Mastakilla
Patron
- Joined
- Jul 18, 2019
- Messages
- 203
Hi everyone,
I'm currently working on replacing my TrueNAS Core system with TrueNAS Scale. My TrueNAS Core system has the legacy encryption on the "pool-level" (I know it's not really on the pool, but it applies to all datasets below) and requires me to enter a passphrase when booting up the system.
I'd like that same kind of encryption (but then the non-legacy equivalent) on my TrueNAS Scale as well, so
1) Requiring a passphrase to be entered at boot
2) Not having to worry about setting encryption for each dataset separately
I tried to set this up like this:
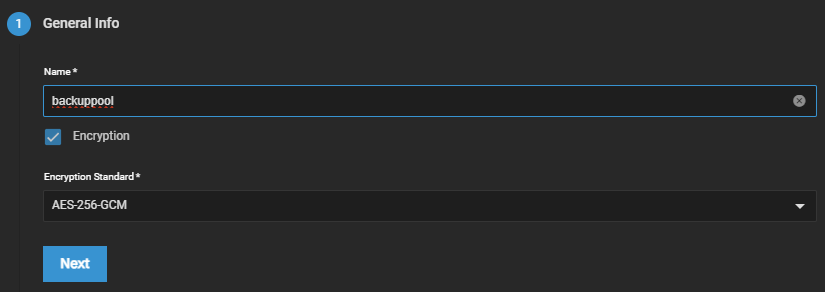
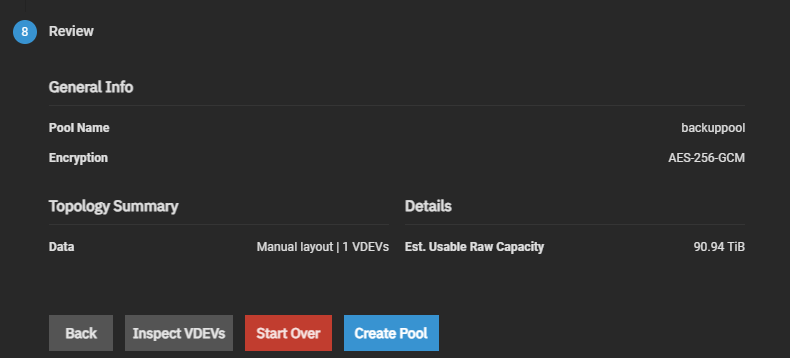
But apparently this sets it up using a keyfile instead of a passphrase (without giving the option to use a passphrase).
And when I want to change this later, I'm running into the following problem:
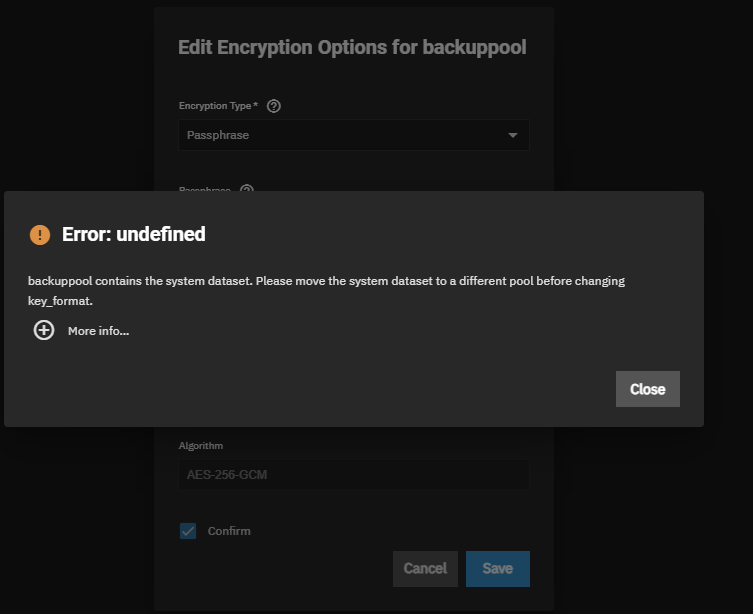
So what is the proper way of setting up my system dataset with passphrase protection?
I'm currently working on replacing my TrueNAS Core system with TrueNAS Scale. My TrueNAS Core system has the legacy encryption on the "pool-level" (I know it's not really on the pool, but it applies to all datasets below) and requires me to enter a passphrase when booting up the system.
I'd like that same kind of encryption (but then the non-legacy equivalent) on my TrueNAS Scale as well, so
1) Requiring a passphrase to be entered at boot
2) Not having to worry about setting encryption for each dataset separately
I tried to set this up like this:
But apparently this sets it up using a keyfile instead of a passphrase (without giving the option to use a passphrase).
And when I want to change this later, I'm running into the following problem:
Code:
Error: Traceback (most recent call last):
File "/usr/lib/python3/dist-packages/middlewared/job.py", line 427, in run
await self.future
File "/usr/lib/python3/dist-packages/middlewared/job.py", line 465, in __run_body
rv = await self.method(*([self] + args))
^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^
File "/usr/lib/python3/dist-packages/middlewared/schema/processor.py", line 177, in nf
return await func(*args, **kwargs)
^^^^^^^^^^^^^^^^^^^^^^^^^^^
File "/usr/lib/python3/dist-packages/middlewared/schema/processor.py", line 44, in nf
res = await f(*args, **kwargs)
^^^^^^^^^^^^^^^^^^^^^^^^
File "/usr/lib/python3/dist-packages/middlewared/plugins/pool_/dataset_encryption_operations.py", line 194, in change_key
verrors.check()
File "/usr/lib/python3/dist-packages/middlewared/service_exception.py", line 70, in check
raise self
middlewared.service_exception.ValidationErrors: [EINVAL] id: backuppool contains the system dataset. Please move the system dataset to a different pool before changing key_format.So what is the proper way of setting up my system dataset with passphrase protection?
