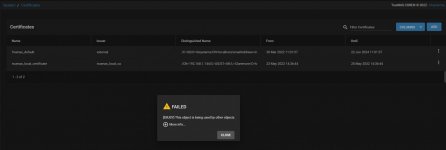
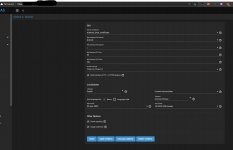
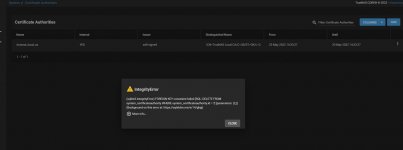
I'm new to networking and NAS, and been wrestling with TrueNAS for weeks on end now. I got a critical error related to the GUI SSL Certificate (something about not having a self signed key or something), so I went looking for a solution. There are a lot of posts relative to this subject in general, but so many are with old versions of FreeNAS and many were way too technical for me to follow. I found one where someone made their own dummy CA and Certificate to get rid of the error so I tried doing that, but now I can't get HTTPS to work and the system won't let me delete the dummy CA and Certificate I made.
I'm just trying to run a home network storage server to give me some storage space for my M1 macbook air that only has a 512 GB drive in it. I pretty worried about my NAS being secure now and would really appreciate it if someone would be willing to help talk me through getting myself out of the mess I've created and get my HTTPS working again. I'll attach some screenshots that might help understanding my mess.
I'm not a programmer, but I've been a computer user since the commodore 64 came out and building my own desktop PC's sense then. When it comes to networking, I have a lot to learn and I'm trying. Just need a helping hand so I can get my home NAS secure again. I really don't understand how certificates work and what they do. I've been looking on the internet, but not finding much on it. Looking at "Lets Encrypt" certificates as I've seen some threads on it just to learn, but I don't think it relates to my problem right now.
I'm just trying to run a home network storage server to give me some storage space for my M1 macbook air that only has a 512 GB drive in it. I pretty worried about my NAS being secure now and would really appreciate it if someone would be willing to help talk me through getting myself out of the mess I've created and get my HTTPS working again. I'll attach some screenshots that might help understanding my mess.
I'm not a programmer, but I've been a computer user since the commodore 64 came out and building my own desktop PC's sense then. When it comes to networking, I have a lot to learn and I'm trying. Just need a helping hand so I can get my home NAS secure again. I really don't understand how certificates work and what they do. I've been looking on the internet, but not finding much on it. Looking at "Lets Encrypt" certificates as I've seen some threads on it just to learn, but I don't think it relates to my problem right now.