I delete everything and did the procedure again with standard instead pluginjail and the result are the same.
I think that my problem is because the port is not opening, but router is configure ok.
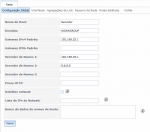
Need to configure some special at FreeNAS to port forwarding this?
I check VIMAGE box after pkg update, upgrade, install...
With this check box I did not get internet.
And if I leave this unmarked openvpn does not start.
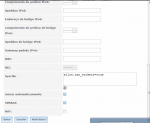
Here my files:
nano openvpn.conf
Code:
port 10011
proto udp
dev tun
ca ca.crt
cert openvpn-server.crt #Server public key
key openvpn-server.key #Server private key
dh dh.pem #Diffie-Hellman parameters
server 172.16.8.0 255.255.255.0 #Purple network
ifconfig-pool-persist ipp.txt
push "route 192.168.25.0 255.255.255.0" #Yellow network
tls-auth ta.key 0
#crl-verify crl.pem
keepalive 10 120
cipher AES-256-CBC
group nobody
user nobody
comp-lzo
persist-key
persist-tun
Code:
#!/bin/sh
EPAIR=$(/sbin/ifconfig -l | tr " " "\n" | /usr/bin/grep epair)
ipfw -q -f flush
ipfw -q nat 1 config if ${EPAIR}
ipfw -q add nat 1 all from 172.16.8.0/24 to any out via ${EPAIR}
ipfw -q add nat 1 all from any to any in via ${EPAIR}
TUN=$(/sbin/ifconfig -l | tr " " "\n" | /usr/bin/grep tun)
ifconfig ${TUN} name tun0
nano /etc/rc.conf
Code:
portmap_enable="NO"
sshd_enable="NO"
sendmail_enable="NO"
sendmail_submit_enable="NO"
sendmail_outbound_enable="NO"
sendmail_msp_queue_enable="NO"
hostname="openvpn"
devfs_enable="YES"
devfs_system_ruleset="devfsrules_common"
inet6_enable="YES"
ip6addrctl_enable="YES"
openvpn_enable="YES"
openvpn_if="tun"
openvpn_configfile="/mnt/keys/openvpn.conf"
openvpn_dir="/mnt/keys"
cloned_interfaces="tun"
gateway_enable="YES"
firewall_enable="YES"
firewall_script="/usr/local/etc/ipfw.rules"
Client
Code:
client
dev tun
proto udp
remote [my ddns here] 10011
resolv-retry infinite
nobind
persist-key
persist-tun
ca ca.crt
cert smarley.crt
key smarley.key
remote-cert-tls server
cipher AES-256-CBC
tls-auth ta.key 1
#dhcp-option DNS 0.0.0.0
#redirect-gateway def1
comp-lzo
verb 3
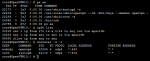
root@openvpn:/mnt/keys # ipfw list
00100 nat 1 ip from 172.16.8.0/24 to any out via epair2b
00200 nat 1 ip from any to any in via epair2b
65535 allow ip from any to any
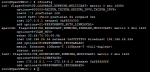
root@openvpn:/mnt/keys # ifconfig
lo0: flags=8049<UP,LOOPBACK,RUNNING,MULTICAST> metric 0 mtu 16384
options=600003<RXCSUM,TXCSUM,RXCSUM_IPV6,TXCSUM_IPV6>
inet6 ::1 prefixlen 128
inet6 fe80::1%lo0 prefixlen 64 scopeid 0x1
inet 127.0.0.1 netmask 0xff000000
nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL>
epair2b: flags=8843<UP,BROADCAST,RUNNING,SIMPLEX,MULTICAST> metric 0 mtu 1500
options=8<VLAN_MTU>
ether 02:ff:70:00:09:0b
inet 192.168.25.54 netmask 0xffffff00 broadcast 192.168.25.255
nd6 options=9<PERFORMNUD,IFDISABLED>
media: Ethernet 10Gbase-T (10Gbase-T <full-duplex>)
status: active
tun0: flags=8051<UP,POINTOPOINT,RUNNING,MULTICAST> metric 0 mtu 1500
options=80000<LINKSTATE>
inet 172.16.8.1 --> 172.16.8.2 netmask 0xffffffff
nd6 options=9<PERFORMNUD,IFDISABLED>