consulvation
Cadet
- Joined
- Aug 28, 2020
- Messages
- 2
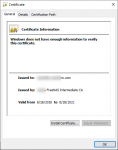
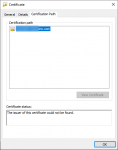
Ever since FreeNAS-11.3-U4.1, we are no longer able to issue valid certificates signed by the server. We had no issues do this prior to the upgrade. We can issue a new cert and it seems to get signed by our own intermediary CA and then we export the cert. It include the full cert chain in pem format and it appears to be in the correct order. It has 3 certs, target, then intermediary and then root. Wherever we install the cert, the browser comes back with an invalid CA error. If we try to open the cert in Windows, it cannot find the intermediary or root certs and marks it invalid.
We tried creating new CAs after the upgrade and signing new certs using the new CAs with the same results. It seems like something in the stored cert or export is failing to link the signers together with the cert being issued.
There are no CSRs involved, this is an "Internal Certificate".
The original CA certs are distributed to all the client devices and this has been working for years.
I am including some screenshots from what Windows sees.
Thanks for any assistance.
We tried creating new CAs after the upgrade and signing new certs using the new CAs with the same results. It seems like something in the stored cert or export is failing to link the signers together with the cert being issued.
There are no CSRs involved, this is an "Internal Certificate".
The original CA certs are distributed to all the client devices and this has been working for years.
I am including some screenshots from what Windows sees.
Thanks for any assistance.