mtuttle007
Cadet
- Joined
- Feb 8, 2022
- Messages
- 2
I'm new to TrueNAS running Scale 22.02-RC.2 and trying to understand how to setup ACL permissions on a dataset that is ultimately shared through a SMB share using the purpose "Default share parameters".
To simplify I have 2 local users setup in TrueNAS with the "Microsoft Account" option set to true on both. Both are part of the same group that has full permissions to my "shared" dataset. When I first set the permissions and copy all of my files over everything works fine.
The issue I'm having is when user A creates a file in my "shared" dataset only user A can open or modify the file. If I look at the permissions on the new file the owner is only set to whoever create the file (user A or B). The group permissions aren't being applied for whatever reason. If I set the permission recursively on my "shared" dataset again that fixes the permission issue. It's almost like I have a umask issue somehow.
The attached screenshots hopefully provide further clarification. If you could point me in the right direction I would appreciate it.
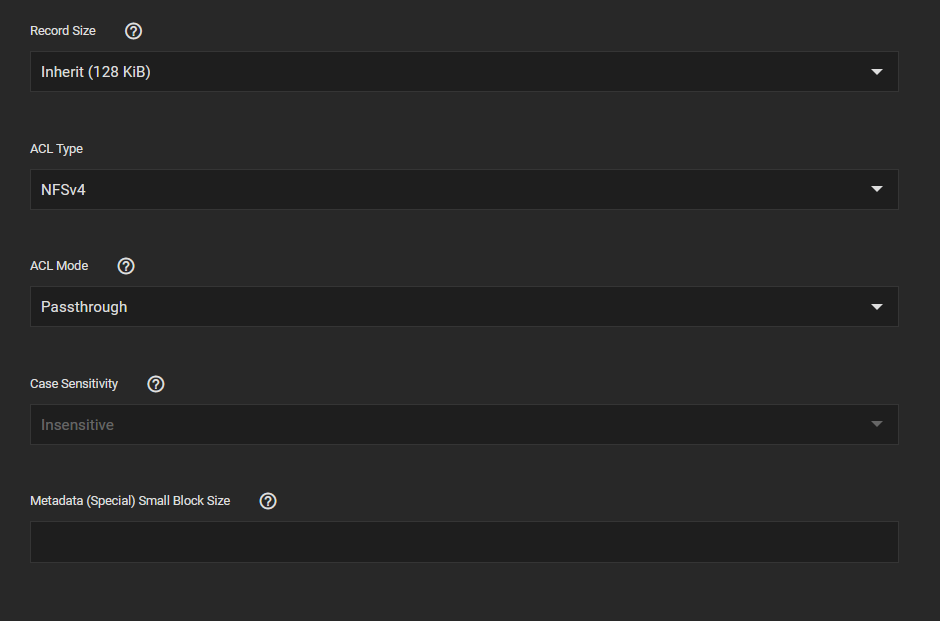
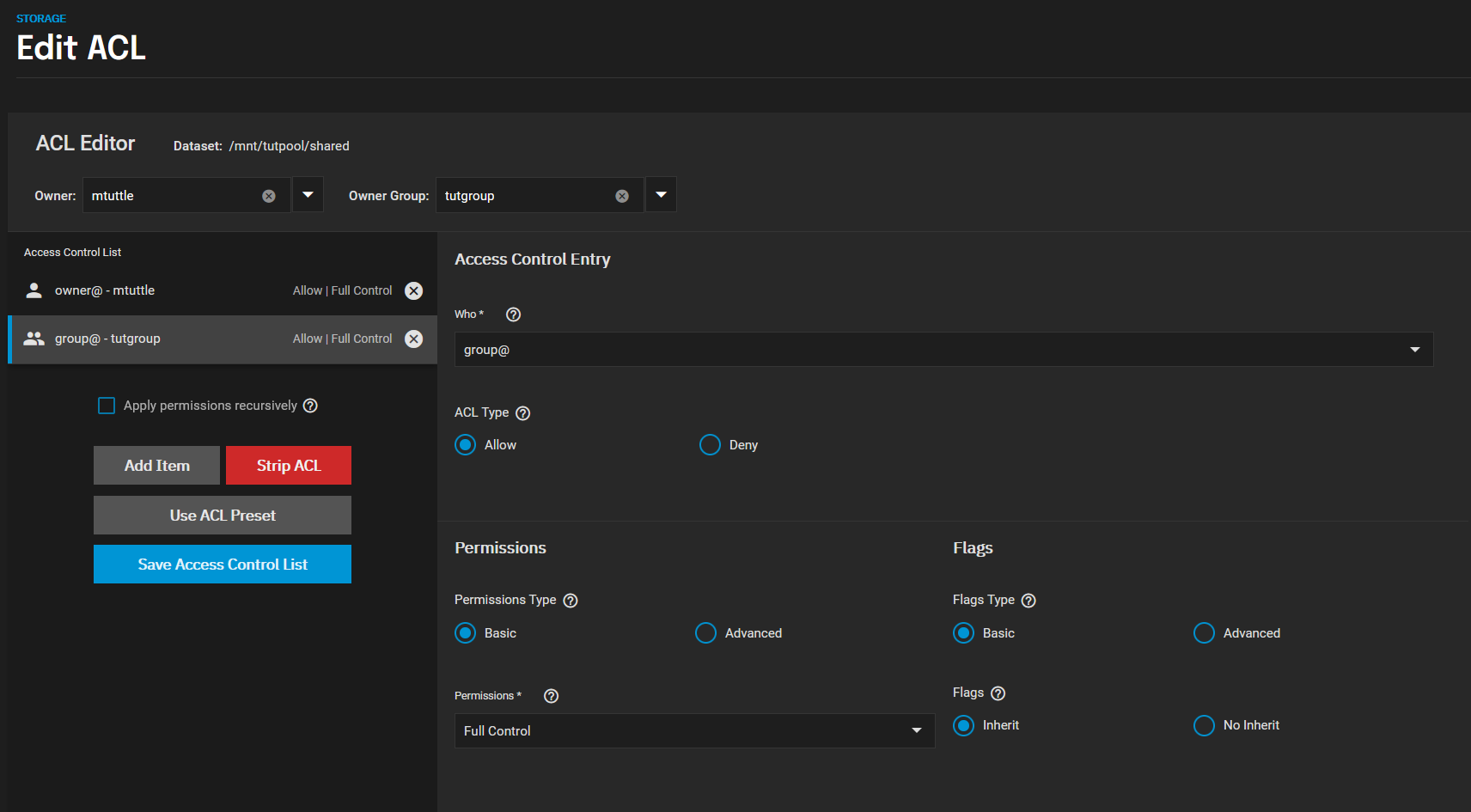
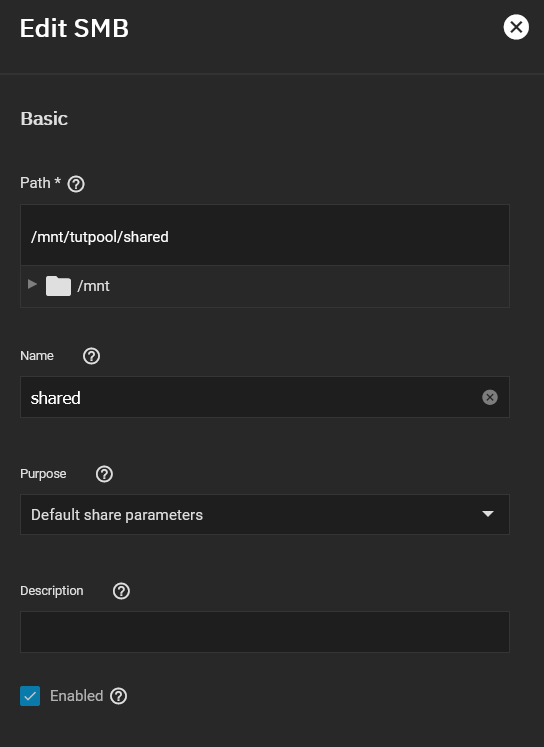
-Matt
To simplify I have 2 local users setup in TrueNAS with the "Microsoft Account" option set to true on both. Both are part of the same group that has full permissions to my "shared" dataset. When I first set the permissions and copy all of my files over everything works fine.
The issue I'm having is when user A creates a file in my "shared" dataset only user A can open or modify the file. If I look at the permissions on the new file the owner is only set to whoever create the file (user A or B). The group permissions aren't being applied for whatever reason. If I set the permission recursively on my "shared" dataset again that fixes the permission issue. It's almost like I have a umask issue somehow.
The attached screenshots hopefully provide further clarification. If you could point me in the right direction I would appreciate it.
-Matt
