fundatus
Cadet
- Joined
- Apr 7, 2023
- Messages
- 2
Hey!
Even though there is decent SecureBoot support with Linux, TrueNAS SCALE currently does not support it out of the box unfortunately. So I went ahead and manually enabled that for my installation and I wanted to record my steps here for anyone who runs into the same problem in the future.
I used this reddit thread and the Debian docs to do this.
First you need a running TrueNAS SCALE installation, so in case you don't have that yet, go ahead and disable SecureBoot so that you can install TrueNAS. Do all of the following steps as root user. Since you'll need to interact with UEFI you also need to be physically present with the machine and connect a monitor to it.
Follow this tutorial to enable apt and add the upstream debian repositories.Then make sure that the packages "shim-signed", "shim-helpers-amd64-signed", "grub-efi-amd64-signed" and "sbsigntool" are installed:
Use "fdisk -l" to check for the Devide ID of your EFI partition. For me that was "/dev/sda2". Now add shim to your boot config by using efibootmgr (make sure to adjust the values of -d and -p according the EFI partition device ID):
Now create your own signing key:
Enroll that key:
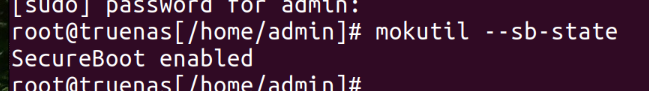
Reboot your machine. UEFI will ask you if you want to import the key, confirm that and type in the password you gave to mokutil before. Now check if the key was enrolled successfully:
Now add the key to the DKMS config located at "/etc/dkms/framework.conf" by adding these three lines:
Set some variables we need in the upcoming steps:
Sign the kernel:
Securely record the passphrase of your signing key to a environment variable:
Navigate to your kernel module folder and sign all the modules there:
Enrol the DKMS keys to your machine:
Reboot your machine and confirm enrolling the key. Now you can reboot again and enable SecureBoot. I also had to manaully add my EFI image (shimx64.efi) but I think that was a peculiarity of my system.
Hope this helped!
Even though there is decent SecureBoot support with Linux, TrueNAS SCALE currently does not support it out of the box unfortunately. So I went ahead and manually enabled that for my installation and I wanted to record my steps here for anyone who runs into the same problem in the future.
I used this reddit thread and the Debian docs to do this.
First you need a running TrueNAS SCALE installation, so in case you don't have that yet, go ahead and disable SecureBoot so that you can install TrueNAS. Do all of the following steps as root user. Since you'll need to interact with UEFI you also need to be physically present with the machine and connect a monitor to it.
Follow this tutorial to enable apt and add the upstream debian repositories.Then make sure that the packages "shim-signed", "shim-helpers-amd64-signed", "grub-efi-amd64-signed" and "sbsigntool" are installed:
Code:
$ apt update $ apt install shim-signed shim-helpers-amd64-signed grub-efi-amd64-signed sbsigntool
Code:
$ efibootmgr -c -d /dev/sda -p 2 -L debian-shim -l \\EFI\\debian\\shimx64.efi
Code:
$ mkdir -p /var/lib/shim-signed/mok/ $ cd /var/lib/shim-signed/mok/ $ openssl req -new -x509 -newkey rsa:2048 -keyout MOK.priv -outform DER -out MOK.der -days 36500 -subj "/CN=truenas/" $ openssl x509 -inform der -in MOK.der -out MOK.pem
Code:
$ mokutil --import /var/lib/shim-signed/mok/MOK.der
Code:
$ mokutil --test-key /var/lib/shim-signed/mok/MOK.der /var/lib/shim-signed/mok/MOK.der is already enrolled
Code:
mok_signing_key="/var/lib/shim-signed/mok/MOK.priv" mok_certificate="/var/lib/shim-signed/mok/MOK.der" sign_tool="/etc/dkms/sign_helper.sh"
Code:
$ VERSION="$(uname -r)" $ SHORT_VERSION="$(uname -r | cut -d . -f 1-2)" $ MODULES_DIR=/lib/modules/$VERSION $ KBUILD_DIR=/usr/src/linux-headers-$VERSION
Code:
$ sbsign --key /var/lib/shim-signed/mok/MOK.priv --cert MOK.pem "/boot/vmlinuz-$VERSION" --output "/boot/vmlinuz-$VERSION.tmp"
$ mv "/boot/vmlinuz-$VERSION.tmp" "/boot/vmlinuz-$VERSION"
Code:
$ read -s KBUILD_SIGN_PIN $ export KBUILD_SIGN_PIN
Code:
$ cd $MODULES_DIR $ for i in *.ko ; do sudo --preserve-env=KBUILD_SIGN_PIN "$KBUILD_DIR"/scripts/sign-file sha256 /var/lib/shim-signed/mok/MOK.priv /var/lib/shim-signed/mok/MOK.der "$i" ; done
Code:
mokutil --import /var/lib/dkms/mok.pub
Hope this helped!
