I'm no longer using the Smallstep CA for TrueNAS. But if I were, I think I'd abandon the ACME authenticator and instead do this:
- Get a cert at the CLI using the normal
step certificate command, validate with the standard provisioner password.
- Deploy it to TrueNAS using my deploy-freenas script.
- Set a cron job every 8-12 hours to call a script in which you'd:
- Renew the cert using
step certificate renew
- Call
deploy-freenas to deploy it to TrueNAS
Thank you!
However I did not manage to get the script running. Can you please help me. I guess I did not understand the config-file correctly
I made the following steps:
1. installed tinyca on a pi
according to
Let's make a tiny, standalone CA! We'll use a Raspberry Pi 4, YubiKey 5 NFC, and Infinite Noise TRNG.

smallstep.com
2. installed pi-hole as app under truenas scale
and added the follwoing dns entries for:
tinyca -> tinyca.lan.internal
truenas -truenas.lan internal
3. Installed acme.sh on my truenas server in /home/admin/.acme.sh according to:
A pure Unix shell script implementing ACME client protocol - acmesh-official/acme.sh

github.com
with
curl
https://get.acme.sh | sh -s email=
nestor@na.na
I made no further configuration.
4. installed deploy-freenas in truenas asscoding to
Python script to automate deploying TLS certificates to TrueNAS servers - danb35/deploy-freenas

github.com
with
git clone
https://github.com/danb35/deploy-freenas
6. copied the content of
root_ca.cert
and
intermediate_ca.crt
which were generated with smallstep on m pi in /mnt/ca/certs
(including lines "--- BEGIN..." and " ---END ...") into a file with filename
fullchain.cer
7. moved fullchain.cer to /home/admin/.acme.sh/tinyca.lan.internal/fullchain.cer in truenas
8. configured deploy_config
# Configuration file for deploy_freenas.py
as follows:
[deploy]
# Choose one of the following authentication methods, "api_key" or "password" (comment out the other one).
# Auth via API keys is highly recommended, but is only available from TrueNAS (Core) 12.0 up.
# You can generate a new API key in the web interface under "Settings" (upper right) > "API Keys".
api_key = xxxxxxxxx api key generated in truenas xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx
# If you are on FreeNAS 11 or lower, set this to your FreeNAS root password
# password = YourSuperSecurePassword#@#$*
# Everything below here is optional
# cert_fqdn specifies the FQDN used for your certificate. Default is your system hostname
cert_fqdn = truenas.lan.internal
# connect_host specifies the hostname the script should attempt to connect to, to deploy the cert.
# Default is localhost (assuming the script is running on your FreeNAS box)
connect_host = tinyca.lan.internal
# verify sets whether the script will attempt to verify the server's certificate with a HTTPS
# connection. Set to true if you're using a HTTPS connection to a remote host. If connect_host
# is set to localhost (or is unset), set to false. Default is false.
# verify = false
# privkey_path is the path to the certificate private key on your system. Default
# assumes you're using acme.sh:
# /root/.acme.sh/cert_fqdn/cert_fqdn.key or /root/.acme.sh/cert_fqdn_ecc/cert_fqdn.key
privkey_path = /home/admin/.acme.sh/truenas.lan.internal_ecc/truenas.lan.internal.key
# fullchain_path is the path to the full chain (leaf cert + intermediate certs)
# on your system. Default assumes you're using acme.sh:
# /root/.acme.sh/cert_fqdn/fullchain.cer or /root/.acme.sh/cert_fqdn_ecc/fullchain.cer
fullchain_path = /home/admin/.acme.sh/tinyca.lan.internal/fullchain.cer
# protocol sets the connection protocol, http or https. Include '://' at the end.
# Default is http
# protocol = https://
# port sets the port to use to connect. Default is 80. If protocol is https,
# this MUST be set to your https port.
# port = 443
# set ui_certificate_enabled to false if you want to skip using the new cerificate for the UI. Default is true.
# ui_certificate_enabled = false
# set s3_enabled to true if you have the S3 service enabled on your FreeNAS. Default is false.
# s3_enabled = true
# set ftp_enabled to true if you have the FTP service enabled on your FreeNAS. Default is false.
# ftp_enabled = true
# set webdav_enabled to true if you have the WEBDAV service enabled on your FreeNAS. Default is false.
# webdav_enabled = true
# set apps_enabled to true if you want to update your TrueNAS SCALE chart applications to use the new certificate. Default is false.
# apps_enabled = true
# only update TrueNAS SCALE chart applications where the san of the current and the new cert matches. Default is false.
#apps_only_matching_san = true
# Certificates will be given a name with a timestamp, by default it will be
# letsencrypt-yyyy-mm-dd-hhmmss. You can change the first part if you like.
# cert_base_name = something_else
9.
Where do I find the truenas.lan.internal.key? Is this identical with the file localhost.key generated with smallstep???
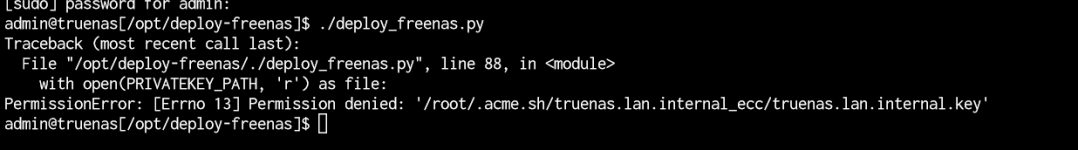
As I have no such file I generated and empty file with touch /home/admin/.acme.sh/truenas.lan.internal_ecc/truenas.lan.internal.key
10. Starting deploy_freenas.py
I get the following error message:
admin@truenas[/opt/deploy-freenas]$ ./deploy_freenas.py
Traceback (most recent call last):
File "/usr/lib/python3/dist-packages/urllib3/connection.py", line 169, in _new_conn
conn = connection.create_connection(
File "/usr/lib/python3/dist-packages/urllib3/util/connection.py", line 96, in create_connection
raise err
File "/usr/lib/python3/dist-packages/urllib3/util/connection.py", line 86, in create_connection
sock.connect(sa)
ConnectionRefusedError: [Errno 111] Connection refused
During handling of the above exception, another exception occurred:
Traceback (most recent call last):
File "/usr/lib/python3/dist-packages/urllib3/connectionpool.py", line 699, in urlopen
httplib_response = self._make_request(
File "/usr/lib/python3/dist-packages/urllib3/connectionpool.py", line 394, in _make_request
conn.request(method, url, **httplib_request_kw)
File "/usr/lib/python3/dist-packages/urllib3/connection.py", line 234, in request
super(HTTPConnection, self).request(method, url, body=body, headers=headers)
File "/usr/lib/python3.9/http/client.py", line 1255, in request
self._send_request(method, url, body, headers, encode_chunked)
File "/usr/lib/python3.9/http/client.py", line 1301, in _send_request
self.endheaders(body, encode_chunked=encode_chunked)
File "/usr/lib/python3.9/http/client.py", line 1250, in endheaders
self._send_output(message_body, encode_chunked=encode_chunked)
File "/usr/lib/python3.9/http/client.py", line 1010, in _send_output
self.send(msg)
File "/usr/lib/python3.9/http/client.py", line 950, in send
self.connect()
File "/usr/lib/python3/dist-packages/urllib3/connection.py", line 200, in connect
conn = self._new_conn()
File "/usr/lib/python3/dist-packages/urllib3/connection.py", line 181, in _new_conn
raise NewConnectionError(
urllib3.exceptions.NewConnectionError: <urllib3.connection.HTTPConnection object at 0x7f9006f5daf0>: Failed to establish a new connection: [Errno 111] Connection refused
During handling of the above exception, another exception occurred:
Traceback (most recent call last):
File "/usr/lib/python3/dist-packages/requests/adapters.py", line 439, in send
resp = conn.urlopen(
File "/usr/lib/python3/dist-packages/urllib3/connectionpool.py", line 755, in urlopen
retries = retries.increment(
File "/usr/lib/python3/dist-packages/urllib3/util/retry.py", line 574, in increment
raise MaxRetryError(_pool, url, error or ResponseError(cause))
urllib3.exceptions.MaxRetryError: HTTPConnectionPool(host='tinyca.lan.internal', port=80): Max retries exceeded with url: /api/v2.0/certificate/ (Caused by NewConnectionError('<urllib3.connection.HTTPConnection object at 0x7f9006f5daf0>: Failed to establish a new connection: [Errno 111] Connection refused'))
During handling of the above exception, another exception occurred:
Traceback (most recent call last):
File "/opt/deploy-freenas/./deploy_freenas.py", line 97, in <module>
r = session.post(
File "/usr/lib/python3/dist-packages/requests/sessions.py", line 590, in post
return self.request('POST', url, data=data, json=json, **kwargs)
File "/usr/lib/python3/dist-packages/requests/sessions.py", line 542, in request
resp = self.send(prep, **send_kwargs)
File "/usr/lib/python3/dist-packages/requests/sessions.py", line 655, in send
r = adapter.send(request, **kwargs)
File "/usr/lib/python3/dist-packages/requests/adapters.py", line 516, in send
raise ConnectionError(e, request=request)
requests.exceptions.ConnectionError: HTTPConnectionPool(host='tinyca.lan.internal', port=80): Max retries exceeded with url: /api/v2.0/certificate/ (Caused by NewConnectionError('<urllib3.connection.HTTPConnection object at 0x7f9006f5daf0>: Failed to establish a new connection: [Errno 111] Connection refused'))
admin@truenas[/opt/deploy-freenas]$
Best regards,
Nestor

 smallstep.com
smallstep.com

 www.truenas.com
www.truenas.com
 www.truenas.com
www.truenas.com