ghostwolf59
Contributor
- Joined
- Mar 2, 2013
- Messages
- 165
Thought I share this with anyone interested...
The other day I decided to install clamAV *again* after rebuilding my freenas under 11.3-STABLE
Basis of what I've done was nicked from this thread (https://www.ixsystems.com/community/threads/how-to-install-clamav-on-freenas-v11.56790/) but since its old I thought I post what I've done under 11.3
1. Create your new clamav iocage jail as a root user on server level
iocage create -n clamav -r 11.3-RELEASE ip4_addr="vnet0|(your static ip for jail)/24" defaultrouter="your gateway ip" vnet="on" allow_raw_sockets="1" boot="on"
2. If jail wasnt started automatically, Start jail and open shell from within the jail
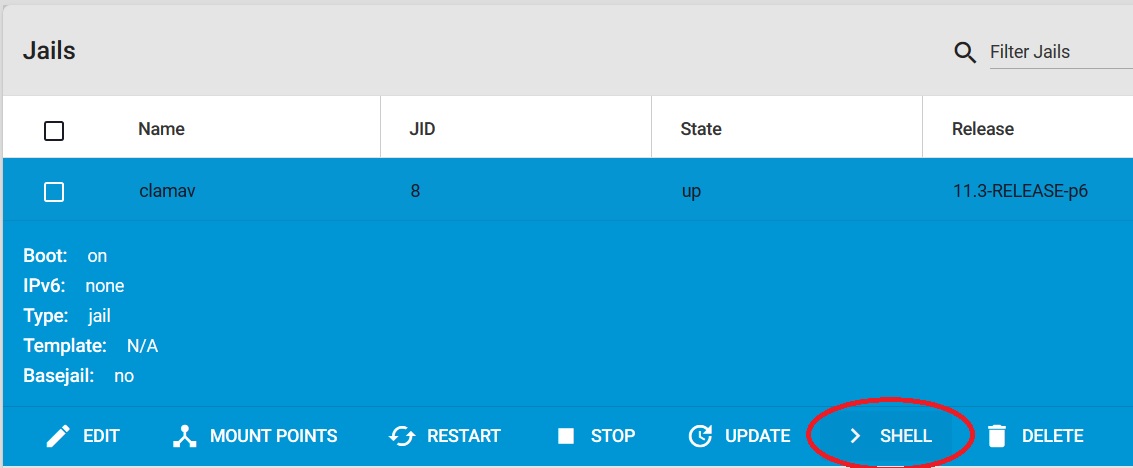
3. update /etc/pkg/FreeBSD.conf (change quarterly to latest)
The following is optional, but its easier since I personally prefer to work from Bitvise SSH Client (way better than putty ;) )
Its easy enough to disable this once done !
4. set root password
$passwd xyz (remember the password as this is needed once using a different ssh client)
5. edit /etc/ssh/sshd_config and unhash PermitRootLogin and set it to "yes" do the same with PasswordAuthentication and set the flag to "yes"
6. do
$sysrc sshd_enable=yes
7. do
$service sshd start
8. Close shell and login with direct using Bitwise SSH Client and take it from there...
i.e clamav jail ip address userid (root) and password previously setup
9. Once in the jail do
$pkg update && pkg upgrade -y
10. do
$portsnap fetch extract
11. do
$cd /usr/ports/ports-mgmt/portmaster
12. do
$make install clean
13. do
$cd /usr/ports/security/clamav
14. do
$make install clean
The following I prefer to do on server level, so exit out from the jail and start another ssh session as server level root user
15. Adding local directories of scantarget storage...
iocage exec clamav mkdir -p /mnt/scantarget # this is the root folder holding my mapped drives and folders
iocage exec clamav mkdir -p /mnt/scantarget/Accounts # this is one of my targets Id like to scan later
.
.
16. Create the script folder (to be mapped tp external *outside the jail itself* later
iocage exec clamav mkdir -p /mnt/script # this is where two shell scripts will reside mapped to an external location
17. Map your scantargets...
iocage fstab -a clamav /mnt/STORE01/Accounts /scantarget/Accounts nullfs rw 0 0
.
.
.
18. Map your external script folder to jail script folder
iocage fstab -a clamav /mnt/JailSSD/apps/clamav /script nullfs rw 0 0 # /mnt/JailSSD/apps/clamav needs exist prior
19. two shell scripts needs to be created and stored in /mnt/JailSSD/apps/clamav/
These two scripts will allow you to
1. Enable concurrent scan jobs to run without conflicts
2. pass subfolder to be scanned as a parameters into the job
Note: folder names containing spaces require the scantarget parameter to be surrounded by ""
i.e /mnt/JailSSD/apps/clamav/run_clamav_scan.sh "folder name with spaces"
3. Limit the virusdb to be updated once every 24 hours or if/when /var/log/clamav/freshclam-[yyyymmdd].log inside the clamav jail is missing
avscan.sh
run_clamav_scan.sh
20. Change the permission on both these shell scripts to...
chown 0:0
chmod 500
21. The run_clamav_scan.sh script needs to be run on server root level *generally you setup a cron task to kick it off regularly
Cron Task:
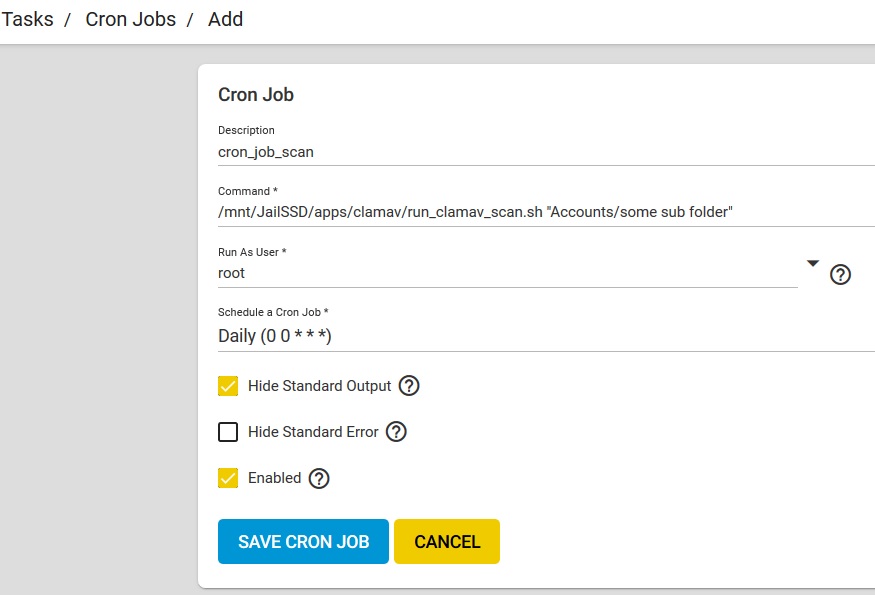
22. Thats it!
If you want to kick off the job manually, login as root on the server and do
$/mnt/JailSSD/apps/clamav/run_clamav_scan.sh "scan target folder name"
**** 'scan target folder name' as defined within the clamav jail scantarget or use the root folder name and append subfolder to limit the scan"
IF you dont what the keep the root access to clamav jail
1. edit /etc/ssh/sshd_config and unhash PermitRootLogin and set it to "no" do the same with PasswordAuthentication and set the flag to "no"
2. do
$sysrc sshd_enable=no
7. do
$service sshd restart
let me know if I missed something - Works pretty good for me, but noticed some issues when scanning large content *memory and timeout issues*, but this has nothing to do with the overall setup as far as I can see
The other day I decided to install clamAV *again* after rebuilding my freenas under 11.3-STABLE
Basis of what I've done was nicked from this thread (https://www.ixsystems.com/community/threads/how-to-install-clamav-on-freenas-v11.56790/) but since its old I thought I post what I've done under 11.3
1. Create your new clamav iocage jail as a root user on server level
iocage create -n clamav -r 11.3-RELEASE ip4_addr="vnet0|(your static ip for jail)/24" defaultrouter="your gateway ip" vnet="on" allow_raw_sockets="1" boot="on"
2. If jail wasnt started automatically, Start jail and open shell from within the jail
3. update /etc/pkg/FreeBSD.conf (change quarterly to latest)
The following is optional, but its easier since I personally prefer to work from Bitvise SSH Client (way better than putty ;) )
Its easy enough to disable this once done !
4. set root password
$passwd xyz (remember the password as this is needed once using a different ssh client)
5. edit /etc/ssh/sshd_config and unhash PermitRootLogin and set it to "yes" do the same with PasswordAuthentication and set the flag to "yes"
6. do
$sysrc sshd_enable=yes
7. do
$service sshd start
8. Close shell and login with direct using Bitwise SSH Client and take it from there...
i.e clamav jail ip address userid (root) and password previously setup
9. Once in the jail do
$pkg update && pkg upgrade -y
10. do
$portsnap fetch extract
11. do
$cd /usr/ports/ports-mgmt/portmaster
12. do
$make install clean
13. do
$cd /usr/ports/security/clamav
14. do
$make install clean
The following I prefer to do on server level, so exit out from the jail and start another ssh session as server level root user
15. Adding local directories of scantarget storage...
iocage exec clamav mkdir -p /mnt/scantarget # this is the root folder holding my mapped drives and folders
iocage exec clamav mkdir -p /mnt/scantarget/Accounts # this is one of my targets Id like to scan later
.
.
16. Create the script folder (to be mapped tp external *outside the jail itself* later
iocage exec clamav mkdir -p /mnt/script # this is where two shell scripts will reside mapped to an external location
17. Map your scantargets...
iocage fstab -a clamav /mnt/STORE01/Accounts /scantarget/Accounts nullfs rw 0 0
.
.
.
18. Map your external script folder to jail script folder
iocage fstab -a clamav /mnt/JailSSD/apps/clamav /script nullfs rw 0 0 # /mnt/JailSSD/apps/clamav needs exist prior
19. two shell scripts needs to be created and stored in /mnt/JailSSD/apps/clamav/
These two scripts will allow you to
1. Enable concurrent scan jobs to run without conflicts
2. pass subfolder to be scanned as a parameters into the job
Note: folder names containing spaces require the scantarget parameter to be surrounded by ""
i.e /mnt/JailSSD/apps/clamav/run_clamav_scan.sh "folder name with spaces"
3. Limit the virusdb to be updated once every 24 hours or if/when /var/log/clamav/freshclam-[yyyymmdd].log inside the clamav jail is missing
avscan.sh
Code:
#!/bin/sh
### Notes ###
## Shell scripts to update the ClamAV definations, then run a scan and prepare an email template ##
## This script is called from a master script running as a cron job on the FreeNAS server ##
## Master script is: run_clamav_scan.sh ##
##
## Instructions: ##
## 1) To use this you need to create a Jail called "ClamAV" ##
## 2) Open a Shall to the jail and then run: "pkg update" ##
## 3) The run: "pkg install clamav" ##
## 4) You can then "exit" the Jail ##
## 5) Add the windows shares you wish to scan by using the Jail Add Storage feature ##
## 5a) Add the shares to same location you use in the variable: "scanlocation" ##
## 6) Setp a cronjob on the FreeNAS server to run a shell script on the FreeNAS server: "run_clamav_scan.sh" ##
## 7) The shell script "run_clamav_scan.sh" then connects to the Jail and runs this script. ##
## 8) Once finished, the "run_clamav_scan.sh" script emails a log to the email entered in the variable: "to_email" ##
##
## https://www.clamav.net/ ##
## ClamAV® is an open source (GPL) anti-virus engine used in a variety of situations including email scanning, web scanning, ##
## and end point security. It provides a number of utilities including a flexible and scalable multi-threaded daemon, a command ##
## line scanner and an advanced tool for automatic database updates. ##
pid=${1}
#echo "pid argument ${pid}"
targetdir=${2}
#targetdir=${@}
#echo "targetdir ${targetdir}"
## Top directory of the files/directories you wish to scan, i.e. the "Jail Add Storage" locations ##
scanlocation="/scantarget/${targetdir}"
### Parameters ###
## update email address ##
to_email="your_email@address"
NOW=$(date "+%Y%m%d")
### Only Update anti-virus definitions once per day identified by date ###
## Look for existing freshclam.log for todays date - if found, ignore updating the virus def
## If NOT found, clean up any old freshclam-*.log files stored on the system and re-created it along with fresh virus def
file="/var/log/clamav/freshclam-${NOW}.log"
if [ ! -f "$file" ]
then
echo "$0: File '${file}' not found."
## Clean up old clam files and create a fresh up to date version
f=0
for file in /var/log/clamav/freshclam*.log
do
if [ -f "$file" ]
then
rm -f $file
((f++))
fi
done
echo "number of files removed: $f"
echo "creating a new freshclam"
freshclam -l /var/log/clamav/freshclam-${NOW}.log
fi
#freshclam -l /var/log/clamav/freshclam${pid}.log
### End ###
echo "scan starting targetting ${scanlocation}"
### Run the anti-virus scan uniquely identified by pid ###
started=$(date "+ClamAV Scan started at: %Y-%m-%d %H:%M:%S")
clamscan -i -r -l /var/log/clamav/clamscan${pid}.log "${scanlocation}"
finished=$(date "+ClamAV Scan finished at: %Y-%m-%d %H:%M:%S")
### End ###
### prepare the email - pid makes the file unique ###
## Set email headers ##
(
echo "To: ${to_email}"
echo "Subject: ${started}"
echo "MIME-Version: 1.0"
# echo "Content-Type: text/html" ## does not work with 11.3 for now
echo -e "\\r\\n"
) >> /tmp/clamavemail${pid}.tmp
## Set email body ##
(
echo "<pre style=\"font-size:14px\">"
echo ""
echo "scantarget ${scanlocation}"
echo ""
echo "${started}"
echo ""
echo "${finished}"
echo ""
echo "--------------------------------------"
echo "ClamAV Scan Summary pid ${pid}"
echo "--------------------------------------"
tail -n 8 /var/log/clamav/clamscan${pid}.log
echo ""
echo ""
echo "--------------------------------------"
echo "freshclam log file"
echo "--------------------------------------"
tail -n +2 /var/log/clamav/freshclam-${NOW}.log
echo ""
echo ""
echo "--------------------------------------"
echo "clamav log file"
echo "--------------------------------------"
tail -n +4 /var/log/clamav/clamscan${pid}.log | sed -e :a -e '$d;N;2,10ba' -e 'P;D'
echo "</pre>"
) >> /tmp/clamavemail${pid}.tmp
### Tidy Up ###
## Delete the freshclam log in preparation of a new log ##
#rm /var/log/clamav/freshclam-${NOW}.log ## Not required since file is created once per day i.e no need to refresh clam virus def for every run
## Delete the clamscan log in preparation of a new log ##
rm /var/log/clamav/clamscan${pid}.log
### End ###
run_clamav_scan.sh
Code:
#!/bin/sh
### Execute a shall script on the ClamAV jail, which updates the Anti-Virus definations and then runs a scan ###
## iocage = FreeNAS v11.1 and above (yes FreeNAS v11.1 supports both warden and iocage [via CLI]) ##
## Define the location where the "avscan.sh" shell script is located on the jail:
scriptlocation="/script/"
# Grab pid id from started process and sent it to tmp file so second process can pick it up
pid=$$
#echo "pid id ${pid}"
# Grab target directory parameter
scantarget=${@}
## Execute the script passing pid and target path ##
iocage exec clamav "$scriptlocation"avscan.sh "${pid}" "${scantarget}"
## email the log ##
sendmail -t < /mnt/JailSSD/iocage/jails/clamav/root/tmp/clamavemail${pid}.tmp
## Delete the log file ##
rm /mnt/JailSSD/iocage/jails/clamav/root/tmp/clamavemail${pid}.tmp
20. Change the permission on both these shell scripts to...
chown 0:0
chmod 500
21. The run_clamav_scan.sh script needs to be run on server root level *generally you setup a cron task to kick it off regularly
Cron Task:
22. Thats it!
If you want to kick off the job manually, login as root on the server and do
$/mnt/JailSSD/apps/clamav/run_clamav_scan.sh "scan target folder name"
**** 'scan target folder name' as defined within the clamav jail scantarget or use the root folder name and append subfolder to limit the scan"
IF you dont what the keep the root access to clamav jail
1. edit /etc/ssh/sshd_config and unhash PermitRootLogin and set it to "no" do the same with PasswordAuthentication and set the flag to "no"
2. do
$sysrc sshd_enable=no
7. do
$service sshd restart
let me know if I missed something - Works pretty good for me, but noticed some issues when scanning large content *memory and timeout issues*, but this has nothing to do with the overall setup as far as I can see
Last edited:
