The new web GUI in the 11.2 doesn't work when behind an nginx reverse proxy server :
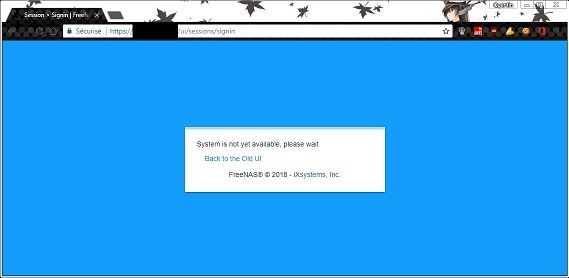
maybe there's something to configure in either freenas or nginx, but i have no clue what
Web GUI works fine when accessed directly from its IP.
both Nginx and freenas are set up with SSL with the exact same certificate from letsencrypt
this is what my nginx.conf looks like for the freenas part :
maybe there's something to configure in either freenas or nginx, but i have no clue what
Web GUI works fine when accessed directly from its IP.
both Nginx and freenas are set up with SSL with the exact same certificate from letsencrypt
this is what my nginx.conf looks like for the freenas part :
Code:
# HTTP server
server {
listen 80;
listen [::]:80;
server_name XXXXXXXXXX;
location /.well-known {
alias /usr/local/www/freenas_stub/.well_known;
}
location / {
return 301 https://XXXXXXXX;
}
}
# HTTPS server
server {
listen 443 ssl;
listen [::]:443 ssl;
server_name XXXXXXX;
ssl on;
ssl_certificate /usr/local/etc/letsencrypt/live/XXXXXXXXX/fullchain.pem;
ssl_certificate_key /usr/local/etc/letsencrypt/live/XXXXXXXXXX/privkey.pem;
ssl_session_timeout 1d;
ssl_session_cache shared:SSL:50m;
ssl_session_tickets off;
ssl_protocols TLSv1.2;
ssl_ciphers 'ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-SHA384:ECDHE-RS
A-AES256-SHA384:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA256';
ssl_prefer_server_ciphers on;
ssl_stapling on;
ssl_stapling_verify on;
location / {
proxy_pass https://192.168.1.40:443;
proxy_http_version 1.1;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header Host $http_host;
proxy_set_header X-Forwarded-Proto https;
proxy_redirect off;
proxy_ssl_certificate /usr/local/etc/letsencrypt/live/XXXXXXXX/fullchain.pem;
proxy_ssl_certificate_key /usr/local/etc/letsencrypt/live/XXXXXXXX/privkey.pem;
}
}
