shpokas
Dabbler
- Joined
- Oct 3, 2014
- Messages
- 32
Hi,
is it possible to get FreeIPA authentication with Samba sharing on TrueNAS 12-U1 ? I've read it was last time working well on FreeNAS 10.
There are hints in JIRA it can be done, but is there a guide maybe?
What works for me:
Any hints or help is much appreciated.
Thanks!
shpokas
is it possible to get FreeIPA authentication with Samba sharing on TrueNAS 12-U1 ? I've read it was last time working well on FreeNAS 10.
There are hints in JIRA it can be done, but is there a guide maybe?
What works for me:
- FreeIPA working for years, authenticating users, etc.
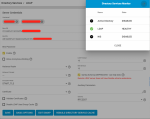
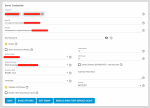
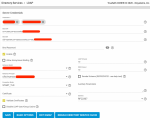
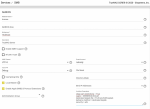
- LDAP configured and working on TrueNAS, I can ssh to TrueNAS box with FreeIPA user, getent works and lists users and groups.
- ipa-adtrust-install was run on FreeIPA - I needed ipaNTHash attribute for FreeRADIUS authentication - this is working fine.
- Samba sharing with FreeIPA users - if I try to access samba share with FreeIPA user, I see "NT_STATUS_NO_SUCH_USER" error in /var/log/samba4/auth_audit.log
- Cannot enable "Samba Schema (DEPRECATED - see help text)" - I get a message that "Remote LDAP server does not have Samba schema extensions."
But do I really need it enabled, particularly since it is "DEPRECATED - see help text" ?
Any hints or help is much appreciated.
Thanks!
shpokas