Upgraded to 21.08 and trying to learn my way around.
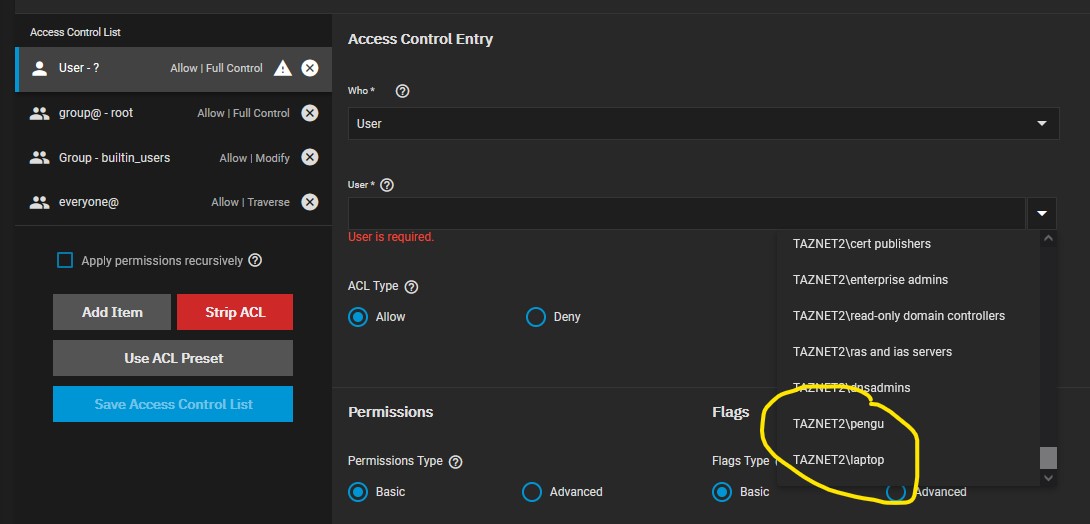
If I create an SMB share and try to give a specific domain user permissions, not all domain users are listed:
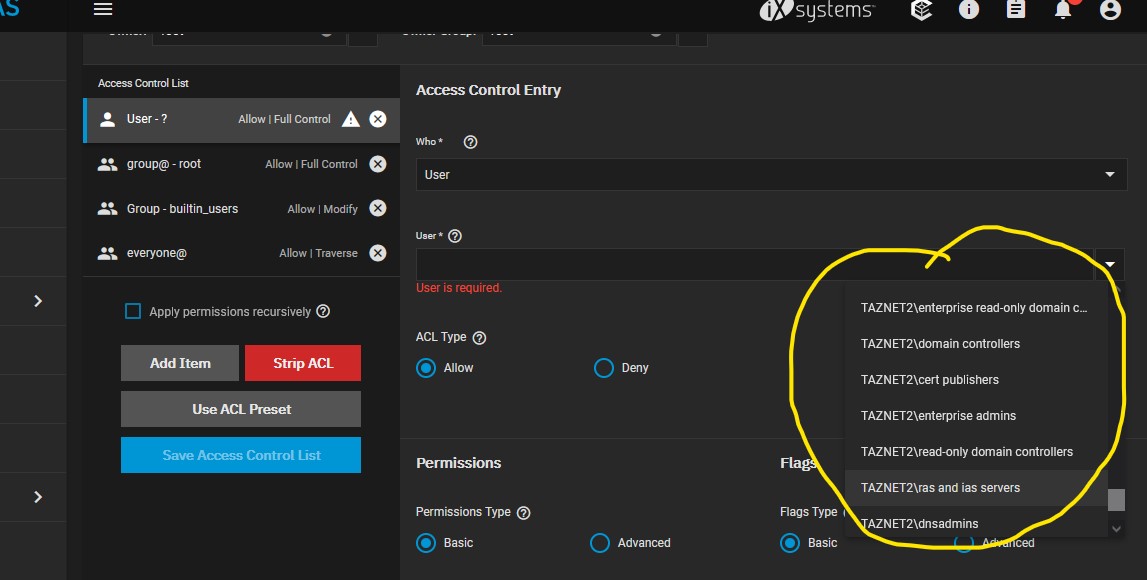
Same with a group:
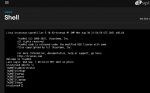
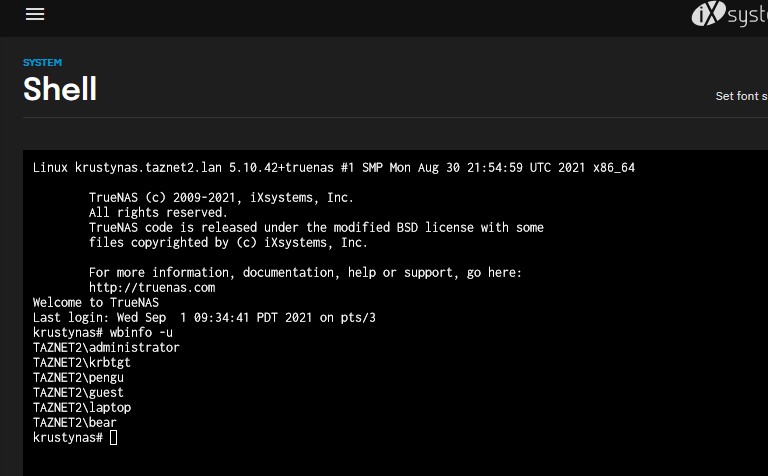
Issuing the command wbinfo -u shows all the domain users:
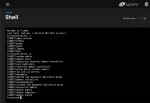
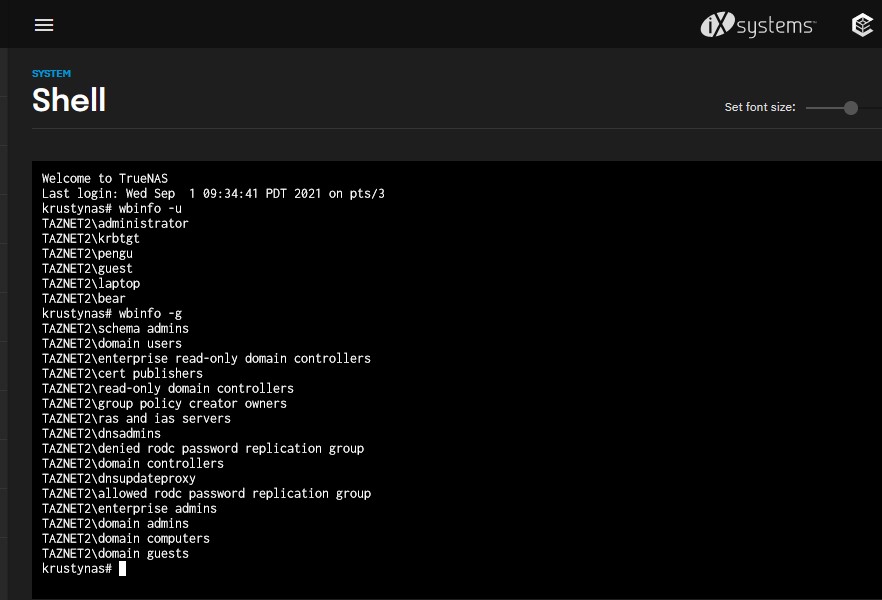
Same with wbinfo -g
Shares created before the update to 21.08 still work, but I can't give permissions to say the domain admins group. It is not specifically listed.
I don't know what to make of this. Thoughts?
If I create an SMB share and try to give a specific domain user permissions, not all domain users are listed:
Same with a group:
Issuing the command wbinfo -u shows all the domain users:
Same with wbinfo -g
Shares created before the update to 21.08 still work, but I can't give permissions to say the domain admins group. It is not specifically listed.
I don't know what to make of this. Thoughts?