting (XSS) flaws that allow remote, unauthenticated attackers to execute arbitrary JavaScript code in the context of the logged-in BMC user.
CVE-2023-40285 and CVE-2023-40286 (CVSS score: 8.6) - Two cross-site scripting (XSS) flaws that allow remote, unauthenticated attackers to execute arbitrary JavaScript code in the context of the logged-in BMC user by poisoning browser cookies or local storage.
CVE-2023-40289 (CVSS score: 9.1) - An operating system command injection flaw that allows for the execution of malicious code as a user with administrative privileges.
CVE-2023-40290 (CVSS score: 8.3) - A cross-site scripting (XSS) flaw that allows remote, unauthenticated attackers to execute arbitrary JavaScript code in the context of the logged-in BMC user, but only when using Internet Explorer 11 browser on Windows.
CVE-2023-40289 is "critical because it allows authenticated attackers to gain root access and completely compromise the BMC system," Binarly said in a technical analysis published this week
