I'm trying to convert our NAS to being fully encrypted and it would seem I'm missing a clue or a step somewhere. To test with, I've got a server that I can blow away the ZFS volume as many times as I choose...
To start with, the server boots and runs off a ZFS mirror (ada0p2/ada1p2) and I'm trying to create an encrypted ZFS volume on da0-da7
If I create a ZFS volume through the web interface, I have "tank" using da0p2 - da7p2.
If I then follow these steps:
(putting a
I can no longer bring the offline'd volume back:
of note:
It would seem that the
Now if I do:
... it works but I'm no longer working with the UUID.
Is there a better way to do this?
To start with, the server boots and runs off a ZFS mirror (ada0p2/ada1p2) and I'm trying to create an encrypted ZFS volume on da0-da7
If I create a ZFS volume through the web interface, I have "tank" using da0p2 - da7p2.
If I then follow these steps:
zpool offline tank gptid/UUID-da0p2 geli init -B /boot/da0p2.eli -e AES-XTS -K /boot/storage.key -l 256 -s 4096 /dev/da0p2(putting a
geli restore in here makes no difference to the outcome) geli attach -k /boot/storage.key /dev/da0p2I can no longer bring the offline'd volume back:
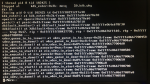
Code:
zpool online tank gptid/UUID-da0p2 warning: device '/dev/gptid/UUID-da0p2' onlined, but remains in faulted state use 'zpool replace' to replace devices that are no longer present
of note:
Code:
glabel status | grep gptid/UUID-da0p2 | wc -l 0
It would seem that the
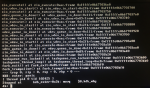
geli attach makes it otherwise impossible to get to the disk:Code:
zpool labelclear /dev/da0p2 failed to open /dev/da0p2: Operation not permitted
Now if I do:
zpool replace tank gptid/UUID-da0p2 /dev/da0p2.eli... it works but I'm no longer working with the UUID.
Is there a better way to do this?
Last edited by a moderator: