blahhumbug
Dabbler
- Joined
- Apr 25, 2015
- Messages
- 22
I've been running various FreeNAS plugins that support HTTPS through the Qualsys SSL Labs checker at https://www.ssllabs.com/ssltest/analyze.html
Most of the plugins are supporting vulnerable protocols on a default install. The only plugin I've been able to reasonable secure so far is the OwnCloud plugin since all of the SSL configuration was easily changed by reconfiguring Apache 2.4 settings. The only thing I wasn't able to resolve for OwnCloud yet is TLS_FALLBACK_SCSV support which needs Openssl 0.9.8zc or newer, but it looks like most FreeNas plugins are using OpenSSL 0.9.8za. But this is not critical as I have shut off most of the older protocols anyway.
However, for Headphones since it acts as its own webserver, I am not sure how to start on securing it, and whether the issues are in Headphones code itself, or in any of the libraries it uses (CherryPy, pyOpenssl, etc). I'm hoping that I might be able to do a sidegrade and upgrade some python libraries without having to muck with Headphones code.
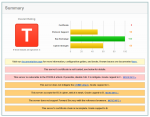
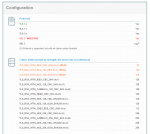
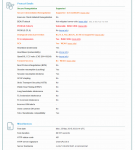
Attached are three screencaptures of the Qualsys report for Headphones. The main issues are:
* Vulnerable to CRIME attack. Need to shut off TLS compression
* Accepts weak ciphers: TLS_RSA_WITH_DES_CBC_SHA, TLS_RSA_WITH_RC4_128_MD5, TLS_RSA_WITH_RC4_128_SHA
* Does not support Forward Secrecy
* Vulnerable to POODLE (Need to disable SSLv3 support)
* Vulnerable to DoS attacks due to Client-Initiated renegotation support
Does anyone have recommendations on where to begin in resolving any of these issues, especially disabling SSLv3, RC4, and TLS compression?
Most of the plugins are supporting vulnerable protocols on a default install. The only plugin I've been able to reasonable secure so far is the OwnCloud plugin since all of the SSL configuration was easily changed by reconfiguring Apache 2.4 settings. The only thing I wasn't able to resolve for OwnCloud yet is TLS_FALLBACK_SCSV support which needs Openssl 0.9.8zc or newer, but it looks like most FreeNas plugins are using OpenSSL 0.9.8za. But this is not critical as I have shut off most of the older protocols anyway.
However, for Headphones since it acts as its own webserver, I am not sure how to start on securing it, and whether the issues are in Headphones code itself, or in any of the libraries it uses (CherryPy, pyOpenssl, etc). I'm hoping that I might be able to do a sidegrade and upgrade some python libraries without having to muck with Headphones code.
Attached are three screencaptures of the Qualsys report for Headphones. The main issues are:
* Vulnerable to CRIME attack. Need to shut off TLS compression
* Accepts weak ciphers: TLS_RSA_WITH_DES_CBC_SHA, TLS_RSA_WITH_RC4_128_MD5, TLS_RSA_WITH_RC4_128_SHA
* Does not support Forward Secrecy
* Vulnerable to POODLE (Need to disable SSLv3 support)
* Vulnerable to DoS attacks due to Client-Initiated renegotation support
Does anyone have recommendations on where to begin in resolving any of these issues, especially disabling SSLv3, RC4, and TLS compression?