obsidiangroup
Dabbler
- Joined
- Oct 4, 2022
- Messages
- 19
Did anything else change from 2.2.2 to 2.3.0? WIth 2.2.2, I have my TrueCommand working behind a nginx reverse proxy server, running with no issues. Websocket support is enabled. After upgrading to 2.3.0, can no longer access TrueCommand via reverse proxy.
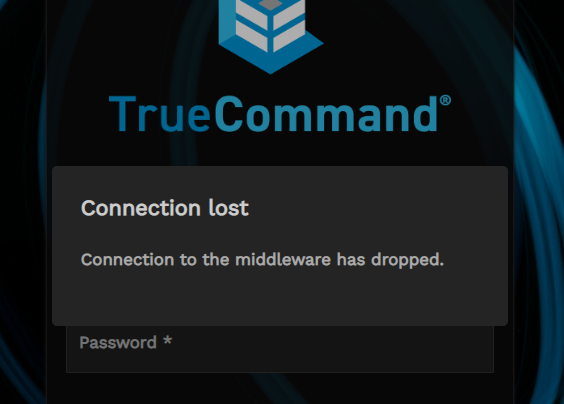
If you go to https://truecommand.domain.com, it sends the request to https://truecommand.domain.com/auth, which then displays:
Watching the logs for TrueCommand, the only thing I noticed was:
And my reverse proxy logs:
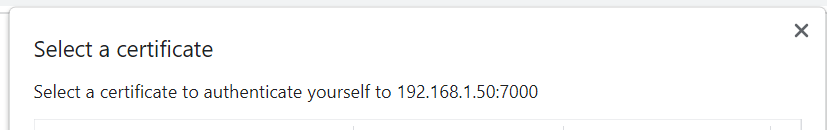
However, from my nginx container, I can access the host with no problems. It seems to be an issue with SSL certificates, as attempting to access the page via https://IP:7000 (Port forwarded to 443), I'm prompted to select a certificate to authenticate with:
 .
.
Rolling back to 2.2.2, these problems are gone.
If you go to https://truecommand.domain.com, it sends the request to https://truecommand.domain.com/auth, which then displays:
Watching the logs for TrueCommand, the only thing I noticed was:
Code:
==> caddy.log <==
{"level":"warn","ts":1674762991.5564384,"logger":"tls","msg":"YOUR SERVER MAY BE VULNERABLE TO ABUSE: on-demand TLS is enabled, but no protections are in place","docs":"https://caddyserver.com/docs/automatic-https#on-demand-tls"}
{"level":"info","ts":1674762991.5566363,"logger":"tls","msg":"cleaning storage unit","description":"FileStorage:/data/.caddy/data/caddy"}
{"level":"info","ts":1674762991.5584602,"logger":"tls","msg":"finished cleaning storage units"}
{"level":"info","ts":1674762991.5589929,"logger":"http","msg":"enabling HTTP/3 listener","addr":":443"}
{"level":"info","ts":1674762991.5592604,"logger":"http.log","msg":"server running","name":"srv0","protocols":["h1","h2","h3"]}
{"level":"info","ts":1674762991.5593576,"logger":"http.log","msg":"server running","name":"srv1","protocols":["h1","h2","h3"]}
{"level":"info","ts":1674762991.5616798,"msg":"autosaved config (load with --resume flag)","file":"/data/.caddy/config/caddy/autosave.json"}
{"level":"info","ts":1674762991.5617027,"msg":"serving initial configuration"}
{"level":"info","ts":1674762991.5620532,"logger":"watcher","msg":"watching config file for changes","config_file":"/etc/CaddyFile"}
{"level":"warn","ts":1674762991.7860959,"logger":"tls","msg":"stapling OCSP","error":"no OCSP stapling for [172.17.0.2]: no OCSP server specified in certificate","identifiers":["172.17.0.2"]}
And my reverse proxy logs:
Code:
2023/01/26 14:33:35 [error] 474#474: *2779 connect() failed (111: Connection refused) while connecting to upstream, client: 192.168.20.202, server: trucommand.domain.co, request: "GET /websocket HTTP/1.1", upstream: "https://192.168.1.50:7000/websocket", host: "truecommand.domain.co" 2023/01/26 14:33:36 [error] 474#474: *2795 connect() failed (111: Connection refused) while connecting to upstream, client: 192.168.20.202, server: trucommand.domain.co, request: "GET /websocket HTTP/1.1", upstream: "https://192.168.1.50:7000/websocket", host: "truecommand.domain.co" [26/Jan/2023:15:02:23 -0500] - 421 421 - GET https truecommand.domain.co "/websocket" [Client 192.168.20.202] [Length 0] [Gzip -] [Sent-to 192.168.1.50] "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/108.0.0.0 Safari/537.36" "-" [26/Jan/2023:15:02:26 -0500] - 421 421 - GET https truecommand.domain.co "/websocket" [Client 192.168.20.202] [Length 0] [Gzip -] [Sent-to 192.168.1.50] "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/108.0.0.0 Safari/537.36" "-"
However, from my nginx container, I can access the host with no problems. It seems to be an issue with SSL certificates, as attempting to access the page via https://IP:7000 (Port forwarded to 443), I'm prompted to select a certificate to authenticate with:
Rolling back to 2.2.2, these problems are gone.