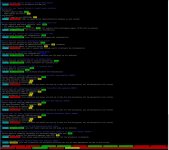
Through my experimentation with Proxmox (for other than TrueNAS), I just became aware of a vulnerability scanning tool (https://github.com/speed47/spectre-meltdown-checker) that works with FreeBSD and reports several vulnerabilities on my TrueNAS-12.0-U8.1 system.
Has anyone run it on version 12 or 13? Are there any/some/many false positives? How many of the issues found would not be of particular concern as long as TrueNAS is behind a firewall? What if I wanted to expose some plug-ins/ports (e.g. Plex Server and UnifiController) to the internet? Should I just plain avoid doing that?
Also, some of the mitigations are flagged as having medium or high impact, or potentially significant impact depending on the use of the feature that's affected I presume. For some or all of those (found at the link above), in balance might I be better to leave them unmitigated since they are behind a firewall? There is a post on this forum by someone who turned off all OS mitigations implemented. Not sure I want to go there.
In my case I'll certainly have to look at a BIOS upgrade because the last time I checked for one was maybe 3-5 years ago when I was running Windows on the machine I now use for TrueNAS. I do have to consider that the system may be too old for BIOS and/or OS level mitigations and consider either limiting how I use it even behind a firewall, or upgrade the h/w.
I've attached the output from the script and the colorful summary the script provides in the shell.
Any info would be appreciated.
Has anyone run it on version 12 or 13? Are there any/some/many false positives? How many of the issues found would not be of particular concern as long as TrueNAS is behind a firewall? What if I wanted to expose some plug-ins/ports (e.g. Plex Server and UnifiController) to the internet? Should I just plain avoid doing that?
Also, some of the mitigations are flagged as having medium or high impact, or potentially significant impact depending on the use of the feature that's affected I presume. For some or all of those (found at the link above), in balance might I be better to leave them unmitigated since they are behind a firewall? There is a post on this forum by someone who turned off all OS mitigations implemented. Not sure I want to go there.
In my case I'll certainly have to look at a BIOS upgrade because the last time I checked for one was maybe 3-5 years ago when I was running Windows on the machine I now use for TrueNAS. I do have to consider that the system may be too old for BIOS and/or OS level mitigations and consider either limiting how I use it even behind a firewall, or upgrade the h/w.
I've attached the output from the script and the colorful summary the script provides in the shell.
Any info would be appreciated.