Hi all,
I am following the ixsystem guide to setup wireguad on the TrueNAS system. Once I rebooted the server I cannot see the wg0 interface.
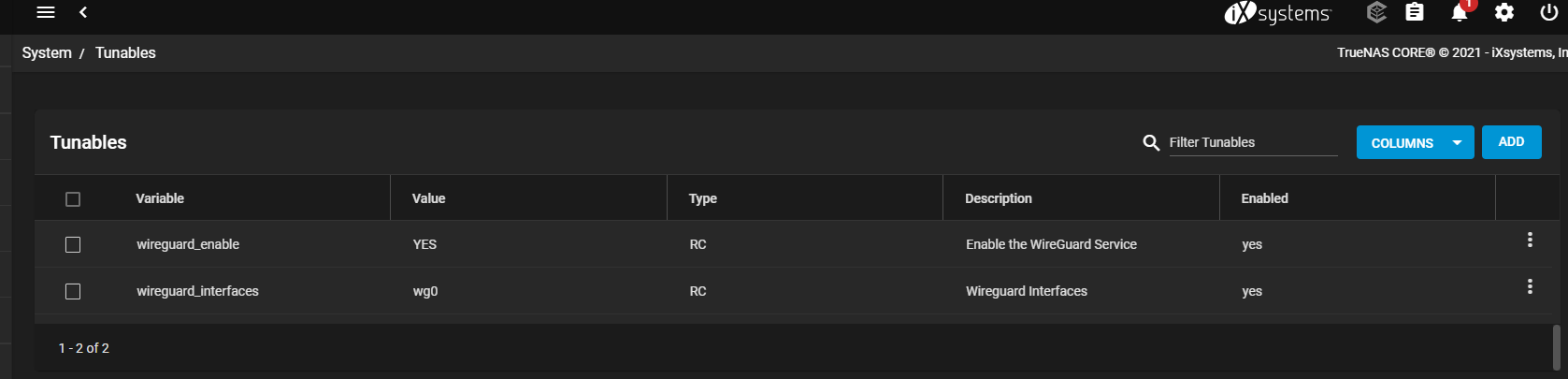
I am also not able to see the
Could anyone please advise?
I am following the ixsystem guide to setup wireguad on the TrueNAS system. Once I rebooted the server I cannot see the wg0 interface.
I am also not able to see the
in thewireguard_enable = YES
/etc/rc.conf fileCode:
root@freenas2[~]# ifconfig wg0 ifconfig: interface wg0 does not exist
Code:
root@freenas2[~]# wg-quick up wg0 [#] wireguard-go wg0 INFO: (wg0) 2021/05/13 13:05:06 Starting wireguard-go version 0.0.20200320 [#] wg setconf wg0 /tmp/tmp.WqhToS44/sh-np.BeievT [#] ifconfig wg0 inet 172.15.10.11/24 172.15.10.11 alias ifconfig: ioctl (SIOCAIFADDR): File exists [#] rm -f /var/run/wireguard/wg0.sock
Could anyone please advise?
