Hello everyone
TrueNas has an integrated OpenVPN server and client service, easy to setup easy to start
However when I started my OpenVPN server, I can reach my TrueNAS throught the VPN but nothing more than that
I can ping my server
I can access my shares which is one of my goal
how to access the rest of my network behind this ? like another server ?
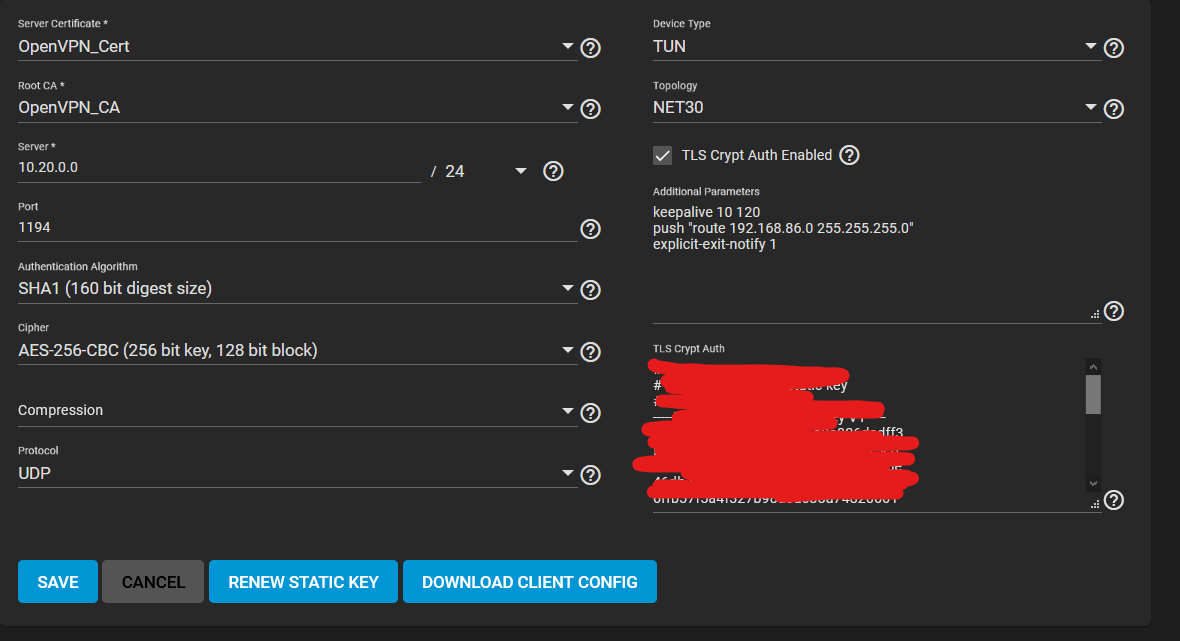
My server config:
My server log:
My client side route table
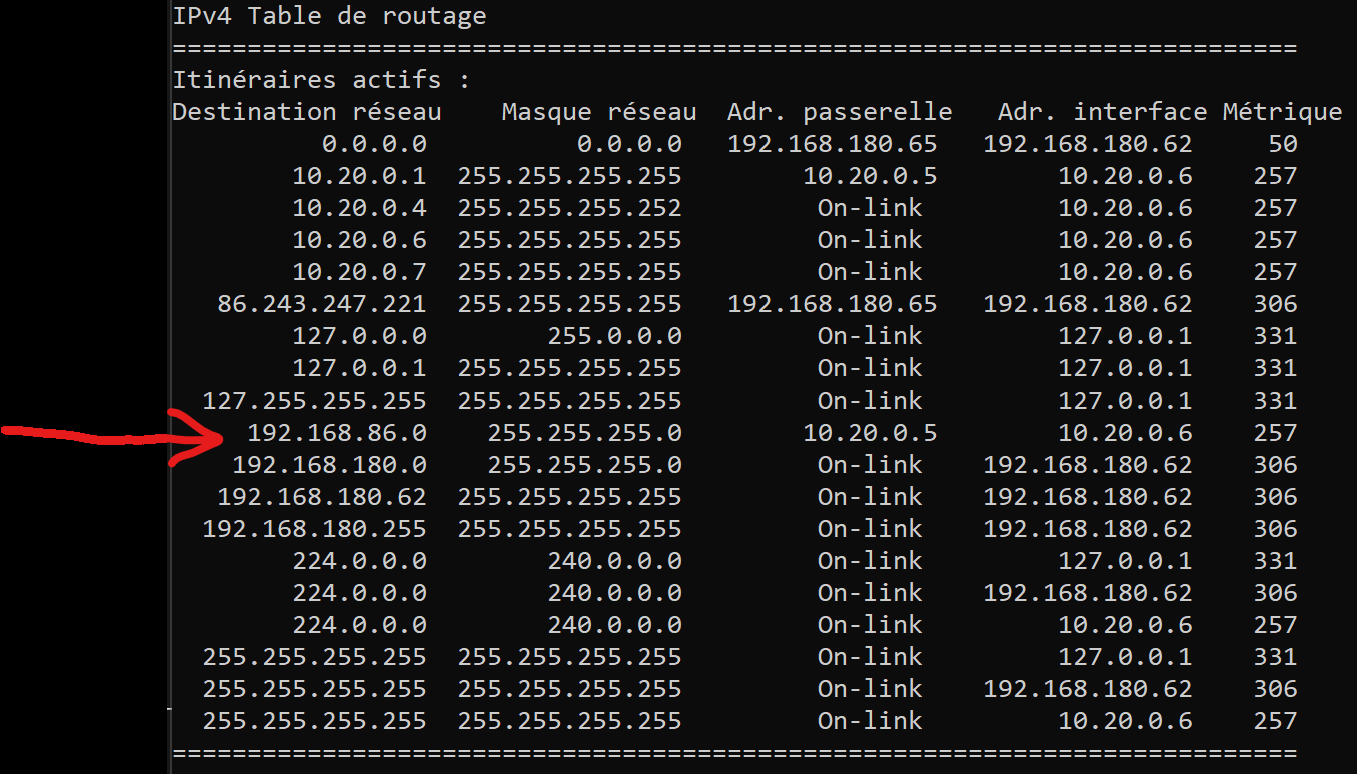
except my TrueNAS server I cannot access anything else, maybe a firewall rule? or a missing route ?
thanks for your help
TrueNas has an integrated OpenVPN server and client service, easy to setup easy to start
However when I started my OpenVPN server, I can reach my TrueNAS throught the VPN but nothing more than that
I can ping my server
I can access my shares which is one of my goal
how to access the rest of my network behind this ? like another server ?
My server config:
My server log:
Code:
Sat Jan 16 12:35:25 2021 OpenVPN 2.4.8 amd64-portbld-freebsd12.0 [SSL (OpenSSL)] [LZO] [LZ4] [MH/RECVDA] [AEAD] built on Dec 9 2020 Sat Jan 16 12:35:25 2021 library versions: OpenSSL 1.1.1h-freebsd 22 Sep 2020, LZO 2.10 Sat Jan 16 12:35:25 2021 Diffie-Hellman initialized with 2048 bit key Sat Jan 16 12:35:25 2021 Failed to extract curve from certificate (UNDEF), using secp384r1 instead. Sat Jan 16 12:35:25 2021 ECDH curve secp384r1 added Sat Jan 16 12:35:25 2021 Outgoing Control Channel Encryption: Cipher 'AES-256-CTR' initialized with 256 bit key Sat Jan 16 12:35:25 2021 Outgoing Control Channel Encryption: Using 256 bit message hash 'SHA256' for HMAC authentication Sat Jan 16 12:35:25 2021 Incoming Control Channel Encryption: Cipher 'AES-256-CTR' initialized with 256 bit key Sat Jan 16 12:35:25 2021 Incoming Control Channel Encryption: Using 256 bit message hash 'SHA256' for HMAC authentication Sat Jan 16 12:35:25 2021 ROUTE_GATEWAY 192.168.86.1/255.255.255.0 IFACE=re0 HWADDR=70:85:c2:7d:88:9d Sat Jan 16 12:35:25 2021 TUN/TAP device /dev/tun0 opened Sat Jan 16 12:35:25 2021 /sbin/ifconfig tun0 10.20.0.1 10.20.0.2 mtu 1500 netmask 255.255.255.255 up Sat Jan 16 12:35:25 2021 /sbin/route add -net 10.20.0.0 10.20.0.2 255.255.255.0 add net 10.20.0.0: gateway 10.20.0.2 Sat Jan 16 12:35:25 2021 Could not determine IPv4/IPv6 protocol. Using AF_INET6 Sat Jan 16 12:35:25 2021 Socket Buffers: R=[42080->42080] S=[9216->9216] Sat Jan 16 12:35:25 2021 setsockopt(IPV6_V6ONLY=0) Sat Jan 16 12:35:25 2021 UDPv6 link local (bound): [AF_INET6][undef]:1194 Sat Jan 16 12:35:25 2021 UDPv6 link remote: [AF_UNSPEC] Sat Jan 16 12:35:25 2021 GID set to nobody Sat Jan 16 12:35:25 2021 UID set to nobody Sat Jan 16 12:35:25 2021 MULTI: multi_init called, r=256 v=256 Sat Jan 16 12:35:25 2021 IFCONFIG POOL: base=10.20.0.4 size=62, ipv6=0 Sat Jan 16 12:35:25 2021 Initialization Sequence Completed Sat Jan 16 12:35:25 2021 MYIPADDRESS:58483 TLS: Initial packet from [AF_INET6]::ffff:86.243.247.221:58483, sid=5ccbf123 a88c7b97 Sat Jan 16 12:35:25 2021 MYIPADDRESS:58483 VERIFY KU OK Sat Jan 16 12:35:25 2021 MYIPADDRESS:58483 Validating certificate extended key usage Sat Jan 16 12:35:25 2021 MYIPADDRESS:58483 ++ Certificate has EKU (str) TLS Web Client Authentication, expects TLS Web Client Authentication Sat Jan 16 12:35:25 2021 MYIPADDRESS:58483 VERIFY EKU OK Sat Jan 16 12:35:25 2021 MYIPADDRESS:58483 VERIFY OK: depth=0, CN=MyVPN, C=***, ST=***, L=***, O=***, OU=***, emailAddress=***@***.*** Sat Jan 16 12:35:25 2021 MYIPADDRESS:58483 peer info: IV_VER=3.git::662eae9a Sat Jan 16 12:35:25 2021 MYIPADDRESS:58483 peer info: IV_PLAT=win Sat Jan 16 12:35:25 2021 MYIPADDRESS:58483 peer info: IV_NCP=2 Sat Jan 16 12:35:25 2021 MYIPADDRESS:58483 peer info: IV_TCPNL=1 Sat Jan 16 12:35:25 2021 MYIPADDRESS:58483 peer info: IV_PROTO=2 Sat Jan 16 12:35:25 2021 MYIPADDRESS:58483 peer info: IV_AUTO_SESS=1 Sat Jan 16 12:35:25 2021 MYIPADDRESS:58483 peer info: IV_GUI_VER=OCWindows_3.2.2-1455 Sat Jan 16 12:35:25 2021 MYIPADDRESS:58483 peer info: IV_SSO=openurl Sat Jan 16 12:35:25 2021 MYIPADDRESS:58483 Control Channel: TLSv1.3, cipher TLSv1.3 TLS_AES_256_GCM_SHA384, 2048 bit RSA Sat Jan 16 12:35:25 2021 MYIPADDRESS:58483 [MyVPN] Peer Connection Initiated with [AF_INET6]::ffff:86.243.247.221:58483 Sat Jan 16 12:35:25 2021 MyVPN/MYIPADDRESS:58483 MULTI_sva: pool returned IPv4=10.20.0.6, IPv6=(Not enabled) Sat Jan 16 12:35:25 2021 MyVPN/MYIPADDRESS:58483 MULTI: Learn: 10.20.0.6 -> MyVPN/86.243.247.221:58483 Sat Jan 16 12:35:25 2021 MyVPN/MYIPADDRESS:58483 MULTI: primary virtual IP for MyVPN/86.243.247.221:58483: 10.20.0.6 Sat Jan 16 12:35:25 2021 MyVPN/MYIPADDRESS:58483 PUSH: Received control message: 'PUSH_REQUEST' Sat Jan 16 12:35:25 2021 MyVPN/MYIPADDRESS:58483 SENT CONTROL [MyVPN]: 'PUSH_REPLY,route 192.168.86.0 255.255.255.0,route 10.20.0.1,topology net30,ping 10,ping-restart 120,ifconfig 10.20.0.6 10.20.0.5,peer-id 0,cipher AES-256-GCM' (status=1) Sat Jan 16 12:35:25 2021 MyVPN/MYIPADDRESS:58483 Data Channel: using negotiated cipher 'AES-256-GCM' Sat Jan 16 12:35:25 2021 MyVPN/MYIPADDRESS:58483 Outgoing Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key Sat Jan 16 12:35:25 2021 MyVPN/MYIPADDRESS:58483 Incoming Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
My client side route table
except my TrueNAS server I cannot access anything else, maybe a firewall rule? or a missing route ?
thanks for your help
