glauco
Guru
- Joined
- Jan 30, 2017
- Messages
- 526
I have two zfs pools: MyVolume and replica.
MyVolume is my main pool. It's made up of two SSDs that I've set up as Self-Encrypting Drives (SEDs) by following the instructions at https://www.truenas.com/docs/core/coretutorials/storage/sed/ As you can see in the first screenshot, the Storage > Pools web page shows no padlock next to it.
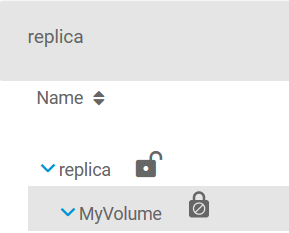
The pool named replica was encrypted at creation time and is the target of my replication experiments. As I imported it and decrypted it, it shows an open padlock icon next to its root dataset (second screenshot). The dataset right below it, called MyVolume, is the target of a periodic replication task I've set up. As you can see, it has that padlock icon that means (quoting https://www.truenas.com/docs/core/c.../storageencryption/#encrypting-a-storage-pool ):
A Dataset on an encrypted pool with encryption properties that don’t match the root dataset have this icon:

NOTE: An unencrypted pool with an encrypted dataset also shows this icon:

At the command line, I can see the data in replica/MyVolume, so why do I get that icon? Is it because MyVolume is deployed on SEDs?
Should I be worried that I might not be able to restore replica/MyVolume if my main TrueNAS pool is destroyed?
What am I failing to understand?
Thanks.
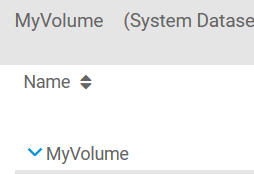
MyVolume is my main pool. It's made up of two SSDs that I've set up as Self-Encrypting Drives (SEDs) by following the instructions at https://www.truenas.com/docs/core/coretutorials/storage/sed/ As you can see in the first screenshot, the Storage > Pools web page shows no padlock next to it.
The pool named replica was encrypted at creation time and is the target of my replication experiments. As I imported it and decrypted it, it shows an open padlock icon next to its root dataset (second screenshot). The dataset right below it, called MyVolume, is the target of a periodic replication task I've set up. As you can see, it has that padlock icon that means (quoting https://www.truenas.com/docs/core/c.../storageencryption/#encrypting-a-storage-pool ):
A Dataset on an encrypted pool with encryption properties that don’t match the root dataset have this icon:

NOTE: An unencrypted pool with an encrypted dataset also shows this icon:

At the command line, I can see the data in replica/MyVolume, so why do I get that icon? Is it because MyVolume is deployed on SEDs?
Should I be worried that I might not be able to restore replica/MyVolume if my main TrueNAS pool is destroyed?
What am I failing to understand?
Thanks.
