-
Important Announcement for the TrueNAS Community.
The TrueNAS Community has now been moved. This forum has become READ-ONLY for historical purposes. Please feel free to join us on the new TrueNAS Community Forums
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Resource icon
Scripted installation of Nextcloud 28 in iocage jail 2018-03-23
- Thread starter danb35
- Start date
airflow
Contributor
- Joined
- May 29, 2014
- Messages
- 111
On the reverse proxy warning, see:

"The reverse proxy header configuration is incorrect, or you are accessing Nextcloud from a trusted proxy"
▶ Support intro Nextcloud version (eg, 20.0.5): 24.0.1 and 23.0.4 Operating system and version (eg, Ubuntu 20.04): FreeBSD 13.1, in a jail under TrueNAS CORE 13.0 Apache or nginx version (eg, Apache 2.4.25): Caddy 2.5.1 PHP version (eg, 7.4): 8.0.18 The issue you are facing: After...help.nextcloud.com
Do I understand correctly that the problem with the error message "The reverse proxy header configuration is incorrect, or you are accessing Nextcloud from a trusted proxy." could not be solved and should just be ignored? In the linked thread there is no outcome of the analysis.
danb35
Hall of Famer
- Joined
- Aug 16, 2011
- Messages
- 15,504
I haven't seen any explanation of that message that accounts for how I'm seeing it. The one response I got (a couple of months after the fact) was to add Cloudflare's IPs as trusted proxies, which would be irrelevant to me since I was access it entirely over my LAN.
I have been running nextcloud for while and everything is working properly. Now, I wanted to step it up a notch and actually want to install caddy on its own jail and set up a reverse proxy so that I can multiple sub-domain for my other apps. I have used this exact automation script along with others (heimdall, plex...). I did noticed when running nextcloud and heimdall they both already included Caddy. I found @danb35 script for installing Caddy. But how do I clean up the Caddy mess that already included when previously installed nextcloud and heimdall. What change do I need to make in the Caddy files?
danb35
Hall of Famer
- Joined
- Aug 16, 2011
- Messages
- 15,504
What about either of these do you think is a mess? Both Heimdall and Nextcloud, as I install them with my scripts, use Caddy as the web server--just as other guides/scripts/plugins use Apache or nginx as web servers. If you also want to use Caddy as a reverse proxy to allow remote access to internal resources, you have a few options:But how do I clean up the Caddy mess that already included when previously installed nextcloud and heimdall.
- Edit the Caddyfile in one of the existing installations to do this, and use your router to forward ports 80 and 443 to that jail
- Create a separate Caddy jail, edit its Caddyfile to act as a reverse proxy, and forward 80 and 443 there
- If you're using OPNsense for your router, install Caddy there and configure that Caddyfile accordingly
- ...or use the better-supported HAProxy, but then you aren't using Caddy--and I find it's a lot easier to write three lines of Caddyfile than click through 27 different steps of HAProxy configuration
Code:
{
email admin@mydomain
}
ombi.mydomain {
reverse_proxy 192.168.1.28:5000
}
bitwarden.mydomain {
reverse_proxy https://bitwarden.mydomain
}
opnsense.mydomain {
@denied not remote_ip 192.168.0.0/22
abort @denied
reverse_proxy localhost:81
}
It proxies any traffic from outside for Ombi and Bitwarden, but only accepts traffic from 192.168.0.0/22 (i.e., .0.x, .1.x, .2.x, or .3.x) for the OPNsense UI itself. And, as Caddy usually does, it handles certs, HTTPS redirect, TLS configuration, and all that other stuff automatically, all of which would need to be manually configured (and all in different places) if I were using HAProxy.
Caddy in my Heimdall jail handles proxies for resources I just use in my LAN and don't expose to the outside--I use the proxy in this case to (1) access those resources without having to remember wacky port numbers; and (2) add HTTPS, as browsers increasingly complain if you're using HTTP (and especially entering information via HTTP). I use an internal CA with this Caddy installation to issue certs, and it manages them perfectly.
So, if you want to use Caddy as a reverse proxy, how to go about it? Probably the simplest way to do it would be to forward ports 80 and 443 to your Nextcloud installation, and add the reverse proxy directives for other services to that Caddyfile. That's likely the simplest way to do it, as Nextcloud itself isn't behind a proxy, so it doesn't need to be told about one.
Failing that, Nextcloud needs to be told if it's behind a proxy. There's a good bit of discussion on that subject up-thread, and also what looks like some relevant stuff here:
Sorry, I don't meant to say they were a mess. They're perfectly neat and working nice haha. I'm just a bit OCD when it come to stuff just sitting there without getting use and I like to keep thing clean. Now, I don't know if the Caddy instances in nextcloud and heimdall would get use anymore if I created a new instances of Caddy in a separate jail.What about either of these do you think is a mess?
I'm sure the info you provided were great info, but it is a little bit over my head. So, what I am planning on doing would just be the 2nd option as you suggested. If I do that, then do I need to copy all the stuff in the Caddyfile within Nextcloud and Heimdall to the newly created Caddyfile in the new jail?
Here is the Caddyfile within nextcloud:
{
# debug
##acme_ca https://acme-staging-v02.api.letsencrypt.org/directory
email example@gmail.com
# default_sni example.com
}
example.us {
root * /usr/local/www/nextcloud
file_server
log {
output file /var/log/example.com.log
format single_field common_log
}
php_fastcgi 127.0.0.1:9000 {
env front_controller_active true
}
header {
# enable HSTS
Strict-Transport-Security max-age=31536000;
}
# client support (e.g. os x calendar / contacts)
redir /.well-known/carddav /remote.php/dav 301
redir /.well-known/caldav /remote.php/dav 301
redir /.well-known/webfinger /index.php/.well-known/webfinger 301
redir /.well-known/nodeinfo /index.php/.well-known/nodeinfo 301
# .htaccess / data / config / ... shouldn't be accessible from outside
@forbidden {
path /.htaccess
path /data/*
path /config/*
path /db_structure
path /.xml
path /README
path /3rdparty/*
path /lib/*
path /templates/*
path /occ
path /console.php
}
respond @forbidden 404
}
Here is the Caddyfile within heimdall:
:80 {
encode gzip
log {
output file /var/log/heimdall_access.log
}
root * /usr/local/www/html/public
file_server
php_fastcgi 127.0.0.1:9000
# Add reverse proxy directives here if desired
}
Last edited:
danb35
Hall of Famer
- Joined
- Aug 16, 2011
- Messages
- 15,504
Sorry to be blunt, but I think you're going to need to do some reading so that it isn't so far over your head. You're looking to expose portions of your home network to the Internet. The Internet is a dangerous place, and you have private data on your home network that you don't want to expose. Doing this safely takes some planning.but it is a little bit over my head.
No, that wouldn't work--that Caddy jail wouldn't have access to the data for either Nextcloud or Heimdall. The Caddyfile in that jail would consist only of reverse proxy statements, like this:So, what I am planning on doing would just be the 2nd option as you suggested. If I do that, then do I need to copy all the stuff in the Caddyfile within Nextcloud and Heimdall to the newly created Caddyfile in the new jail?
Code:
cloud.yourdomain {
reverse_proxy 192.168.100.100
}
heimdall.yourdomain {
reverse_proxy 192.168.100.101
}
radarr.yourdomain {
reverse_proxy 192.168.100.102:7878
}
...and so forth--a lot like the example I posted the other day, in fact.
The problem with doing it this way is that Nextcloud, in particular, needs to be configured to be behind a reverse proxy--and I really can't help you there, as I don't use it that way, but there's quite a bit of discussion up-thread on the question, as well as at the link I gave.
That's why I suggested doing the proxying in the Nextcloud jail. To do that, you'd just add the proxy statements (as above) to the Caddyfile there.
Edit: forgot to address this:
Yes, they would. Again, Caddy is acting as a web server in both of those cases. Like Apache and nginx, Caddy is a web server that can also act as a reverse proxy--it's just considerably easier to configure, for either application (or both together).Now, I don't know if the Caddy instances in nextcloud and heimdall would get use anymore if I created a new instances of Caddy in a separate jail.
Last edited:
I don't have an OPNsense router so I am not familiar with that configuration.That's why I suggested doing the proxying in the Nextcloud jail. To do that, you'd just add the proxy statements (as above) to the Caddyfile there.
I already have forward port 80 and 443 to my nextcloud and I can access it from outside of my home network for a while. Seem like my only option is to edit the Caddyfile located within nextcloud. Now, my questions are:If you also want to use Caddy as a reverse proxy to allow remote access to internal resources, you have a few options:
- Edit the Caddyfile in one of the existing installations to do this, and use your router to forward ports 80 and 443 to that jail
- Create a separate Caddy jail, edit its Caddyfile to act as a reverse proxy, and forward 80 and 443 there
- If you're using OPNsense for your router, install Caddy there and configure that Caddyfile accordingly
- ...or use the better-supported HAProxy, but then you aren't using Caddy--and I find it's a lot easier to write three lines of Caddyfile than click through 27 different steps of HAProxy configuration
- Can I add reverse proxy for things that I want to expose to the internet in the Caddyfile within nextcloud. AND also add reverse proxy for thing that I want to keep within my LAN in the Caddyfile within Heimdall?
- If the answer to the above question is yes. Then do I need to create an A record or anything like that from my domain registrar?
- What will happen to the stuff that I added to the Caddyfile within heimdall since I only forward port 80 and 443 to my nextcloud?
danb35
Hall of Famer
- Joined
- Aug 16, 2011
- Messages
- 15,504
Sure.Can I add reverse proxy for things that I want to expose to the internet in the Caddyfile within nextcloud. AND also add reverse proxy for thing that I want to keep within my LAN in the Caddyfile within Heimdall?
A CNAME would probably be the most appropriate, though it's with your DNS provider--who may, but need not, be the same as your domain registrar.If the answer to the above question is yes. Then do I need to create an A record or anything like that from my domain registrar?
It will only be accessible from within your LAN.What will happen to the stuff that I added to the Caddyfile within heimdall since I only forward port 80 and 443 to my nextcloud?
How would my Caddyfile in both instances look like? I don't want to just randomly taking thing out or add in things that I am not suppose to. I have the Caddyfile inlcluded above.Sure.
So this will work even I only have forward port 80 and 443 to the nextcloud Caddyfile? I am just wondering how my DNS provider would communicate with the Caddyfile within heimdall?It will only be accessible from within your LAN.
Also, I used namecheap for my DNS provider. What would the CNAME record look like?
What would host and value for the CNAME record be? I currently have this setup on namecheap.
Last edited:
danb35
Hall of Famer
- Joined
- Aug 16, 2011
- Messages
- 15,504
No, you shouldn't randomly be making changes to your server configuration for something that's exposed to the Internet, and really, you should be doing some homework of your own to understand how to do this in the Caddyfile. I think I've given enough examples up-topic to get you started; beyond that, you may be better off asking at the Caddy community if the Caddy docs aren't clear enough.I don't want to just randomly taking thing out or add in things that I am not suppose to.
You've forwarded ports 80 and 443 to the Nextcloud jail. The Caddyfile is the configuration file for the Caddy web server inside that jail.So this will work even I only have forward port 80 and 443 to the nextcloud Caddyfile?
I have no idea what you're asking here--why, and in what way, do you think your DNS provider would need to communicate with the Heimdall jail?I am just wondering how my DNS provider would communicate with the Caddyfile within heimdall?
I have nextcloud jail and heimdall in 2 different jail. So if I only forwarded port 80 and 443 to the nextcloud jail. How is the heimdall Caddyfile work?You've forwarded ports 80 and 443 to the Nextcloud jail. The Caddyfile is the configuration file for the Caddy web server inside that jail.
Yes. I think it would. Because I have Heimdall in a different jail and I thought all the network traffic currently right now within that jail would stay local. Even if I edit the Caddyfile in the Heimdall jail. Let's say when I type radarr.mydomain.us. How is my browser gonna know to either look into the Caddyfile within nextcloud or within heimdall?Do you think your DNS provider would need to communicate with the Heimdall jail?
- Joined
- Aug 19, 2017
- Messages
- 1,556
DNS will point to your public IP which is an interface on your router > your router will see traffic on port 80/443 and send that to the interface of the Nextcloud jail > Caddy will evaluate the domain request and if its nextcloud.mydomain it will process the request for nextcloud /> haimdall.mydomain will be forwarded to another ip and that webserver will process the request for haimdall > when the request has been accepted and processed the corresponding webserver will reply back to the client
This is basic stuff, listen to danb35 and study this before exposing your stuff online, setting up a VPN would probably be better
This is basic stuff, listen to danb35 and study this before exposing your stuff online, setting up a VPN would probably be better
I am trying. I just don't know where to start. That's why I am asking dumb questions. But I figure it wouldn't hurt to ask.This is basic stuff, listen to danb35 and study this before exposing your stuff online, setting up a VPN would probably be better
hello,
i used the script to install nextcloud; but i tweaked part of webservice ; ie i removed caddy and installed apache inside the jail.
is there some best way how to upgrade nextcloud only? ie keep all configs/db/ etc.. just nextcloud only. Currently running 24.0.3.
how do you guys manage that? maybe before any activity - the good idea is to create snapshot on dataset level jails/nextcloud and data-dataset nextcloud?
is it safe/ good idea to run official updater? https://xxxxx.ducxxxx.org/updater/
it shows something like >
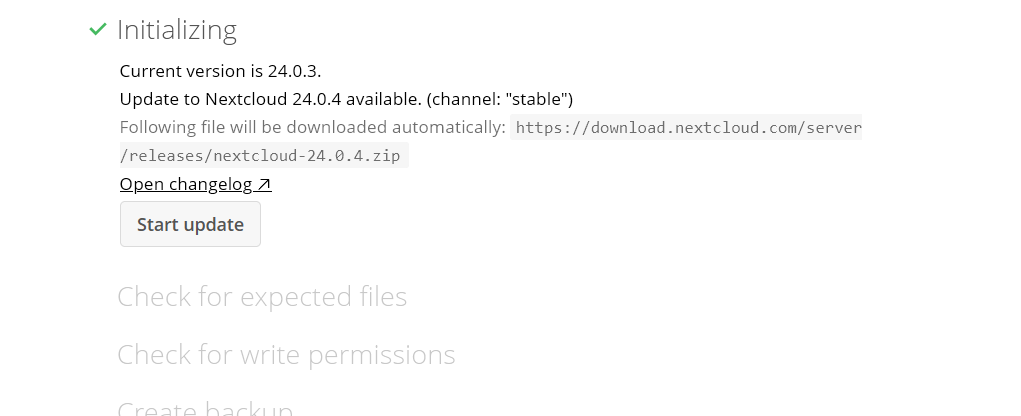
thanks!
i used the script to install nextcloud; but i tweaked part of webservice ; ie i removed caddy and installed apache inside the jail.
is there some best way how to upgrade nextcloud only? ie keep all configs/db/ etc.. just nextcloud only. Currently running 24.0.3.
how do you guys manage that? maybe before any activity - the good idea is to create snapshot on dataset level jails/nextcloud and data-dataset nextcloud?
is it safe/ good idea to run official updater? https://xxxxx.ducxxxx.org/updater/
it shows something like >
thanks!
- Joined
- Aug 19, 2017
- Messages
- 1,556
What I do (and its very scriptable), (1) put nextcloud in maintenance mode, (2) dump database and create snapshot of dataset for datastore and jail, (3) take nextcloud off maintenance mode, (4) backup datastore from snapshot, (5) backup application and database dump from snapshot
This method puts nextcloud out of action for just a few seconds and users general never notice it
This method puts nextcloud out of action for just a few seconds and users general never notice it
@garm and in which step and how do u upgrade?What I do (and its very scriptable), (1) put nextcloud in maintenance mode, (2) dump database and create snapshot of dataset for datastore and jail, (3) take nextcloud off maintenance mode, (4) backup datastore from snapshot, (5) backup application and database dump from snapshot
This method puts nextcloud out of action for just a few seconds and users general never notice it
do you mind to share 1-5 actions on script level?
thanks!
airflow
Contributor
- Joined
- May 29, 2014
- Messages
- 111
For me the process of updating nextcloud in the jail is very easy. All nextcloud-data resides on a separate dataset which is mapped into the jail. I just update the application by whatever method I used for installing (ports or pkg). Then I connect to the webinterface. Typically some maintenance/conversion is done by nextcloud itself to update it's data structures. Sometimes I add some missing indices to the db afterwards (a simple command). That's it.
Important Announcement for the TrueNAS Community.
The TrueNAS Community has now been moved. This forum will now become READ-ONLY for historical purposes. Please feel free to join us on the new TrueNAS Community Forums.Related topics on forums.truenas.com for thread: "Scripted installation of Nextcloud 28 in iocage jail"
Similar threads
- Replies
- 16
- Views
- 31K
- Replies
- 28
- Views
- 13K
- Replies
- 7
- Views
- 5K
