AndrewShumate
Cadet
- Joined
- Feb 11, 2022
- Messages
- 4
So in the past few days I have been playing around with Tailscale for the one day when I finally get back on the road for work and I want to access things at home like my files or my Plex instance when I finally get around to uploading media to my NAS. I looked around and fond that the maintainers of the FreeBSD Tailscale package finally got it working in a jail and with a little bit of sleuthing I have figured out how to not only get Tailscale working in a normal jail, but also in a plugin jail.
So hold on to your hats.
Step 1: Cut a hole in the box... Oh wait! wrong tutorial...
Most importantly when you create your jail or plugin select advanced options fill in all of the relevant Information like name whether you want it NAT'd or not etc, then go to the
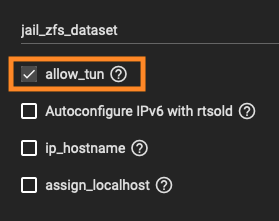
Then create your jail/plugin
Step 2: [When 1.20 makes it to Quarterly this step will become irrelevant]
Then go to your Jail's shell and edit the file
You want to change the line
Then to make sure you're using the correct repository run pkg search tailscale and verify that it's tailscale-1.20.3
Step 3:
run
Step 4:
run
Step 5:
run
Step 6:
make sure tailscaled is running
Optional Step 7:
Go to tailscale.com and create an Auth key, you can create a single key that will allow you to auth all of your jails/plugins or you can create one per jail/plugin
Step 8:
run
Optional Step 9:
go to your list of machines on Tailscale.com and disable key expiry for your jails and plugins
FIN
So far I have successfully installed Tailscale in one standalone jail and advertised my home network as a subnet and installed it in three plugins and successfully connected to them from outside my home LAN
So hold on to your hats.
Step 1: Cut a hole in the box... Oh wait! wrong tutorial...
Most importantly when you create your jail or plugin select advanced options fill in all of the relevant Information like name whether you want it NAT'd or not etc, then go to the
Custom Properties section and check allow_tunThen create your jail/plugin
Step 2: [When 1.20 makes it to Quarterly this step will become irrelevant]
Then go to your Jail's shell and edit the file
/etc/pkg/FreeBSD.confYou want to change the line
url: "pkg+http://pkg.FreeBSD.org/${ABI}/quarterly", so that it says url: "pkg+http://pkg.FreeBSD.org/${ABI}/latest",Then to make sure you're using the correct repository run pkg search tailscale and verify that it's tailscale-1.20.3
Step 3:
run
pkg install tailscale and enter yStep 4:
run
service tailscaled enableStep 5:
run
service tailscaled startStep 6:
make sure tailscaled is running
service tailscaled statusOptional Step 7:
Go to tailscale.com and create an Auth key, you can create a single key that will allow you to auth all of your jails/plugins or you can create one per jail/plugin
Step 8:
run
tailscale up click on the link it gives you and sign in, or if you create an authkey run tailscale up --authkey <your auth key here>Optional Step 9:
go to your list of machines on Tailscale.com and disable key expiry for your jails and plugins
FIN
So far I have successfully installed Tailscale in one standalone jail and advertised my home network as a subnet and installed it in three plugins and successfully connected to them from outside my home LAN
