[2021/01/02 15:25:04.267793, 10, pid=4153, effective(1000, 1000), real(0, 0), class=smb2] ../../source3/smbd/smb2_server.c:3980(smbd_smb2_io_handler)
smbd_smb2_request idx[1] of 5 vectors
[2021/01/02 15:25:04.267841, 10, pid=4153, effective(1000, 1000), real(0, 0), class=smb2_credits] ../../source3/smbd/smb2_server.c:691(smb2_validate_sequence_number)
smb2_validate_sequence_number: smb2_validate_sequence_number: clearing id 17 (position 17) from bitmap
[2021/01/02 15:25:04.267858, 10, pid=4153, effective(1000, 1000), real(0, 0), class=smb2] ../../source3/smbd/smb2_server.c:2343(smbd_smb2_request_dispatch)
smbd_smb2_request_dispatch: opcode[SMB2_OP_CREATE] mid = 17
[2021/01/02 15:25:04.267875, 5, pid=4153, effective(1000, 1000), real(0, 0)] ../../source3/smbd/uid.c:326(change_to_user_impersonate)
change_to_user_impersonate: Skipping user change - already user
[2021/01/02 15:25:04.267948, 4, pid=4153, effective(1000, 1000), real(0, 0), class=vfs] ../../source3/smbd/vfs.c:805(vfs_ChDir)
vfs_ChDir to /mnt/RaidZ01/Windows/DataFilms
[2021/01/02 15:25:04.267991, 3, pid=4153, effective(1000, 1000), real(0, 0)] ../../source3/smbd/service.c:157(chdir_current_service)
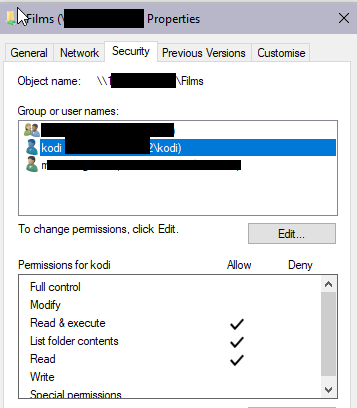
chdir (/mnt/RaidZ01/Windows/DataFilms) failed, reason: Permission denied
[2021/01/02 15:25:04.268026, 0, pid=4153, effective(1000, 1000), real(0, 0)] ../../source3/smbd/uid.c:448(change_to_user_internal)
change_to_user_internal: chdir_current_service() failed!
[2021/01/02 15:25:04.268040, 3, pid=4153, effective(1000, 1000), real(0, 0), class=smb2] ../../source3/smbd/smb2_server.c:3213(smbd_smb2_request_error_ex)
smbd_smb2_request_error_ex: smbd_smb2_request_error_ex: idx[1] status[NT_STATUS_ACCESS_DENIED] || at ../../source3/smbd/smb2_server.c:2542
[2021/01/02 15:25:04.268091, 10, pid=4153, effective(1000, 1000), real(0, 0), class=smb2] ../../source3/smbd/smb2_server.c:3104(smbd_smb2_request_done_ex)
smbd_smb2_request_done_ex: idx[1] status[NT_STATUS_ACCESS_DENIED] body[8] dyn[yes:1] at ../../source3/smbd/smb2_server.c:3261
[2021/01/02 15:25:04.268126, 10, pid=4153, effective(1000, 1000), real(0, 0), class=smb2_credits] ../../source3/smbd/smb2_server.c:956(smb2_set_operation_credit)
smb2_set_operation_credit: smb2_set_operation_credit: requested 1, charge 1, granted 1, current possible/max 8160/8192, total granted/max/low/range 33/8192/18/33
[2021/01/02 15:25:04.270397, 10, pid=4153, effective(1000, 1000), real(0, 0), class=smb2] ../../source3/smbd/smb2_server.c:3980(smbd_smb2_io_handler)
smbd_smb2_request idx[1] of 5 vectors
[2021/01/02 15:25:04.270432, 10, pid=4153, effective(1000, 1000), real(0, 0), class=smb2_credits] ../../source3/smbd/smb2_server.c:691(smb2_validate_sequence_number)
smb2_validate_sequence_number: smb2_validate_sequence_number: clearing id 18 (position 18) from bitmap
[2021/01/02 15:25:04.270449, 10, pid=4153, effective(1000, 1000), real(0, 0), class=smb2] ../../source3/smbd/smb2_server.c:2343(smbd_smb2_request_dispatch)
smbd_smb2_request_dispatch: opcode[SMB2_OP_IOCTL] mid = 18
[2021/01/02 15:25:04.270483, 4, pid=4153, effective(1000, 1000), real(0, 0)] ../../source3/smbd/sec_ctx.c:320(set_sec_ctx_internal)
setting sec ctx (1000, 1000) - sec_ctx_stack_ndx = 0
[2021/01/02 15:25:04.270502, 5, pid=4153, effective(1000, 1000), real(0, 0)] ../../libcli/security/security_token.c:63(security_token_debug)
Security token SIDs (11):
SID[ 0]: S-1-5-21-1909120653-2637104421-1922714665-1005
SID[ 1]: S-1-5-21-1909120653-2637104421-1922714665-513
SID[ 2]: S-1-5-21-1909120653-2637104421-1922714665-1001
SID[ 3]: S-1-1-0
SID[ 4]: S-1-5-2
SID[ 5]: S-1-5-11
SID[ 6]: S-1-22-1-1000
SID[ 7]: S-1-22-2-1000
SID[ 8]: S-1-22-2-90000001
SID[ 9]: S-1-22-2-90000002
SID[ 10]: S-1-22-2-90000003
Privileges (0x E00):
Privilege[ 0]: SeTakeOwnershipPrivilege
Privilege[ 1]: SeBackupPrivilege
Privilege[ 2]: SeRestorePrivilege
Rights (0x 0):
[2021/01/02 15:25:04.270670, 5, pid=4153, effective(1000, 1000), real(0, 0)] ../../source3/auth/token_util.c:866(debug_unix_user_token)
UNIX token of user 1000
Primary group is 1000 and contains 4 supplementary groups
Group[ 0]: 1000
Group[ 1]: 90000001
Group[ 2]: 90000002
Group[ 3]: 90000003
[2021/01/02 15:25:04.270796, 5, pid=4153, effective(1000, 1000), real(0, 0)] ../../source3/smbd/uid.c:300(print_impersonation_info)
print_impersonation_info: Impersonated user: uid=(0,1000), gid=(0,1000), cwd=[/var/tmp]
[2021/01/02 15:25:04.270824, 10, pid=4153, effective(1000, 1000), real(0, 0), class=smb2_credits] ../../source3/smbd/smb2_server.c:2013(smbd_smb2_request_verify_creditcharge)
smbd_smb2_request_verify_creditcharge: mid 18, CreditCharge: 1, NeededCharge: 1
[2021/01/02 15:25:04.270850, 10, pid=4153, effective(1000, 1000), real(0, 0), class=smb2] ../../source3/smbd/smb2_ioctl.c:397(smbd_smb2_ioctl_send)
smbd_smb2_ioctl: ctl_code[0x00110018] <no handle>, fnum [fsp is NULL]
[2021/01/02 15:25:04.270883, 10, pid=4153, effective(1000, 1000), real(0, 0), class=smb2] ../../source3/smbd/smb2_ioctl.c:294(smbd_smb2_request_ioctl_done)
smbd_smb2_request_ioctl_done: smbd_smb2_ioctl_recv returned 0 status NT_STATUS_FS_DRIVER_REQUIRED
[2021/01/02 15:25:04.270901, 3, pid=4153, effective(1000, 1000), real(0, 0), class=smb2] ../../source3/smbd/smb2_server.c:3213(smbd_smb2_request_error_ex)
smbd_smb2_request_error_ex: smbd_smb2_request_error_ex: idx[1] status[NT_STATUS_FS_DRIVER_REQUIRED] || at ../../source3/smbd/smb2_ioctl.c:312
[2021/01/02 15:25:04.270918, 10, pid=4153, effective(1000, 1000), real(0, 0), class=smb2] ../../source3/smbd/smb2_server.c:3104(smbd_smb2_request_done_ex)
smbd_smb2_request_done_ex: idx[1] status[NT_STATUS_FS_DRIVER_REQUIRED] body[8] dyn[yes:1] at ../../source3/smbd/smb2_server.c:3261
[2021/01/02 15:25:04.270938, 10, pid=4153, effective(1000, 1000), real(0, 0), class=smb2_credits] ../../source3/smbd/smb2_server.c:956(smb2_set_operation_credit)
smb2_set_operation_credit: smb2_set_operation_credit: requested 1, charge 1, granted 1, current possible/max 8160/8192, total granted/max/low/range 33/8192/19/33
[2021/01/02 15:25:04.292911, 10, pid=4153, effective(1000, 1000), real(0, 0), class=smb2] ../../source3/smbd/smb2_server.c:3980(smbd_smb2_io_handler)
smbd_smb2_request idx[1] of 5 vectors
[2021/01/02 15:25:04.292949, 10, pid=4153, effective(1000, 1000), real(0, 0), class=smb2_credits] ../../source3/smbd/smb2_server.c:691(smb2_validate_sequence_number)
smb2_validate_sequence_number: smb2_validate_sequence_number: clearing id 19 (position 19) from bitmap
[2021/01/02 15:25:04.292971, 10, pid=4153, effective(1000, 1000), real(0, 0), class=smb2] ../../source3/smbd/smb2_server.c:2343(smbd_smb2_request_dispatch)
smbd_smb2_request_dispatch: opcode[SMB2_OP_CREATE] mid = 19
[2021/01/02 15:25:04.293005, 4, pid=4153, effective(1000, 1000), real(0, 0)] ../../source3/smbd/sec_ctx.c:320(set_sec_ctx_internal)
setting sec ctx (1000, 1000) - sec_ctx_stack_ndx = 0
[2021/01/02 15:25:04.293047, 5, pid=4153, effective(1000, 1000), real(0, 0)] ../../libcli/security/security_token.c:63(security_token_debug)
Security token SIDs (11):
SID[ 0]: S-1-5-21-1909120653-2637104421-1922714665-1005
SID[ 1]: S-1-5-21-1909120653-2637104421-1922714665-513
SID[ 2]: S-1-5-21-1909120653-2637104421-1922714665-1001
SID[ 3]: S-1-1-0
SID[ 4]: S-1-5-2
SID[ 5]: S-1-5-11
SID[ 6]: S-1-22-1-1000
SID[ 7]: S-1-22-2-1000
SID[ 8]: S-1-22-2-90000001
SID[ 9]: S-1-22-2-90000002
SID[ 10]: S-1-22-2-90000003
Privileges (0x E00):
Privilege[ 0]: SeTakeOwnershipPrivilege
Privilege[ 1]: SeBackupPrivilege
Privilege[ 2]: SeRestorePrivilege
Rights (0x 0):
[2021/01/02 15:25:04.293543, 5, pid=4153, effective(1000, 1000), real(0, 0)] ../../source3/auth/token_util.c:866(debug_unix_user_token)
UNIX token of user 1000
Primary group is 1000 and contains 4 supplementary groups
Group[ 0]: 1000
Group[ 1]: 90000001
Group[ 2]: 90000002
Group[ 3]: 90000003
[2021/01/02 15:25:04.293635, 4, pid=4153, effective(1000, 1000), real(0, 0), class=vfs] ../../source3/smbd/vfs.c:805(vfs_ChDir)
vfs_ChDir to /mnt/RaidZ01/Windows/DataFilms
[2021/01/02 15:25:04.293665, 3, pid=4153, effective(1000, 1000), real(0, 0)] ../../source3/smbd/service.c:157(chdir_current_service)
chdir (/mnt/RaidZ01/Windows/DataFilms) failed, reason: Permission denied
[2021/01/02 15:25:04.293689, 0, pid=4153, effective(1000, 1000), real(0, 0)] ../../source3/smbd/uid.c:448(change_to_user_internal)
change_to_user_internal: chdir_current_service() failed!
[2021/01/02 15:25:04.293715, 3, pid=4153, effective(1000, 1000), real(0, 0), class=smb2] ../../source3/smbd/smb2_server.c:3213(smbd_smb2_request_error_ex)
smbd_smb2_request_error_ex: smbd_smb2_request_error_ex: idx[1] status[NT_STATUS_ACCESS_DENIED] || at ../../source3/smbd/smb2_server.c:2542
[2021/01/02 15:25:04.293744, 10, pid=4153, effective(1000, 1000), real(0, 0), class=smb2] ../../source3/smbd/smb2_server.c:3104(smbd_smb2_request_done_ex)
smbd_smb2_request_done_ex: idx[1] status[NT_STATUS_ACCESS_DENIED] body[8] dyn[yes:1] at ../../source3/smbd/smb2_server.c:3261
[2021/01/02 15:25:04.293764, 10, pid=4153, effective(1000, 1000), real(0, 0), class=smb2_credits] ../../source3/smbd/smb2_server.c:956(smb2_set_operation_credit)
smb2_set_operation_credit: smb2_set_operation_credit: requested 13, charge 1, granted 13, current possible/max 8160/8192, total granted/max/low/range 45/8192/20/45
[2021/01/02 15:25:07.140550, 10, pid=4153, effective(1000, 1000), real(0, 0)] ../../source3/lib/util_event.c:43(smbd_idle_event_handler)
smbd_idle_event_handler: idle_evt(deadtime) 0x0 called
[2021/01/02 15:25:07.140609, 10, pid=4153, effective(1000, 1000), real(0, 0)] ../../source3/lib/util_event.c:54(smbd_idle_event_handler)
smbd_idle_event_handler: idle_evt(deadtime) 0x0 rescheduled
[2021/01/02 15:25:07.140660, 10, pid=4153, effective(1000, 1000), real(0, 0)] ../../source3/lib/util_event.c:43(smbd_idle_event_handler)
smbd_idle_event_handler: idle_evt(housekeeping) 0x0 called
[2021/01/02 15:25:07.140738, 5, pid=4153, effective(1000, 1000), real(0, 0)] ../../source3/smbd/process.c:2897(housekeeping_fn)
housekeeping
[2021/01/02 15:25:07.140916, 4, pid=4153, effective(1000, 1000), real(0, 0)] ../../source3/smbd/sec_ctx.c:320(set_sec_ctx_internal)
setting sec ctx (0, 0) - sec_ctx_stack_ndx = 0
[2021/01/02 15:25:07.141161, 5, pid=4153, effective(1000, 1000), real(0, 0)] ../../libcli/security/security_token.c:53(security_token_debug)
Security token: (NULL)
[2021/01/02 15:25:07.141285, 5, pid=4153, effective(1000, 1000), real(0, 0)] ../../source3/auth/token_util.c:866(debug_unix_user_token)
UNIX token of user 0
Primary group is 0 and contains 0 supplementary groups
[2021/01/02 15:25:07.141354, 5, pid=4153, effective(0, 0), real(0, 0)] ../../source3/smbd/uid.c:504(smbd_change_to_root_user)
change_to_root_user: now uid=(0,0) gid=(0,0)
[2021/01/02 15:25:07.141376, 10, pid=4153, effective(0, 0), real(0, 0)] ../../source3/lib/util_event.c:54(smbd_idle_event_handler)
smbd_idle_event_handler: idle_evt(housekeeping) 0x0 rescheduled