vlad-infra-admin
Dabbler
- Joined
- Dec 18, 2022
- Messages
- 13
Hello,
I am wondering if I can some how "disable password" for root, but not for others.
I mean set it with a reply to clients "root@server: Permission denied (publickey)".
Technically password for root is disabled. I use public key for this account, but if I login it will ask for a password.
It will not be accepted even if type a correct one.
In my company where I am at the moment we have our internal network scanned and tested for weak root passwords.
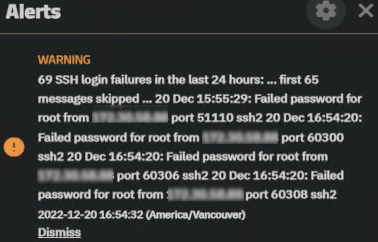
So I keep seeing this message in TrueNAS Scale 22.12.0.
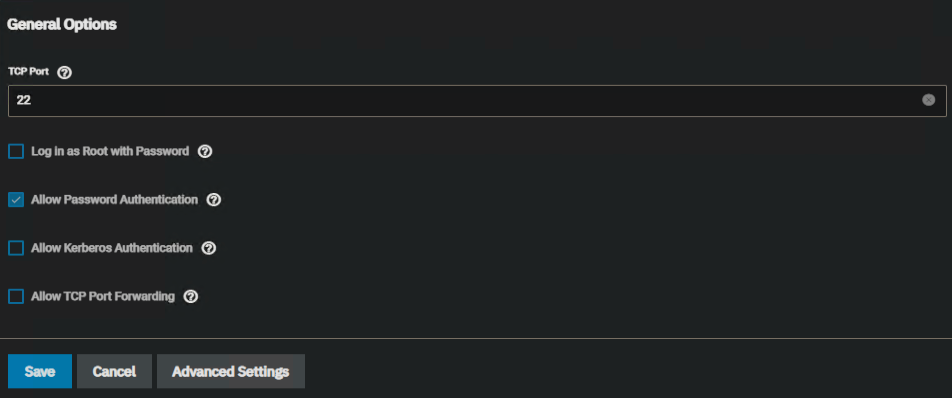
My configuration
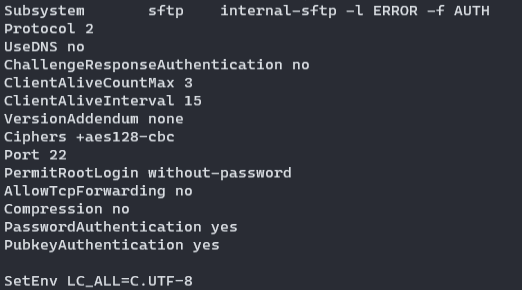
If it would be a manual configuration I would set it to "PermitRootLogin prohibit-password" instead of "PermitRootLogin without-password"
So is there a proper way to configure it?
I am wondering if I can some how "disable password" for root, but not for others.
I mean set it with a reply to clients "root@server: Permission denied (publickey)".
Technically password for root is disabled. I use public key for this account, but if I login it will ask for a password.
It will not be accepted even if type a correct one.
In my company where I am at the moment we have our internal network scanned and tested for weak root passwords.
So I keep seeing this message in TrueNAS Scale 22.12.0.
My configuration
If it would be a manual configuration I would set it to "PermitRootLogin prohibit-password" instead of "PermitRootLogin without-password"
So is there a proper way to configure it?
