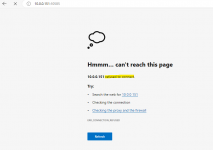
I'm new to truenas scale and kubernetes so bear with me.
I want to install Webnut from the truecharts catalog. I set the following variables to match my UP setup in truenas:
UPS User
UPS Password
UPS Host
UPS Port
The app seems to deploy fine but when i want to open it in a web browser the connection times out and nothing loads.
After some research i found the truechart's installation notes for this app where they indicate
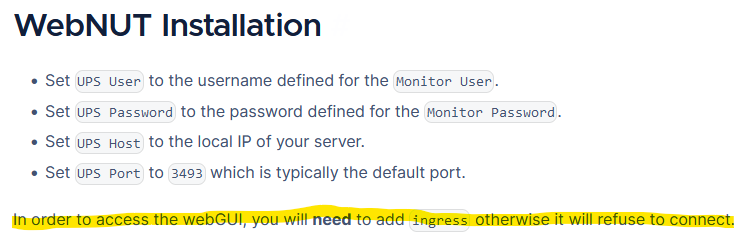
This would explain why it does not load. Do any of you know how to set up "Ingress" in this app to make it work?
My understanding is that this is a way of using traefik as a reverse proxy for this application but i would like to avoid doing this if possible as i already use a different reverse proxy for all my other apps (HAProxy in PFSense). Having to pay attention to 2 reverse proxies would be less than ideal for me.
Any help on this would be greatly appreciated.
I want to install Webnut from the truecharts catalog. I set the following variables to match my UP setup in truenas:
UPS User
UPS Password
UPS Host
UPS Port
The app seems to deploy fine but when i want to open it in a web browser the connection times out and nothing loads.
After some research i found the truechart's installation notes for this app where they indicate
This would explain why it does not load. Do any of you know how to set up "Ingress" in this app to make it work?
My understanding is that this is a way of using traefik as a reverse proxy for this application but i would like to avoid doing this if possible as i already use a different reverse proxy for all my other apps (HAProxy in PFSense). Having to pay attention to 2 reverse proxies would be less than ideal for me.
Any help on this would be greatly appreciated.