Joeman3000
Dabbler
- Joined
- Jun 26, 2015
- Messages
- 10
Recently my FreeNAS Mini (FreeNAS-9.10-STABLE-201605021851) won't join to my Samba AD DC anymore and will spit out the following message:
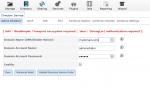
Screenshot of this is attached to this post.
My Samba AD DC (Version 4.2.10) is running Debian Jessie and from what I understand so far, it's not playing nice because of a security vulnerability that was patched in Samba. I tried switching to TLS encryption mode on FreeNAS, but it kicks back a message saying it doesn't want to use a self-signed certificate. I can join Windows machines to this AD DC, but FreeNAS doesn't seem to want to cooperate. FreeNAS will join perfectly fine to a Windows 2008 R2 AD DC though. I also fired up a fresh VM of FreeNAS and Debian Samba AD DC and it will still throw this error.
Anyone have an idea what could be going on?
Code:
{'info': 'BindSimple: Transport encryption required.', 'desc': 'Strong(er) authentication required'}.Screenshot of this is attached to this post.
My Samba AD DC (Version 4.2.10) is running Debian Jessie and from what I understand so far, it's not playing nice because of a security vulnerability that was patched in Samba. I tried switching to TLS encryption mode on FreeNAS, but it kicks back a message saying it doesn't want to use a self-signed certificate. I can join Windows machines to this AD DC, but FreeNAS doesn't seem to want to cooperate. FreeNAS will join perfectly fine to a Windows 2008 R2 AD DC though. I also fired up a fresh VM of FreeNAS and Debian Samba AD DC and it will still throw this error.
Anyone have an idea what could be going on?